/1 Sin #4: Insufficient AD Hardening
Of course, there are many AD attack paths, misconfigurations, and ways to get DA credentials.
But still, companies should try to set the bar as high as possible to force attackers to make mistakes we might detect.
🧵 #CyberSecurity
Of course, there are many AD attack paths, misconfigurations, and ways to get DA credentials.
But still, companies should try to set the bar as high as possible to force attackers to make mistakes we might detect.
🧵 #CyberSecurity
2/ Passwords in the GPO
My first "Real-World #PingCastle Finding" talks exactly about this issue:

My first "Real-World #PingCastle Finding" talks exactly about this issue:
https://twitter.com/malmoeb/status/1451055513131790338

3/ Service accounts are DA
Service accounts should never be part of the Domain Admins group.
Check and clean the DA group regularly because a TA could try to "Kerberoast" the service account, which is primarily a problem if the service account use a weak password (next point).
Service accounts should never be part of the Domain Admins group.
Check and clean the DA group regularly because a TA could try to "Kerberoast" the service account, which is primarily a problem if the service account use a weak password (next point).

4/ Old passwords
All these accounts are part of the Domain Admins group. The passwords were last changed almost 20 years ago - you can imagine the password strength.
These passwords could probably be cracked very quickly to get the highest privileges on the network.
All these accounts are part of the Domain Admins group. The passwords were last changed almost 20 years ago - you can imagine the password strength.
These passwords could probably be cracked very quickly to get the highest privileges on the network.

5/ No tiering model
As soon as we have a forensic agent in the network (e.g., during a compromise assessment), we check if DA's or highly privileged accounts log in to normal clients (which can be analyzed well with the event logs on the clients and servers).
As soon as we have a forensic agent in the network (e.g., during a compromise assessment), we check if DA's or highly privileged accounts log in to normal clients (which can be analyzed well with the event logs on the clients and servers).
6/ There are many ways attackers can grab a password from a compromised machine, which is why a clean tiering model, possibly with local firewall rules and hardening policies, should be used to prevent users and admins from logging in to all clients and servers.
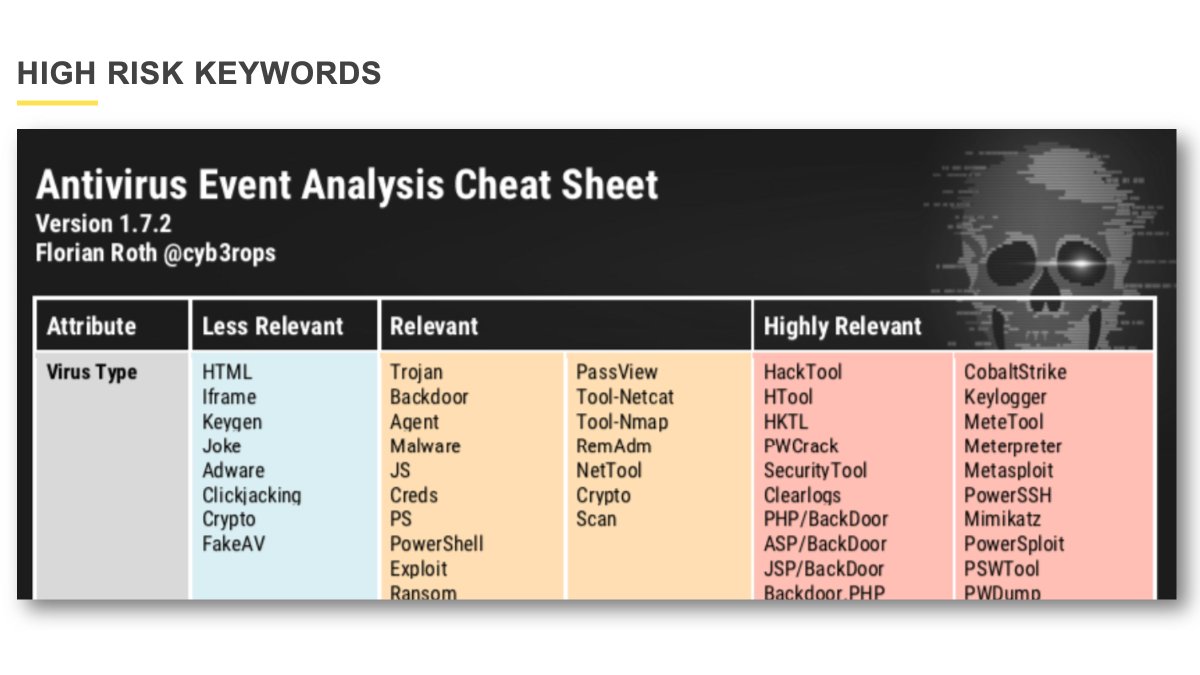
Image from [1].
Image from [1].

8/ Of course, as mentioned at the beginning, there are dozens of other ways a Windows domain can be compromised.
But we all have to start somewhere, don't we?
Good luck 🍀
But we all have to start somewhere, don't we?
Good luck 🍀
• • •
Missing some Tweet in this thread? You can try to
force a refresh