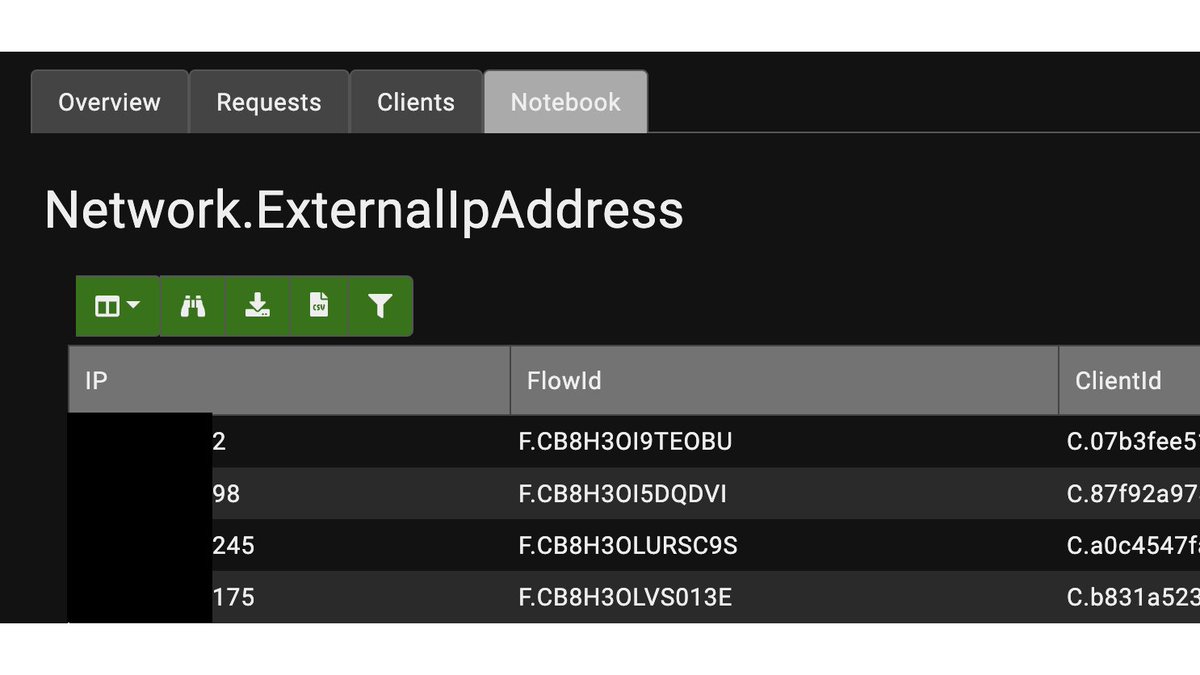
1/ Although Windows logs the creation of new services in the SYSTEM event log (Event ID 7045 - New Service was installed), attackers often delete these logs.
But we can use the Windows Firewall event logs for #ThreatHunting new installations (of backdoors) 🧵
#CyberSecurity
But we can use the Windows Firewall event logs for #ThreatHunting new installations (of backdoors) 🧵
#CyberSecurity

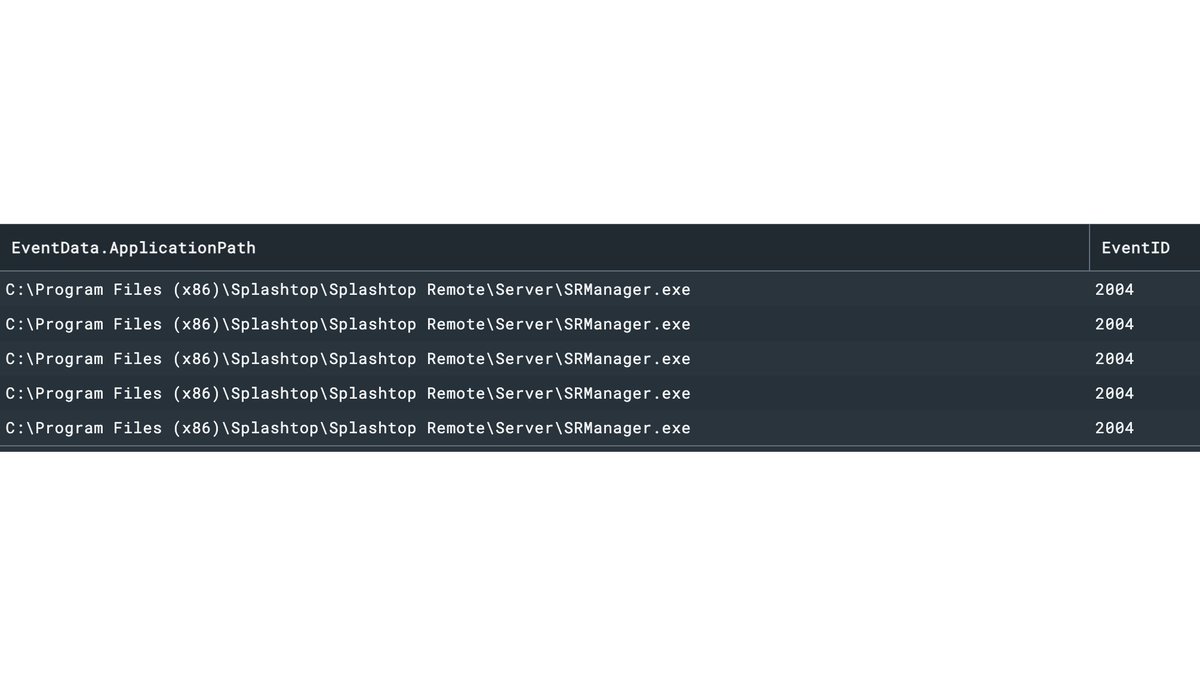
2/ The screenshot above shows the 2004 Event ID (the creation of a new firewall rule).
The screenshot is from an actual case where the attacker installed Splashtop as a backdoor (among others) to get back into the network.
The screenshot is from an actual case where the attacker installed Splashtop as a backdoor (among others) to get back into the network.
3/ Using @velocidex Velociraptor and the EvtxHunter Hunt, we can conveniently collect these event logs on all clients and servers in the network. 

4/ Inside the Hunt, we could have specified an IOC (like Splashtop in our case).
Still, it's almost more convenient (at least for me) to collect all the data and filter inside the Velociraptor notebook (here, by the keyword Splashtop, but do not forget about Atera, TW, etc.).
Still, it's almost more convenient (at least for me) to collect all the data and filter inside the Velociraptor notebook (here, by the keyword Splashtop, but do not forget about Atera, TW, etc.).
5/ In the notebook, we are now presented with the selected fields. The installation paths, on which host, and when the new firewall rules were set up.
Even if attackers delete other event logs to cover their tracks, there are still enough logs where we can find traces. 🕵️🥳
Even if attackers delete other event logs to cover their tracks, there are still enough logs where we can find traces. 🕵️🥳
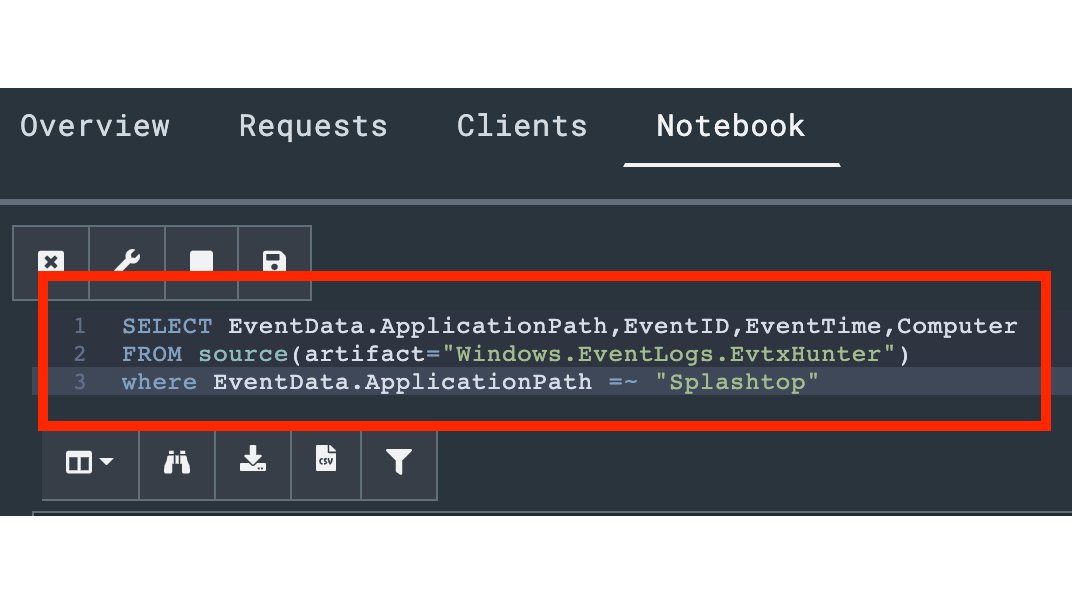
6/ The following query was used in the example:
SELECT EventData.ApplicationPath,EventID,EventTime,Computer FROM source(artifact="Windows.EventLogs.EvtxHunter") where EventData.ApplicationPath =~ "Splashtop"
SELECT EventData.ApplicationPath,EventID,EventTime,Computer FROM source(artifact="Windows.EventLogs.EvtxHunter") where EventData.ApplicationPath =~ "Splashtop"
• • •
Missing some Tweet in this thread? You can try to
force a refresh