
1/ #ThreatHunting for #AsyncRAT
We have various ways to find infected hosts with AsyncRAT:
1⃣ Usage of standard C2 ports
2⃣Hunting for persistence
3⃣Mutexes FTW
4⃣Last but not least, hunting for dropped DLLs
Let's go 🤠🧵
#CyberSecurity
We have various ways to find infected hosts with AsyncRAT:
1⃣ Usage of standard C2 ports
2⃣Hunting for persistence
3⃣Mutexes FTW
4⃣Last but not least, hunting for dropped DLLs
Let's go 🤠🧵
#CyberSecurity
2/ AsyncRAT is a popular Trojan executed at the end of an infection chain on target computers.
@hpsecurity ([2],[3]) and @Trellix ([4]) have both reported in recent reports that TAs have been deploying AsyncRAT.
@hpsecurity ([2],[3]) and @Trellix ([4]) have both reported in recent reports that TAs have been deploying AsyncRAT.
3/ Since the source code of AsyncRAT is publicly available [1], we can obtain a copy to investigate and build detection capabilities for this RAT. 

4/ Three default ports are already populated within the builder, where we can assemble a client (6606, 7707, 8808).
Additionally, the C2 address can be stated, which the client should connect to after a successful infection. It's possible to store the C2 address on Pastebin.
Additionally, the C2 address can be stated, which the client should connect to after a successful infection. It's possible to store the C2 address on Pastebin.

5/ In the analysis of almost 500 AsyncRAT samples from MalwareBazaar (@abuse_ch), the top three ports for the C2 were indeed 6606, 7707, and 8808!
That means that many TAs didn't bother to change the default port within the builder ☝️
Screenshot from [5].
That means that many TAs didn't bother to change the default port within the builder ☝️
Screenshot from [5].

6/ Also, all samples available on Bazaar used a C2 port higher than 1024.
This Information is helpful for targeted hunts within the firewall logs (connections to IP addresses to the Internet on high-ports - beware: may return many hits).
This Information is helpful for targeted hunts within the firewall logs (connections to IP addresses to the Internet on high-ports - beware: may return many hits).
7/ In the builder, you can specify if a persistence should be set up or not.
If the field is checked, we can choose a filename and select the directory where the payload will be saved (per default, only two directories are available).
If the field is checked, we can choose a filename and select the directory where the payload will be saved (per default, only two directories are available).

8/ AsyncRAT uses a mutex to detect already infected systems.
The prefix of the mutex "AsyncMutex_" was also mentioned in @hpsecurity's tweet[6], which again indicates that attackers accept the defaults (which is good for us defenders!).
The prefix of the mutex "AsyncMutex_" was also mentioned in @hpsecurity's tweet[6], which again indicates that attackers accept the defaults (which is good for us defenders!).

9/ Interestingly, we can "clone" the information about the binary from another binary for blending in.
In the example, I took the information from the legitimate PingCastleCloud binary - the builder then uses the same information for the malicious binary.
In the example, I took the information from the legitimate PingCastleCloud binary - the builder then uses the same information for the malicious binary.

11/ Our sample built this way comes straight to a VT score of 48 - anything but unknown, which is also shown by the various YARA hits. 

12/ After running this newly built sample (in the various reports and tweets referenced so far, AsyncRAT is run at the end of an entire infection chain) on our lab machine, we see that our infected machine has reported back to the controller. 

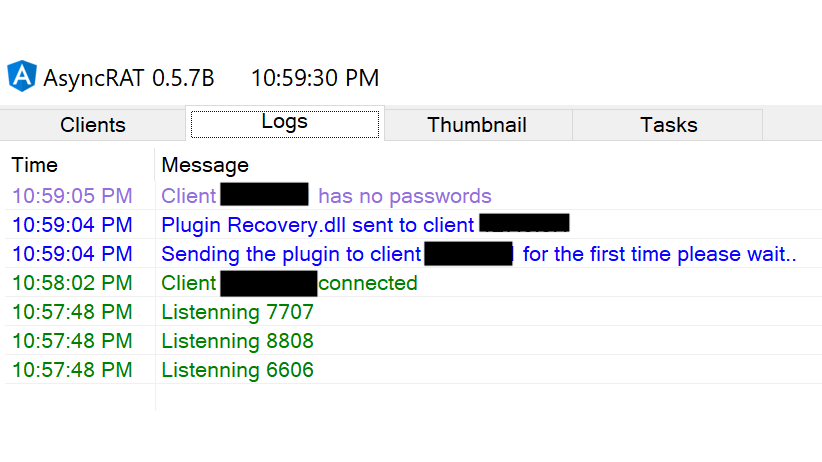
13/ AsyncRAT now has various functions built-in that can be used to further extend the initial access, for example, "Password Recovery".
If the function "Password Recovery" is selected, we see in the logs that a DLL (Recovery.dll) was sent to the client.
If the function "Password Recovery" is selected, we see in the logs that a DLL (Recovery.dll) was sent to the client.
15/ Time for @velocidex Velociraptor 😍
With the MTF-Hunt, we search for the plugin-names on our infected client and find the plugins directly placed under C:\.
All other plugins are stored in this directory (we see the filenames visible in the log (RemoteDesktop.dll, etc.)).
With the MTF-Hunt, we search for the plugin-names on our infected client and find the plugins directly placed under C:\.
All other plugins are stored in this directory (we see the filenames visible in the log (RemoteDesktop.dll, etc.)).

17/ The LimeLogger plugin for recording keyboard strokes works fine, recording all keystrokes on our test machine. 

18/ Using Velociraptor's Mutants-Hunt and the string "AsyncMutex_", we can also find AsyncRAT infected machines. 

19/ AsyncRAT distinguishes between two types of persistence ([7]).
Either the installer is run with admin privileges, in which case a Scheduled Task is created, or a new entry in the Run Key as an unprivileged user. Below is the relevant code.
Either the installer is run with admin privileges, in which case a Scheduled Task is created, or a new entry in the Run Key as an unprivileged user. Below is the relevant code.

20/ In the first example, the sample was installed as an unprivileged user, resulting in a new run key. 

21/ The THOR APT scanner matches the AsyncRAT samples based on the Rule "Reversed String" - the run key within the code used for persistence ([7]).
Probably noisier than stealthier 🤔

Probably noisier than stealthier 🤔


22/ Below is the newly created Scheduled Task (installation with admin rights) - the executable is again placed in AppData\Roaming (one of the two options in the builder). 

23/ By the way, AsyncRAT also can show a UAC prompt to the user to get admin rights.
In my tests, this feature worked well. After confirming the UAC prompt, AsyncRAT had admin rights on the machine.
In my tests, this feature worked well. After confirming the UAC prompt, AsyncRAT had admin rights on the machine.

24/ Sifting through the code, there would be more detection possibilities and keywords to hunt and create alarms.
But with the few indicators presented in this thread, we can hunt for AsyncRAT infections pretty effectively.
Good luck 🍀
But with the few indicators presented in this thread, we can hunt for AsyncRAT infections pretty effectively.
Good luck 🍀
25/ References:
[1] github.com/NYAN-x-CAT/Asy…
[2]
[3] threatresearch.ext.hp.com/stealthy-opend…
[4] trellix.com/en-us/about/ne…
[5] bazaar.abuse.ch/sample/faaddcf…
[6]
[7] github.com/NYAN-x-CAT/Asy…
[1] github.com/NYAN-x-CAT/Asy…
[2]
https://twitter.com/hpsecurity/status/1551917816240128001
[3] threatresearch.ext.hp.com/stealthy-opend…
[4] trellix.com/en-us/about/ne…
[5] bazaar.abuse.ch/sample/faaddcf…
[6]
https://twitter.com/hpsecurity/status/1551918502528880644
[7] github.com/NYAN-x-CAT/Asy…
• • •
Missing some Tweet in this thread? You can try to
force a refresh












