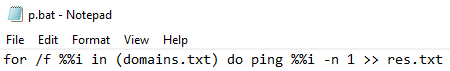
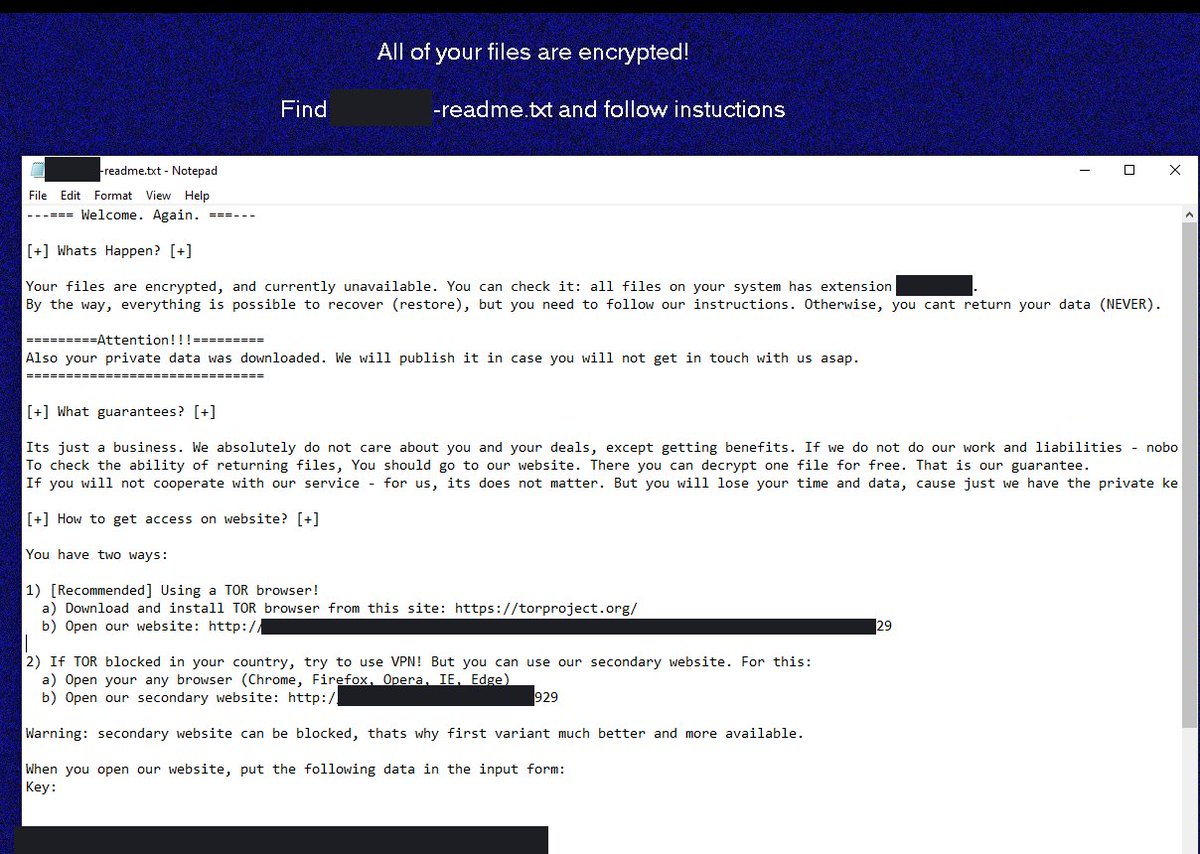
BumbleBee Roasts Its Way to Domain Admin
➡️Initial Access: BumbleBee (zipped ISO /w LNK+DLL)
➡️Persistence: AnyDesk
➡️Discovery: VulnRecon, Seatbelt, AdFind, etc.
➡️Credentials: Kerberoast, comsvcs.dll, ProcDump
➡️C2: BumbleBee, CobaltStrike, AnyDesk
thedfirreport.com/2022/08/08/bum…
➡️Initial Access: BumbleBee (zipped ISO /w LNK+DLL)
➡️Persistence: AnyDesk
➡️Discovery: VulnRecon, Seatbelt, AdFind, etc.
➡️Credentials: Kerberoast, comsvcs.dll, ProcDump
➡️C2: BumbleBee, CobaltStrike, AnyDesk
thedfirreport.com/2022/08/08/bum…
Analysis and reporting completed by @Tornado and @MetallicHack
Shout outs: @threatinsight, Google's Threat Analysis Group, @vladhiewsha, @benoitsevens, @DidierStevens, @malpedia, @k3dg3, @malware_traffic, @Unit42_Intel, @EricRZimmerman, & @svch0st. Thanks ya'll!
Shout outs: @threatinsight, Google's Threat Analysis Group, @vladhiewsha, @benoitsevens, @DidierStevens, @malpedia, @k3dg3, @malware_traffic, @Unit42_Intel, @EricRZimmerman, & @svch0st. Thanks ya'll!
IOC's
#Bumblebee
BC_invoice_Report_CORP_46.zip
6c87ca630c294773ab760d88587667f26e0213a3
142.91.3[.]109:443
45.140.146[.]30:443
#CobaltStrike
fuvataren[.]com
45.153.243[.]142:443
dofixifa[.]co
108.62.12[.]174:443
CS Payload Hosting
hxxp://104.243.33.50:80/a
#Bumblebee
BC_invoice_Report_CORP_46.zip
6c87ca630c294773ab760d88587667f26e0213a3
142.91.3[.]109:443
45.140.146[.]30:443
#CobaltStrike
fuvataren[.]com
45.153.243[.]142:443
dofixifa[.]co
108.62.12[.]174:443
CS Payload Hosting
hxxp://104.243.33.50:80/a
IOCs Continued
document.lnk
58739dc62eeac7374db9a8c07df7c7c36b550ce5
namr.dll
7a3db4b3359b60786fcbdaf0115191502fcded07
VulnRecon.exe
d9832b46dd6f249191e9cbcfba2222c1702c499a
VulnRecon.dll
a204f20b1c96c5b882949b93eb4ac20d4f9e4fdf
document.lnk
58739dc62eeac7374db9a8c07df7c7c36b550ce5
namr.dll
7a3db4b3359b60786fcbdaf0115191502fcded07
VulnRecon.exe
d9832b46dd6f249191e9cbcfba2222c1702c499a
VulnRecon.dll
a204f20b1c96c5b882949b93eb4ac20d4f9e4fdf
Detections
5+ ET Snort/Suricata Rules
20+ Sigma Rules
3 Yara Rules
5+ ET Snort/Suricata Rules
20+ Sigma Rules
3 Yara Rules
• • •
Missing some Tweet in this thread? You can try to
force a refresh