
Today's lab consisted of testing a theory from my @Fortinet NSE4 and NSE5: To connect FortiGates to FortiManager and FortiAnazyler from across the WAN using a VIP.
#THREAD
#HaitianNetworkEngineer
#BlackTechTwitter
#TechTwitter
#FutureCCIE
#NSE5
#Fortinet



#THREAD
#HaitianNetworkEngineer
#BlackTechTwitter
#TechTwitter
#FutureCCIE
#NSE5
#Fortinet




Mapping a specific IP address to another specific IP address is usually called Destination NAT (DNAT). FortiOS calls this a Virtual IP address (VIP). DNAT, or VIP, is are used to map an external IP address to an IP address or address range. 





The mapping can include all TCP/UDP ports or, if port forwarding is enabled, it only refers to the specific configured ports. 

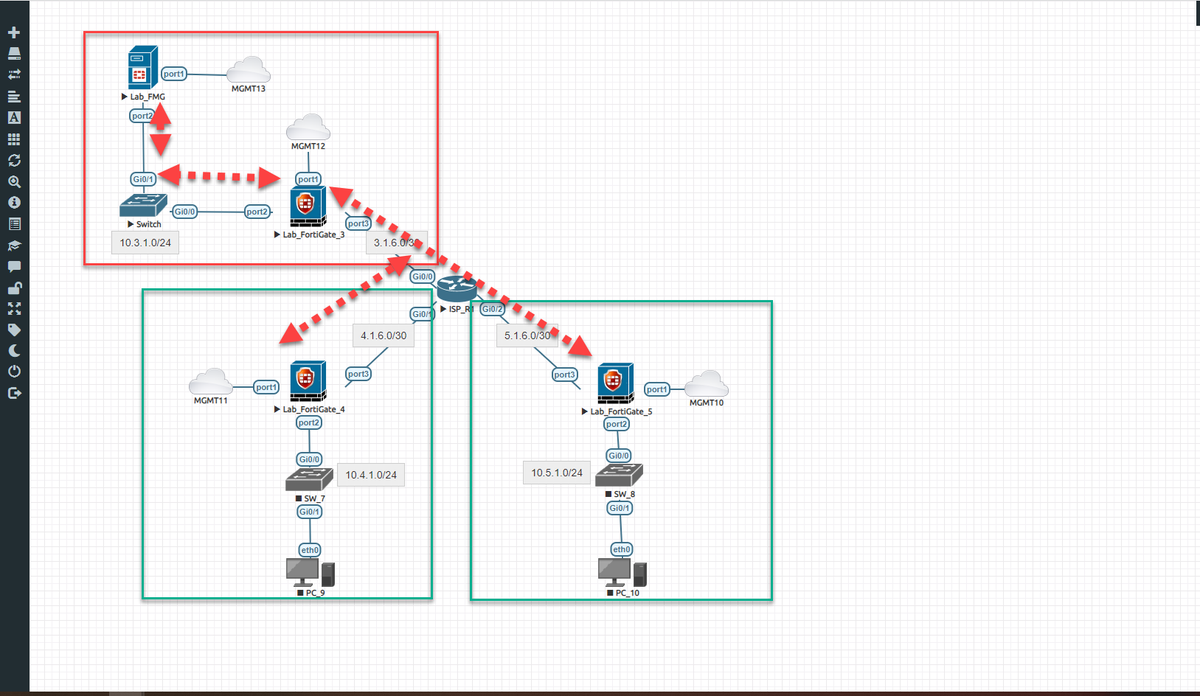
So how can VIP help me with this lab? I wanted to test if I can connect FGT's that cross over the WAN and connect to FMG and FAZ that sits behind a FGT inside of adding it via that inside (LAN) address and traverse through the IPSec tunnel. 

Why? Well what if the tunnel goes down, then along with other resources my end users at Site A cant reach because the tunnel is down, my FortiGate at that site can't be managed by FortiManager and FortiAnayzler.
So the first step in this process is to configure a VIP on my FGT that FMG and FAZ(FAZ is not in this lab) sits in front of. The VIP is configured as follows:
FMG-VIP: Map 3.1.6.2 (WAN interface) to FMG (10.3.1.100).
FMG-VIP: Map 3.1.6.2 (WAN interface) to FMG (10.3.1.100).

But i wanted to make this VIP more specific because in a production enviornment I can be using more VIPs for other services, so I drilled down what Ports (both TCP and UDP) FMG will use. 



I confirmed from my studies that FMG uses the following to manage a FortiGate:
TCP 541 == Remote Management of Fortigate
TCP 8888 == FortiGuard Antispam and webfiltering rating lookup from Forticlient or FortiGate
TCP 8890 == FortiGuard AV and IPS update request from FortiGate
TCP 541 == Remote Management of Fortigate
TCP 8888 == FortiGuard Antispam and webfiltering rating lookup from Forticlient or FortiGate
TCP 8890 == FortiGuard AV and IPS update request from FortiGate

After configuring this, next I had to configure my firewall policy for my VIP to work properly. but even before that to effectively organize and manage my policy in the future, 



I created address objects and groups that had the remote fortigates WAN addresses so that I may set those as my "Source Addresses" in my policy. 





Heres why, the policy for my VIP will be allowing connections from outside (WAN) to inside (LAN). With opening up my network to the "wild" I had to make sure I make this policy as "SPECIFIC" as possible to not open up the network to threats. 
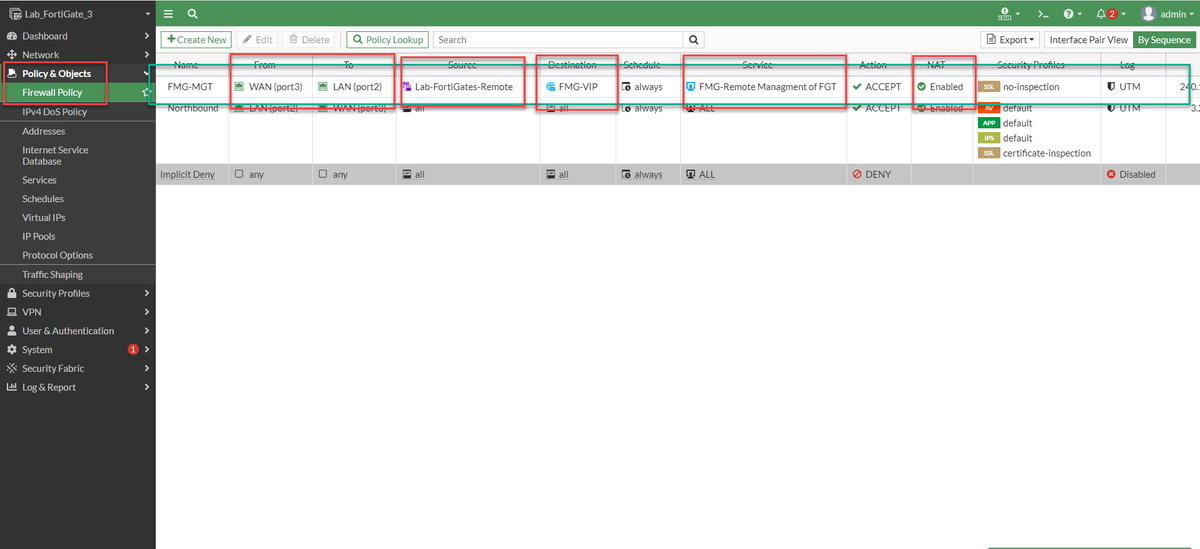
So after configuring the Address Objects needed, I created my firewall policy:
From WAN-->LAN
Source: Remote Fortigate (Address Group)
Destination: FMG-VIP (Destination NAT)
Service: FMG ports (TCP and UDP specific ports)
NAT: Enabled
From WAN-->LAN
Source: Remote Fortigate (Address Group)
Destination: FMG-VIP (Destination NAT)
Service: FMG ports (TCP and UDP specific ports)
NAT: Enabled

So when that traffic hits the WAN interface and destined for FMG, the source will be NAT'ed to the LAN interface so that FMG doesn't have to have a route to the FortiGates that are in the wild. 



To add, I took a packet capture to confirm the ports that are allowed for the VIP is working properly. 

The FortiGate in front of FMG (Lab-FortiGate-3) is doing NAT and passing those ports as the source is the LAN interface of the FortiGate
Source: 4.1.6.2
Destination: 3.1.6.2 - FortiManager VIP/ WAN IP
Source NAT'ed: 10.3.1.254
Destination NAT'ed: 10.3.1.100 - FortiManager



Source: 4.1.6.2
Destination: 3.1.6.2 - FortiManager VIP/ WAN IP
Source NAT'ed: 10.3.1.254
Destination NAT'ed: 10.3.1.100 - FortiManager



This was fun, more to come
"Stay in the gym" - JM / CS
"Stay in the gym" - JM / CS
• • •
Missing some Tweet in this thread? You can try to
force a refresh










