1/ #ThreatHunting
MeshCentral is another remote admin software installed by TAs we have seen in our IR cases [1].
Following is a brief introduction to the software and what forensic traces MeshCentral leaves on the network and the hosts. 🧵
#CyberSecurity
MeshCentral is another remote admin software installed by TAs we have seen in our IR cases [1].
Following is a brief introduction to the software and what forensic traces MeshCentral leaves on the network and the hosts. 🧵
#CyberSecurity

2/ For our tests, we use the hosted instance of MeshCentral.com, but the management software can also be run on a separate server, controlled by the TA.
After logging into the panel, we can download an agent for different operating systems (Windows, Mac, Linux).
After logging into the panel, we can download an agent for different operating systems (Windows, Mac, Linux).

3/ Before the installation or execution of the agent, the server URL is displayed under "Connection Details".
In our example, the agent connects to meshcentral.com, but another domain can be configured when the management server is self-hosted.
In our example, the agent connects to meshcentral.com, but another domain can be configured when the management server is self-hosted.

4/ In an IR case, we found the MeshCentral config on a host where the Server URL was
wss://mesh.<redacted>.com:443/agent.ashx
a self-hosted instance of the management server.
wss://mesh.<redacted>.com:443/agent.ashx
a self-hosted instance of the management server.
5/ We could search for "agent.ashx" in the proxy logs for hunting MeshCentral network connections.
Even if the protocol used is WebSockets, an initial HTTP connection takes place, where the upgrade to the WSS connection is negotiated (which should log the URL). [3]
Even if the protocol used is WebSockets, an initial HTTP connection takes place, where the upgrade to the WSS connection is negotiated (which should log the URL). [3]
6/ When running the agent on our host, we see the configured command line parameters (--connect, --hideConsole).
Even if the executable is renamed, these parameters could be used to identify a MeshAgent installation if command logging is active.
Even if the executable is renamed, these parameters could be used to identify a MeshAgent installation if command logging is active.

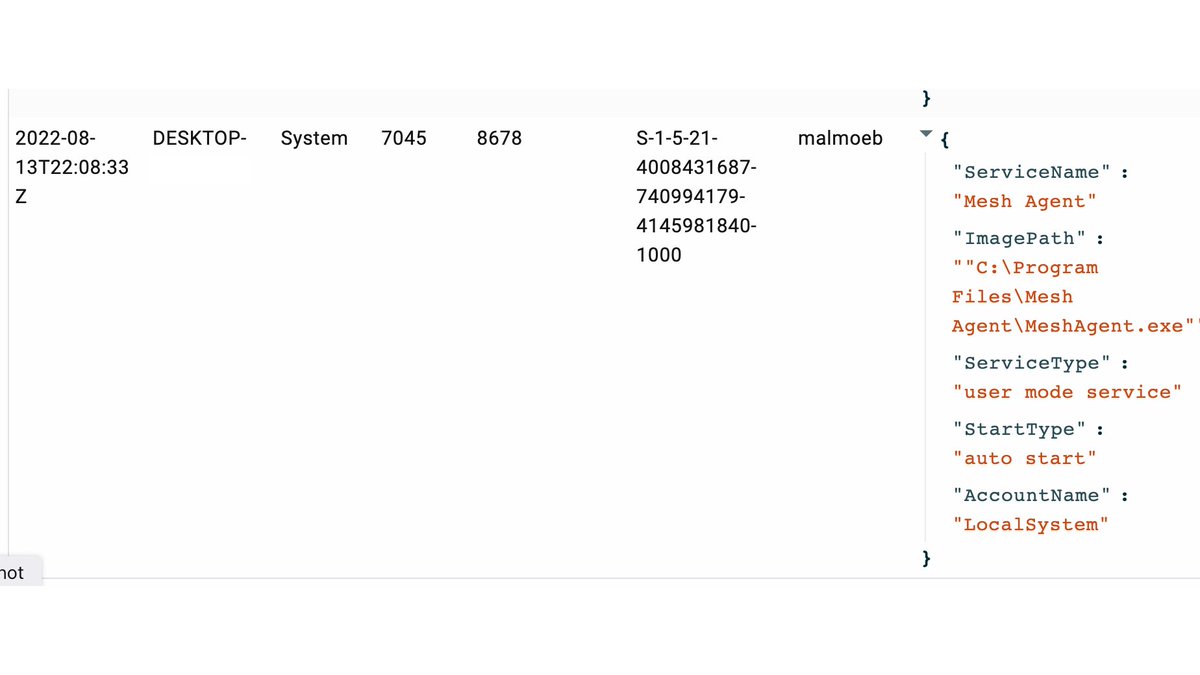
7/ After starting the agent on our host, the computer immediately checks in with the Management server. 

12/ With the @velocidex Velociraptor Hunt DNSCache, we see that the host has resolved the meshcentral.com domain used within the configuration from the agent. 

13/ Perhaps a better hunt for MeshCentral is within the firewall rules, which can be done quickly with Velociraptor's Hunt FirewallRules. 

14/ Interesting is a file with the extension ".msh", which contains the agent configuration, and is placed in the same folder as the agent. 

18/ MeshCentral should be relatively easy to find on the network with the artifacts and hunts presented above and could be signs of an active TA on the network.
Good luck 🍀
And btw, @IcsNick has tweeted a list of other remote admin tools [2], which you should check out ☝️
Good luck 🍀
And btw, @IcsNick has tweeted a list of other remote admin tools [2], which you should check out ☝️
19/ References:
[1] meshcentral.com/info/
[2]
[3] todaysoftmag.com/article/491/ht…
[1] meshcentral.com/info/
[2]
https://twitter.com/IcsNick/status/1557747197982248960
[3] todaysoftmag.com/article/491/ht…
• • •
Missing some Tweet in this thread? You can try to
force a refresh