1/ #ThreatHunting:
#QuasarRAT is another RAT we see from time to time in our IR cases and was also used against NATO facilities in March. [1]
We can hunt for
1⃣ The default port within the FW logs
2⃣Mutexes
3⃣User-Agent
4⃣Persistence mechanisms
🧵
#QuasarRAT is another RAT we see from time to time in our IR cases and was also used against NATO facilities in March. [1]
We can hunt for
1⃣ The default port within the FW logs
2⃣Mutexes
3⃣User-Agent
4⃣Persistence mechanisms
🧵
2/ @qualys has published an excellent paper ("Stealthy Quasar Evolving to Lead the RAT Race") about Quasar, where the whole builder and much more are described in detail. [2]
3/ In the client builder (which creates an executable which is used for the infection), the default port is pre-configured to 4782. 

4/ On ThreatFox by @abuse_ch, we see that a quarter of the samples kept this default port. [3]
The other samples use a different high port.
The other samples use a different high port.

6/ With a regex, we can find these random mutexes and thus efficiently find infected clients on the network:
\\[0-9a-f]{8}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{12}$
\\[0-9a-f]{8}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{12}$
7/ Using the example of a recent sample on Bazaar [4], we look at the Mutexes logged by @joe4security. [5]
So it seems that besides the default port also the default mutex values are used ITW.
So it seems that besides the default port also the default mutex values are used ITW.

8/ Hunting for Mutexes with @velocidex's Velociraptor with the Mutants-Hunt with the following regex:
(?-i)\\[0-9a-f]{8}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{12}$
Which finds the infected machine in the lab 😎
(?-i)\\[0-9a-f]{8}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{12}$
Which finds the infected machine in the lab 😎

9/ In networks were TLS is broken up on the proxy, the hard-coded user agent string could be used for hunting or setting up monitoring for this value. [6] 

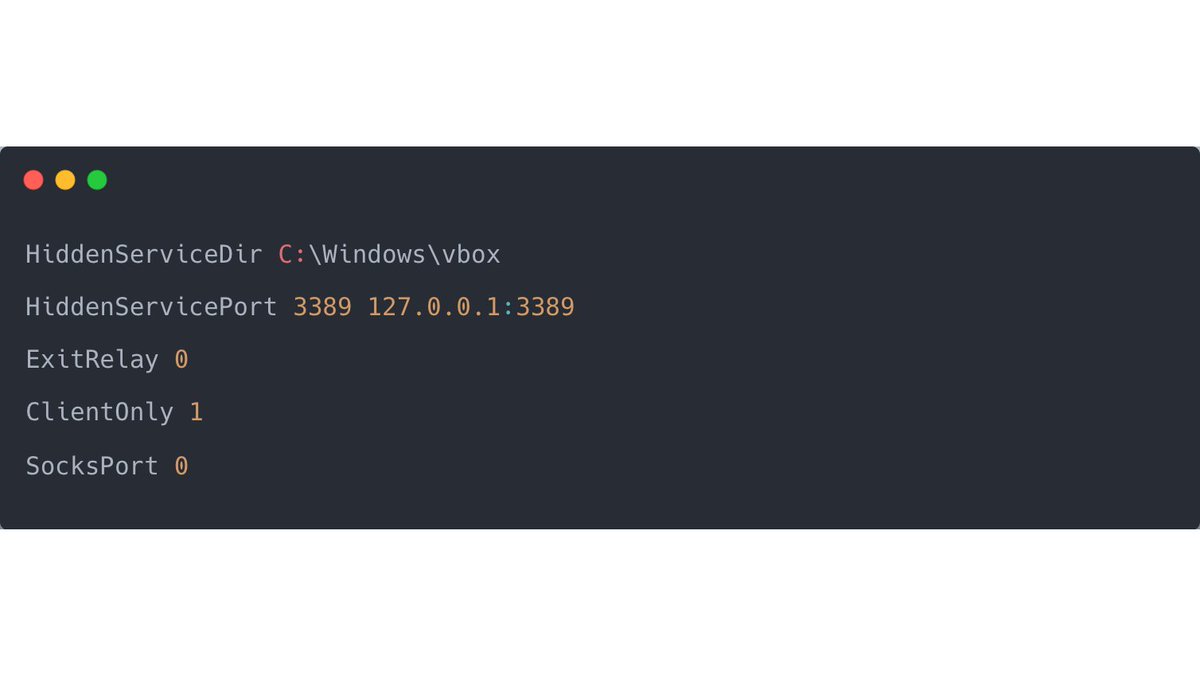
10/ Quasar uses the same persistence mechanisms as AsyncRAT, which we analyzed in a previous tweet [9].
A run-key entry is created when ran with an unprivileged user, or a new scheduled task is created when ran with administrative credentials.
A run-key entry is created when ran with an unprivileged user, or a new scheduled task is created when ran with administrative credentials.

11/ And although @pmelson pointed out in March of this year that the source code for Quasar is still available online on Github, nothing has not changed 🤷♂️. [7], [8]
12/ References:
[1]
[2] qualys.com/docs/whitepape…
[3] threatfox.abuse.ch/browse/malware…
[4] bazaar.abuse.ch/sample/4a3a8ab…
[5] joesandbox.com/analysis/64902…
[6] github.com/quasar/Quasar/…
[7] github.com/quasar/Quasar
[8]
[9] github.com/quasar/Quasar/…
[1]
https://twitter.com/threatinsight/status/1504240694449225731
[2] qualys.com/docs/whitepape…
[3] threatfox.abuse.ch/browse/malware…
[4] bazaar.abuse.ch/sample/4a3a8ab…
[5] joesandbox.com/analysis/64902…
[6] github.com/quasar/Quasar/…
[7] github.com/quasar/Quasar
[8]
https://twitter.com/pmelson/status/1503550727263866884
[9] github.com/quasar/Quasar/…
• • •
Missing some Tweet in this thread? You can try to
force a refresh