
🚨 North Korean APT group responsible for crypto and NFT phishing campaign spanning over 190 domains
Targeting dozens of $ETH and $SOL projects.
Uses collections on NFT marketplaces to lure victims to malicious minting sites.
🧵1/
#Phishing #NFT #NorthKorea #cybercrime
Targeting dozens of $ETH and $SOL projects.
Uses collections on NFT marketplaces to lure victims to malicious minting sites.
🧵1/
#Phishing #NFT #NorthKorea #cybercrime
Campaign activity began in April and is on-going.
The following domains have been registered in the past three days:
golddao[.]site
seveneyes[.]online
tapfantasy[.]in
genmarket[.]app
moonbirdvictorian[.]app
disneyprincessnft[.]com
Full list of domains at the end.
2/



The following domains have been registered in the past three days:
golddao[.]site
seveneyes[.]online
tapfantasy[.]in
genmarket[.]app
moonbirdvictorian[.]app
disneyprincessnft[.]com
Full list of domains at the end.
2/




Campaign used @OVH and @Leaseweb dedicated hosting.
@OVH
15.235.33[.]18
51.222.199[.]231
51.222.199[.]226
64.44.135[.]136
141.95.37[.]116
158.69.133[.]72
198.50.143[.]9
@Leaseweb
23.106.160[.]200
3/
@OVH
15.235.33[.]18
51.222.199[.]231
51.222.199[.]226
64.44.135[.]136
141.95.37[.]116
158.69.133[.]72
198.50.143[.]9
@Leaseweb
23.106.160[.]200
3/
One of the primary lures is spamming the malicious minting site link in collections on NFT marketplaces.
There are potentially thousands of these collections.
The first 7 phishing sites checked had on average 21 NFT collections on @opensea linking to them.
4/
There are potentially thousands of these collections.
The first 7 phishing sites checked had on average 21 NFT collections on @opensea linking to them.
4/
For example, there are at least 21 NFT collections on @opensea using some variant of 'Crazy Mutant APE Kennel Club'
They all link back to malicious minting site mutantkennel[.]in.
The same collections are also listed on @Rarible and @X2Y2.
5/


They all link back to malicious minting site mutantkennel[.]in.
The same collections are also listed on @Rarible and @X2Y2.
5/



These 21 collections are tied to contracts made by 21 separate addresses that were seeded by 0x51057F6E40F4A77E72774d48B7E78FB4634c7681.
Every set of collections discovered followed the same TTP of 1 address seeding a large number of addresses to create the contracts.
6/


Every set of collections discovered followed the same TTP of 1 address seeding a large number of addresses to create the contracts.
6/



Credit goes to @Iamdeadlyz for originally discovering this activity way back in June on OpenSea with thebeeings[.]link.
7/
https://twitter.com/Iamdeadlyz/status/1533731008188940288
7/
This was all connected based on the actor's use of dedicated hosting and unique TTPs.
➡️Logging visitor data to a external site
➡️Sharing a NFT project price list
➡️Sharing a file linking images to targeted project
➡️Sharing spin.umd.js across all sites
8/
➡️Logging visitor data to a external site
➡️Sharing a NFT project price list
➡️Sharing a file linking images to targeted project
➡️Sharing spin.umd.js across all sites
8/
For the next few tweets the four listed sites plus thedoodles[.]site and ascendednft[.]site are being labeled as 'super sites'.
They are being used as quasi-C2 domains to host common files shared across the campaign and monitor site traffic.
9/
They are being used as quasi-C2 domains to host common files shared across the campaign and monitor site traffic.
9/
Unique TTP #1, site visitor information is logged to a external domain using a HTTP GET.
While each of the following super sites used '/postAddr.php', each had a distinct log format.
nserva[.]live
polarbears[.]in
zedrun[.]link
maincontrol[.]in
10/


While each of the following super sites used '/postAddr.php', each had a distinct log format.
nserva[.]live
polarbears[.]in
zedrun[.]link
maincontrol[.]in
10/


Visitors to cryptobuds[.]site triggered the following HTTP GET to polarbears[.]in.
'polarbears[.]in/postAddr.php?url=http://cryptobuds[.]site/&mmAddr=Undefined............&accessTime=Sun%20Aug%2021%202022%2000:14:00%20GMT+0000%20(GMT)&providerType=Undefined.........'
11/
'polarbears[.]in/postAddr.php?url=http://cryptobuds[.]site/&mmAddr=Undefined............&accessTime=Sun%20Aug%2021%202022%2000:14:00%20GMT+0000%20(GMT)&providerType=Undefined.........'
11/
Visitors to coolcats[.]in triggered a similar but differently formatted message to nserva[.]live.
'nserva[.]live/postAddr.php?mmAddr=0x0000000000000000000000000000000000000000&accessTime=Sat%20Aug%2020%202022%2023:58:41%20GMT+0000%20(GMT)&url=http://coolcats[.]in/'
12/
'nserva[.]live/postAddr.php?mmAddr=0x0000000000000000000000000000000000000000&accessTime=Sat%20Aug%2020%202022%2023:58:41%20GMT+0000%20(GMT)&url=http://coolcats[.]in/'
12/
Unique TTP #2, use of a shared NFT floor price list 'getPriceData.php' being pulled from one of the super sites.
Only issue with canned data is that is can be outdated.
Autoglyphs floor price is down ~50 $ETH between market rate and listed rate.
13/
Only issue with canned data is that is can be outdated.
Autoglyphs floor price is down ~50 $ETH between market rate and listed rate.
13/

Unique TTP #3, pulling 'imgSrc.js' from a super site.
Contains a list of targeted sites and the hosting location of image files used on their corresponding phishing site.
Assumption this is part of a site template as multiple sites pulled this file but didn't need it.
14/
Contains a list of targeted sites and the hosting location of image files used on their corresponding phishing site.
Assumption this is part of a site template as multiple sites pulled this file but didn't need it.
14/

Time for attribution.
The same North Korean cyber actors responsible for the massive Naver phishing campaign first documented by @prevailion are also behind this campaign.
prevailion.com/what-wicked-we…
15/
The same North Korean cyber actors responsible for the massive Naver phishing campaign first documented by @prevailion are also behind this campaign.
prevailion.com/what-wicked-we…
15/
One of the email accounts originally listed in the report 'gameproducters@outlook.com' has registered domains for both the Naver and the NFT campaigns (part 1).
Naver:
naveralt[.]com
naveralter[.]com
16/
Naver:
naveralt[.]com
naveralter[.]com
16/

The account has also registered the following (part 2).
NFT:
boredsnakesclub[.]com
pixelgenii[.]xyz
littleponies[.]xyz
stakejoe[.]xyz
Due to WHOIS privacy, only a handful have leaked through but enough to tie the account to both campaigns.
17/
NFT:
boredsnakesclub[.]com
pixelgenii[.]xyz
littleponies[.]xyz
stakejoe[.]xyz
Due to WHOIS privacy, only a handful have leaked through but enough to tie the account to both campaigns.
17/
Another email account 'tigercoco3015@gmail.com' has registered domains for both campaigns as well.
Naver:
navericorp[.]com
naverecorp[.]com
NFT:
lockedkongs[.]net
ascendednft[.]site
hokago[.]fun
18/
Naver:
navericorp[.]com
naverecorp[.]com
NFT:
lockedkongs[.]net
ascendednft[.]site
hokago[.]fun
18/
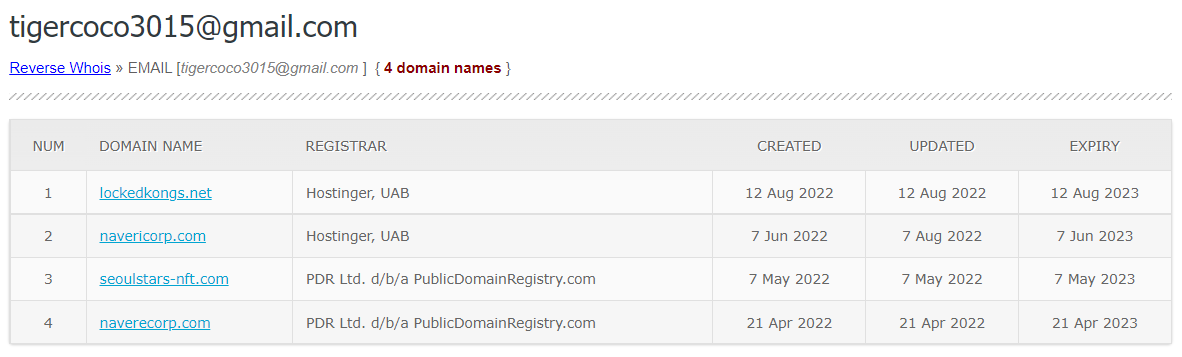
Remember the nserva[.]live domain from earlier?
It was co-hosted on @Leaseweb IP 23.106.160[.]66 alongside naverecorp[.]com.
naverecorp[.]com is associated with DPRK APT activity targeting Naver users.
19/
It was co-hosted on @Leaseweb IP 23.106.160[.]66 alongside naverecorp[.]com.
naverecorp[.]com is associated with DPRK APT activity targeting Naver users.
19/

• • •
Missing some Tweet in this thread? You can try to
force a refresh





