
Users of glassess beware! You may be leaking secret data during Zoom/Skype/etc videoconferences. Screen reflected in glasses, then visible during a videoconferencing. School-grade physics/optics sufficient to understand the exploit equations. arxiv.org/pdf/2205.03971… 



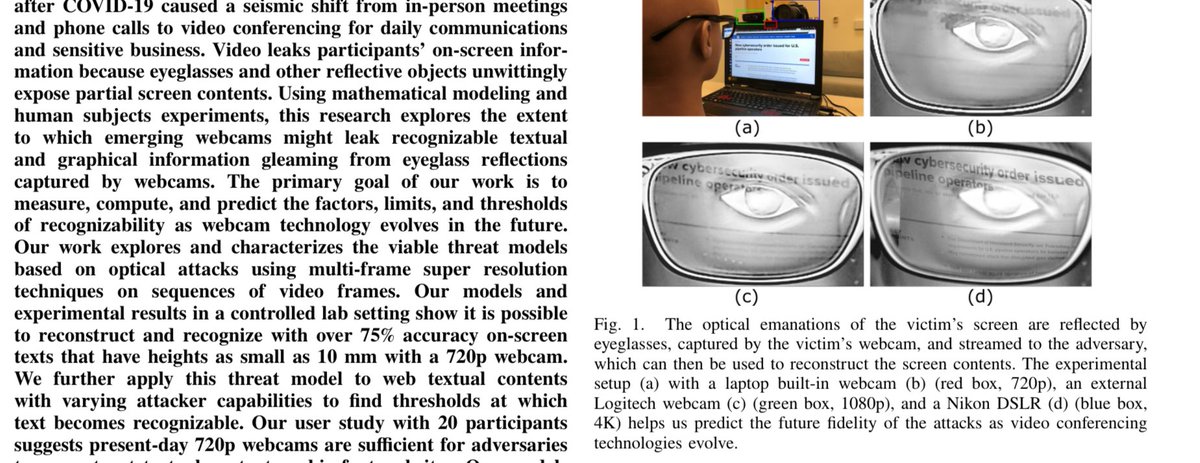
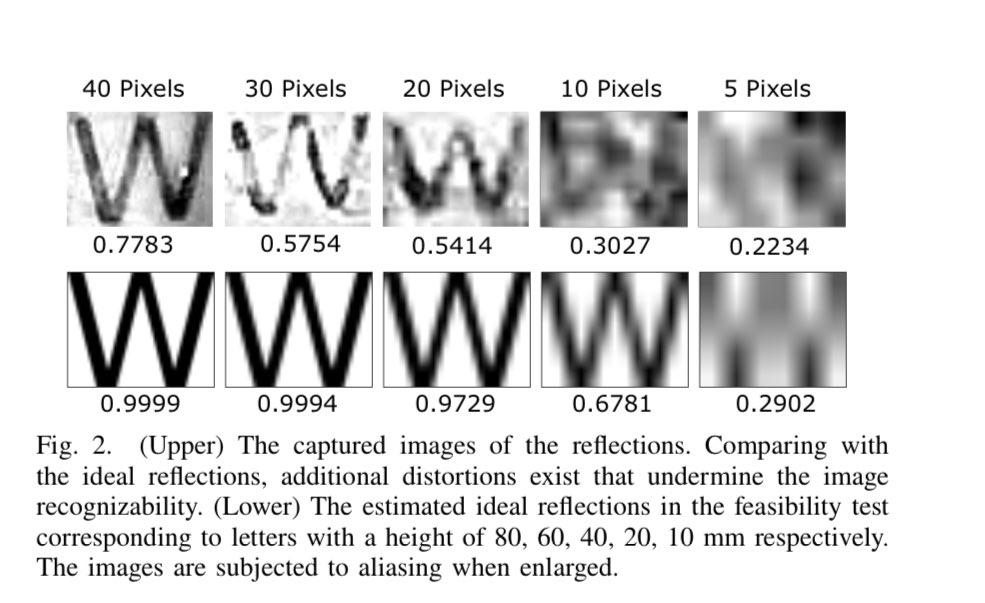


Solution/mitigation? Use a lamp. Or face bluring “reduce reflections’ light SNR, e.g., by placing a lamp facing their face whose light increase the noise portion”. Seriously this isn’t funny: if information may be leaking due to the use technology, it makes sense to do SOMETHING 




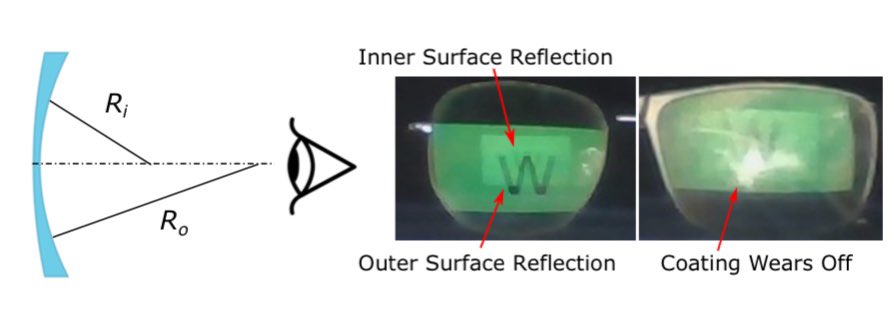
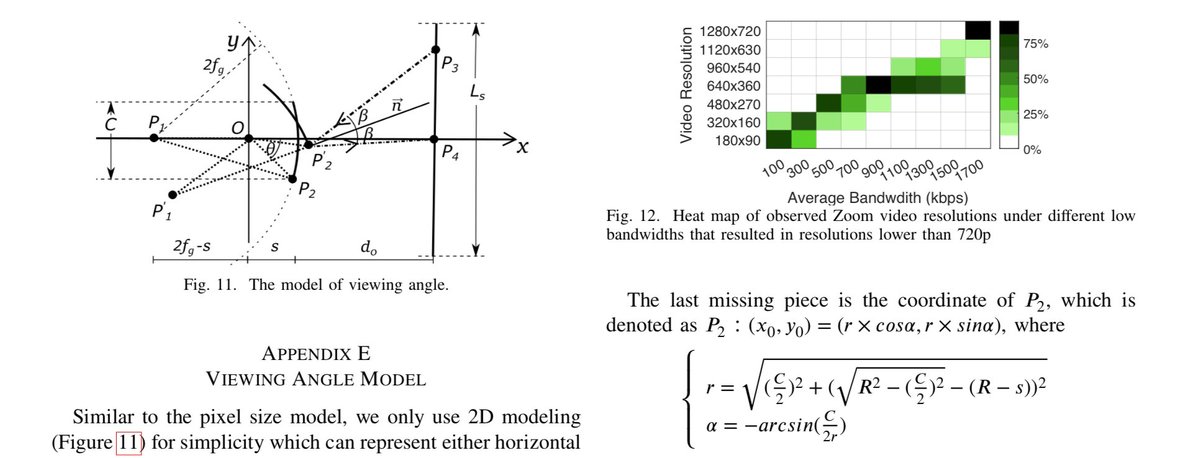
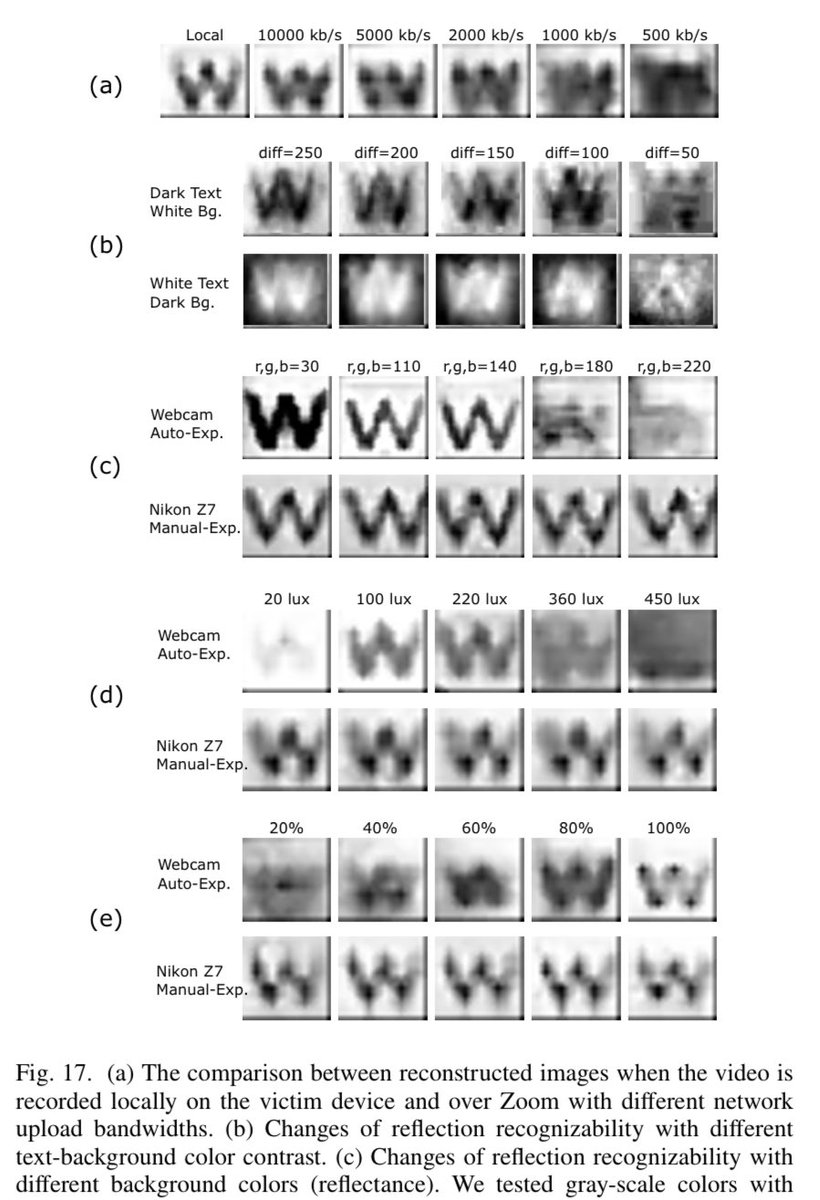
This may or may not sound hilarious/funny, but laughing aside, it is imaginable that data may eventually leak in this way (and a #GDPR data breach notice would have to be issued!). It reminds me of attacks using light sensors to steal user’s data. blog.lukaszolejnik.com/stealing-sensi…
• • •
Missing some Tweet in this thread? You can try to
force a refresh



































