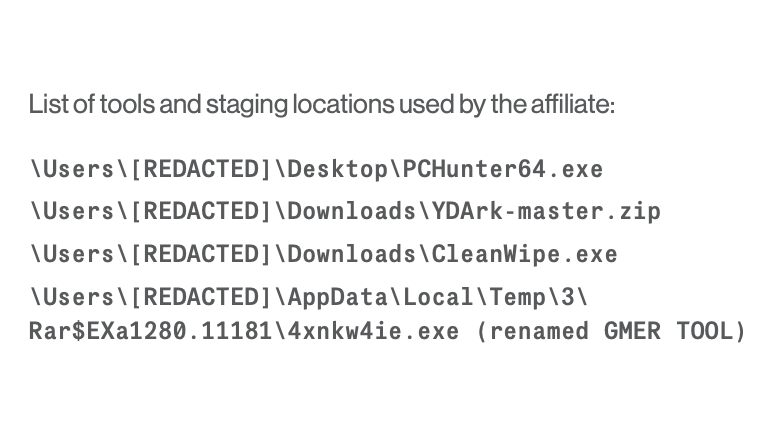
1/ #ThreatHunting:
In a compromised network, we saw the following request in the proxy logs:
www.advanced-ip-scanner[.]com/checkupdate.php?[..]
This scanner is trendy among ransomware groups and has been mentioned in reports by @TheDFIRReport, among others. [1] 🧵
In a compromised network, we saw the following request in the proxy logs:
www.advanced-ip-scanner[.]com/checkupdate.php?[..]
This scanner is trendy among ransomware groups and has been mentioned in reports by @TheDFIRReport, among others. [1] 🧵
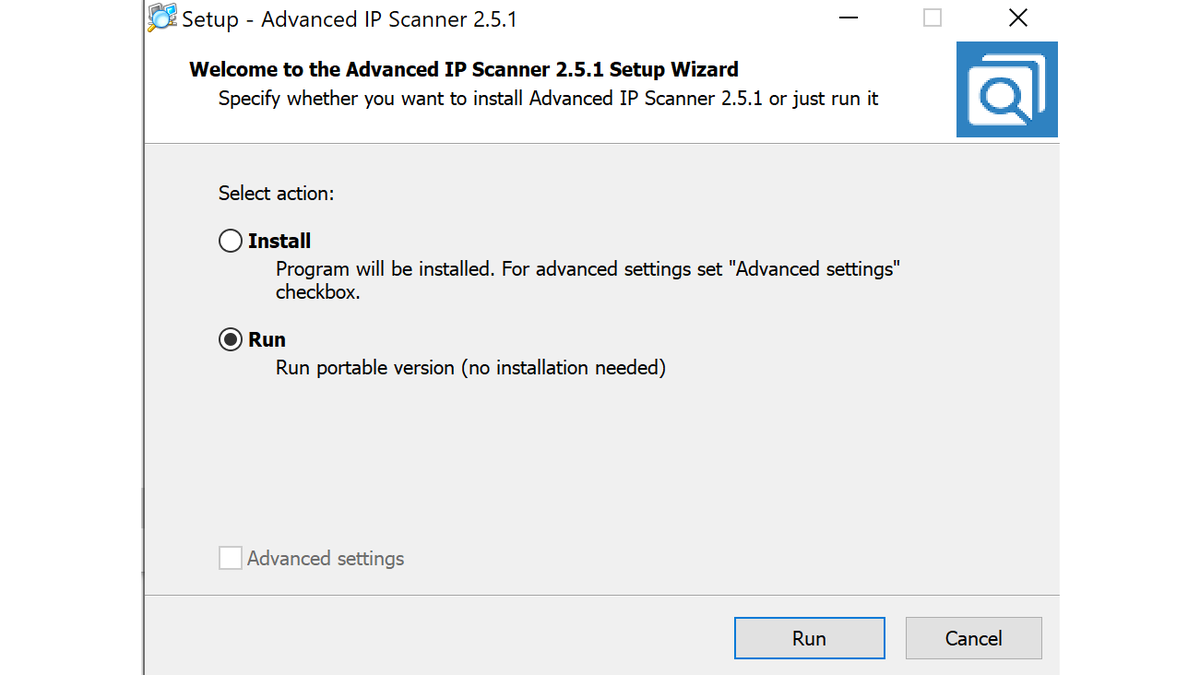
2/ This HTTP request can now be used very well for an alert.
Or better, collect and monitor all your DNS logs, because a DNS request will still go out if the Advanced IP Scanner is run without an installation (portable version).
An excellent opportunity for detection.
Or better, collect and monitor all your DNS logs, because a DNS request will still go out if the Advanced IP Scanner is run without an installation (portable version).
An excellent opportunity for detection.
4/ DFIR Tip:
Inside the registry (HKCU\Software\Famatech\advanced_ip_scanner\State) we can find interesting forensic artifacts like the last scanned range. 🕵️♀️
Reference:
[1]
Inside the registry (HKCU\Software\Famatech\advanced_ip_scanner\State) we can find interesting forensic artifacts like the last scanned range. 🕵️♀️
Reference:
[1]
https://twitter.com/TheDFIRReport/status/1470373411218239488

• • •
Missing some Tweet in this thread? You can try to
force a refresh