1/ #ThreatHunting:
In a compromised network, the TA used PCHunter on different systems to disable the local AV (or at least tried it).
In the web requests recorded on the firewall, we found traces of the download:
www.epoolsoft[.]com/pchunter/pchunter_free
🧵 #CyberSecurity
In a compromised network, the TA used PCHunter on different systems to disable the local AV (or at least tried it).
In the web requests recorded on the firewall, we found traces of the download:
www.epoolsoft[.]com/pchunter/pchunter_free
🧵 #CyberSecurity
2/ @CrowdStrike also mentioned PCHUnter in the latest ThreatHunting report, along with GMER.
go.crowdstrike.com/rs/281-OBQ-266…
go.crowdstrike.com/rs/281-OBQ-266…
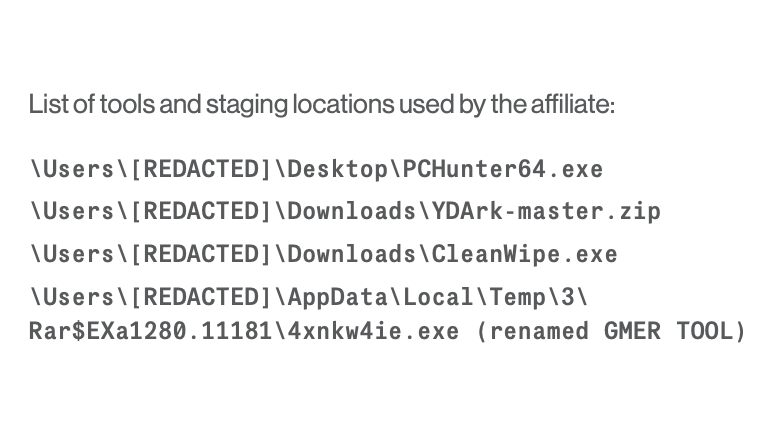
3/ I have tweeted about two of these tools (PCHunter / GMER) before, and we also see these two products regularly in our IR cases.
https://twitter.com/malmoeb/status/1514520454400253952
4/ Bottom line: Pay attention to downloads and or AV alerts which could indicate the download or the use of one of these tools, as this might be an active TA in your network. 📞🚒🧑🚒
• • •
Missing some Tweet in this thread? You can try to
force a refresh