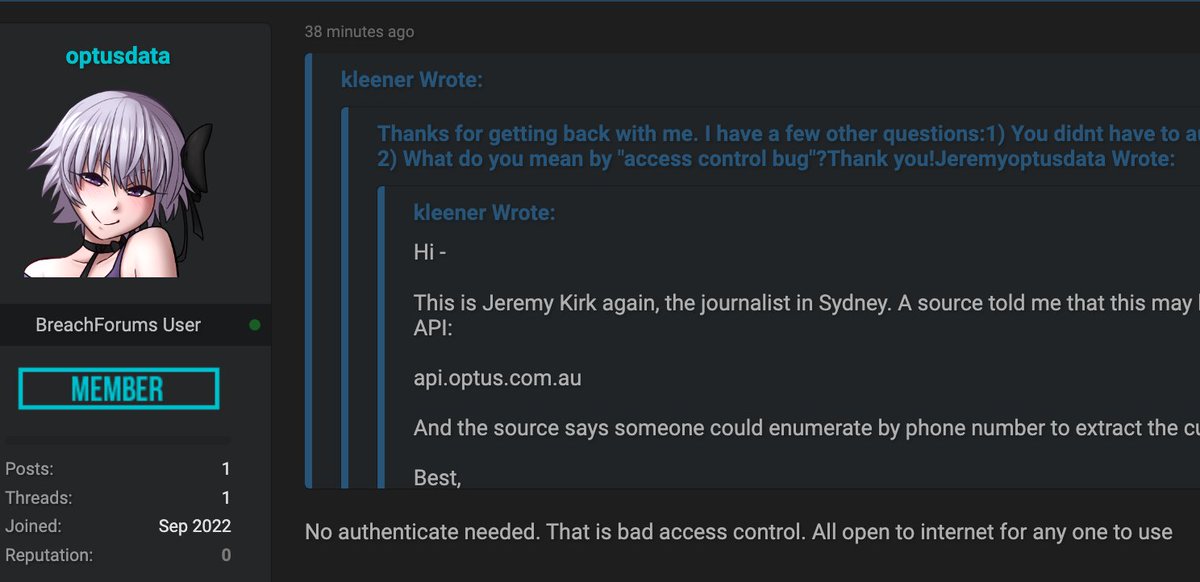
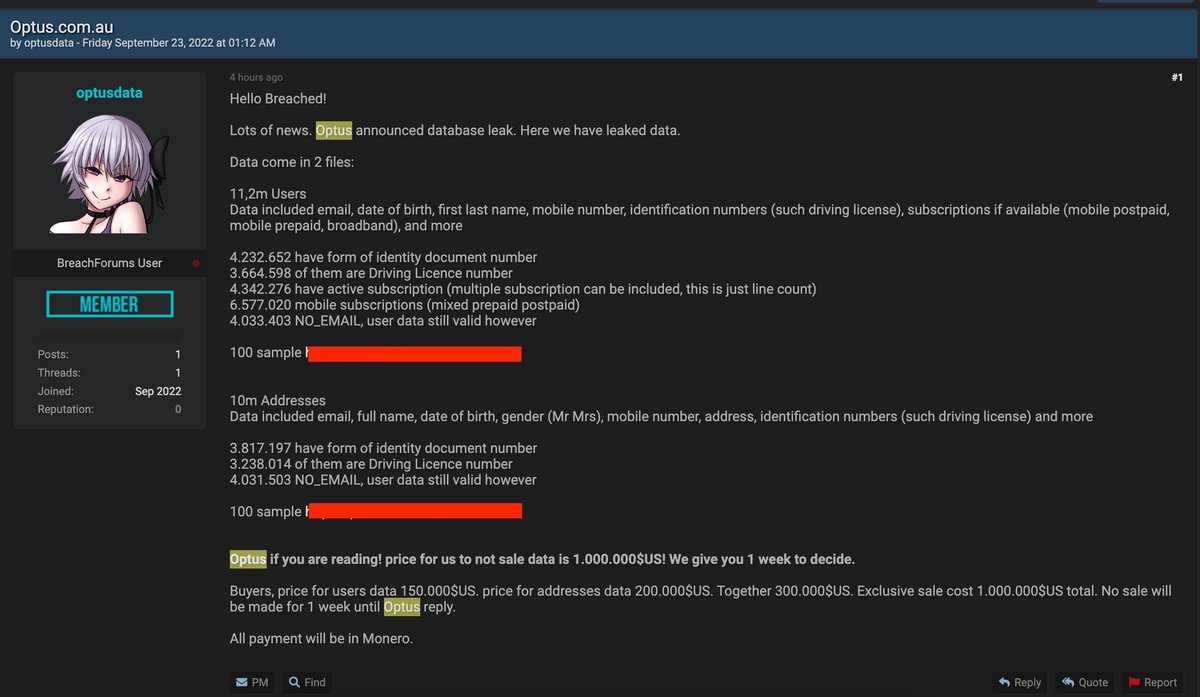
Someone is claiming to have the stolen Optus account data for 11.2 million users. They want $1 million in the Monero cryptocurrency from Optus to not sell the data to other people. Otherwise, they say they will sell it in parcels. #optus #auspol #infosec #OptusHack 
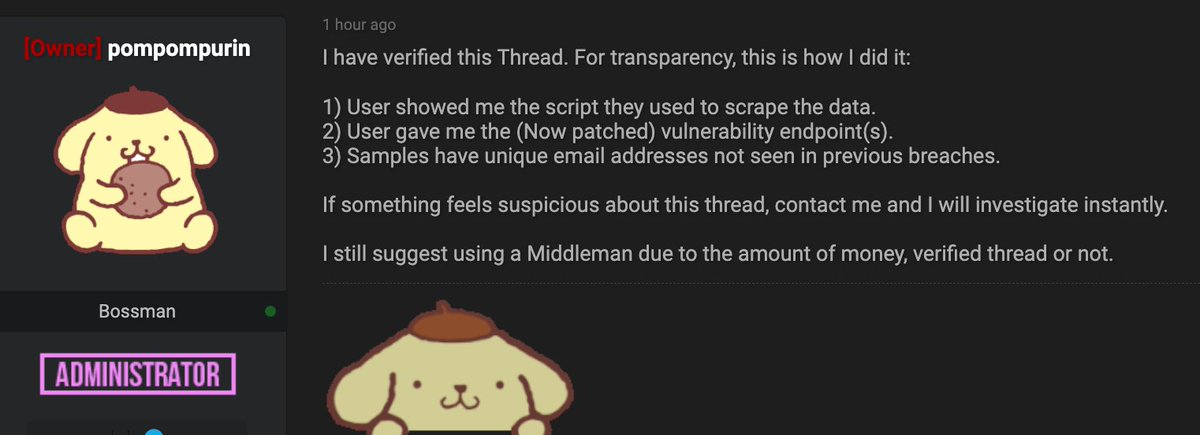
The person who runs this data market where the Optus data was posted says the data is real (I have not verified the data yet). The person writes that "optusdata" showed the script used to scrape the data and passed along info about the vulnerable endpoint. #infosec #OptusHack 
I've run 10 email addresses from the second sample of the Optus data through @haveibeenpwned. Nine have been in multiple data breaches before, but one is unique to this sample. That's a strong sign this leak is the real deal.
@haveibeenpwned I just ran 13 email addresses from the first batch of sample data from the alleged Optus leak through @haveibeenpwned. Six come back as unique (not in another breach indexed in HIBP). Again, another strong sign that the Optus data is real. #OptusHack #infosec #auspol @troyhunt
I queried Optus. Optus says: "We are investigating the legitimacy of this."
I've literally found someone down the road from me in the sample data. When I get out of my bathrobe and stop tweeting, I'll go down there and see if I can find the person to confirm her data.
I found the person in the data set. She was working in her front yard. She wants to stay unnamed but confirmed she is a former Optus customer and that her data is accurate. We still need a confirm from Optus on the data but this is all lining up. #OptusHack #auspol #infosec
I explained who I was and handed her a printout of her data (as an aside, kind of a weird experience - shoe leather journalism meets cyberspace). She said it was kind of scary. She hadn't been contacted by Optus yet. #OptusHack #auspol
Here's another sign the data may have come from Optus. There are email addresses like this: NO_EMAIL82320714@OPTUS.COM.AU. Those addies are in records where the person has no other email, which suggests Optus assigned an address if none was supplied. Just my guess though.
I haven't checked all of the NO_EMAIL email addresses, but none so far are turning up in @haveibeenpwned.
I reached the Optus hacker. The person had a fair bit to say. I've started a new thread here. #OptusHack #infosec #auspol
https://twitter.com/Jeremy_Kirk/status/1573652986437726208
Here's a tidy news story that wraps up all my Optus data breach tweets. I've tried to make this understandable for everyone. It's important we understand how our personal data is at risk if not protected.
bankinfosecurity.com/optus-under-1-…
#OptusHack #auspol #infosec
bankinfosecurity.com/optus-under-1-…
#OptusHack #auspol #infosec
• • •
Missing some Tweet in this thread? You can try to
force a refresh