Former #infosec journo, now threat intel @Intel471inc. Interests: Cybercrime, data breaches, OSINT. Also produce Intel 471's "Cybercrime Exposed" podcast.
How to get URL link on X (Twitter) App


 This is pre-mission. Pressurised space suit, pre-flight plans.
This is pre-mission. Pressurised space suit, pre-flight plans. 




 My brother was a handsome, blonde haired-kid. He was two-and-a-half years younger. Our relationship was typical. Sparring siblings but friends in the same household. We were never close, but united in an upbringing from loving, caring parents. But we were different.
My brother was a handsome, blonde haired-kid. He was two-and-a-half years younger. Our relationship was typical. Sparring siblings but friends in the same household. We were never close, but united in an upbringing from loving, caring parents. But we were different.


 A decade ago, I bought a bitcoin for $12. I was intrigued to investigate how it worked. The blockchain and bitcoin's shadowy architect, Satoshi Nakamoto, was fascinating. It felt mysterious, somewhat rebellious and was a technological marvel. #cryptocurrency
A decade ago, I bought a bitcoin for $12. I was intrigued to investigate how it worked. The blockchain and bitcoin's shadowy architect, Satoshi Nakamoto, was fascinating. It felt mysterious, somewhat rebellious and was a technological marvel. #cryptocurrency

 I just fielded a good question from a reporter: How can we trust that this group/site is @medibank's real extortionist? And how can we verify that? There's a bit of complicated history behind it, but @BleepinComputer has it here: bleepingcomputer.com/news/security/…
I just fielded a good question from a reporter: How can we trust that this group/site is @medibank's real extortionist? And how can we verify that? There's a bit of complicated history behind it, but @BleepinComputer has it here: bleepingcomputer.com/news/security/…



https://twitter.com/Cyberknow20/status/1581838827592699904To recap, Woolworths said on Friday that 2.2 million people were affected after its CRM system was accessed. For 1.2 million, only email was exposed. For the rest, names, email addresses, phone numbers, delivery addresses, sometimes birth dates. PR here: woolworthsgroup.com.au/au/en/media/la…

 Quick observation on this new data. It appears Medicare numbers may be exposed for some people. Redacted screenshot below. #Optus #OptusDataBreach
Quick observation on this new data. It appears Medicare numbers may be exposed for some people. Redacted screenshot below. #Optus #OptusDataBreach 
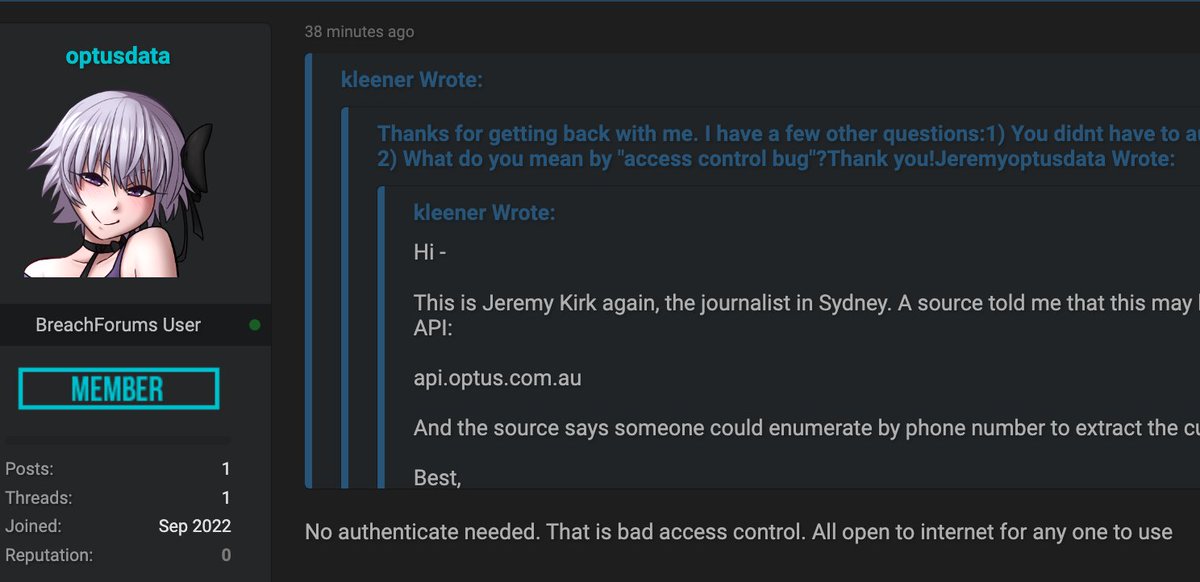

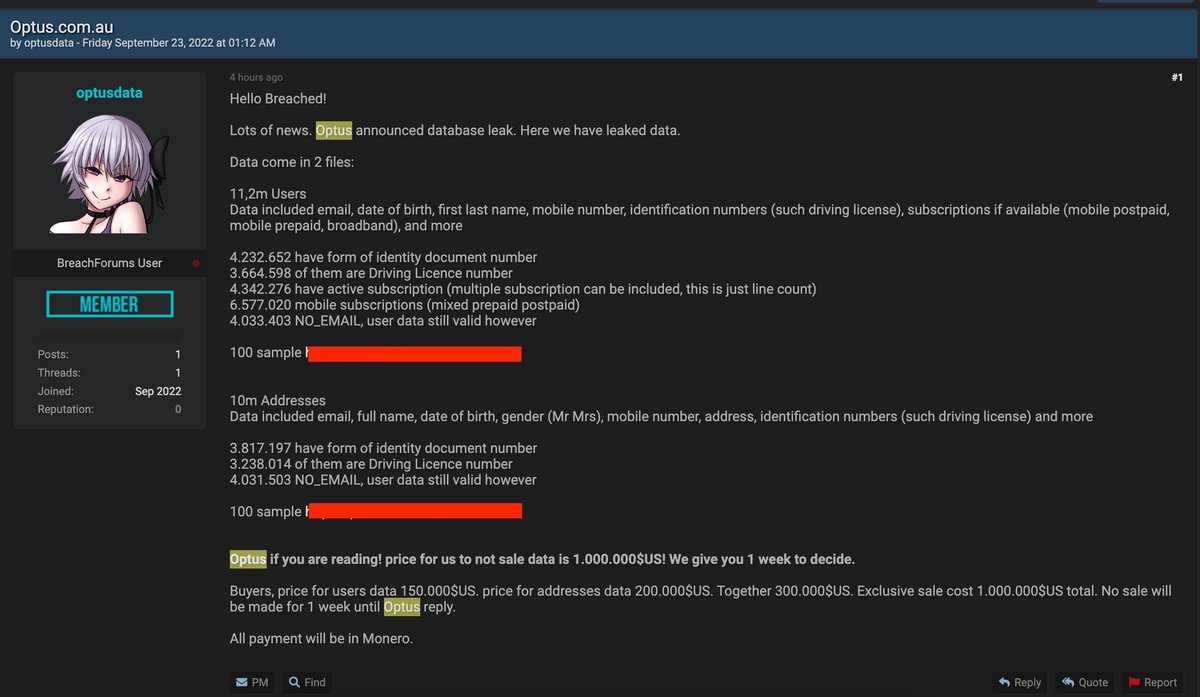
 The person who runs this data market where the Optus data was posted says the data is real (I have not verified the data yet). The person writes that "optusdata" showed the script used to scrape the data and passed along info about the vulnerable endpoint. #infosec #OptusHack
The person who runs this data market where the Optus data was posted says the data is real (I have not verified the data yet). The person writes that "optusdata" showed the script used to scrape the data and passed along info about the vulnerable endpoint. #infosec #OptusHack