1/ #ThreatHunting: Normal users (not developers) who have Python in their Music (!) directory? This screams TA 😅
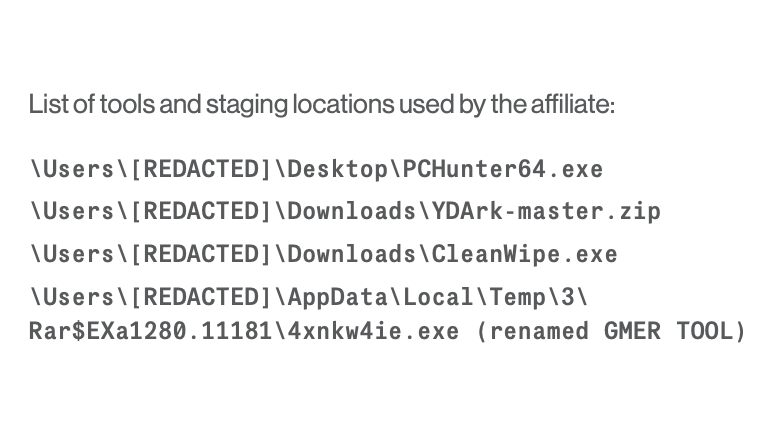
In an investigation on a breached network, we discovered the following directory:
C:\Users\<user>\Music\WPy64-39100\python-3.9.10.amdMusic\WPy64-39100
In an investigation on a breached network, we discovered the following directory:
C:\Users\<user>\Music\WPy64-39100\python-3.9.10.amdMusic\WPy64-39100
2/ The funny thing is that the TA appended "Music" to the ordinary directory name "python-3.9.10.amd64" to make it look more legitimate?
In several directories, we found attack scripts (written in Python), including noPac.py
(github.com/Ridter/noPac)
In several directories, we found attack scripts (written in Python), including noPac.py
(github.com/Ridter/noPac)

3/ And the whole impacket suite.
(github.com/SecureAuthCorp…)
Monitoring or creating a baseline (which users are using Python) could be helpful here, or just monitoring from which paths Python is started (like in our example from the Music directory).
(github.com/SecureAuthCorp…)
Monitoring or creating a baseline (which users are using Python) could be helpful here, or just monitoring from which paths Python is started (like in our example from the Music directory).

4/ Pyramid (github.com/naksyn/Pyramid) is an interesting project that tries to bypass EDRs by using Python to run the payloads.
@naksyn
@naksyn
5/ Excerpt from the GitHub repo:
[..] one of the most efficient solutions would be to block by default binaries and dlls signed by Python Foundation, creating exceptions only for users that actually need to use python binaries.
[..] one of the most efficient solutions would be to block by default binaries and dlls signed by Python Foundation, creating exceptions only for users that actually need to use python binaries.
• • •
Missing some Tweet in this thread? You can try to
force a refresh