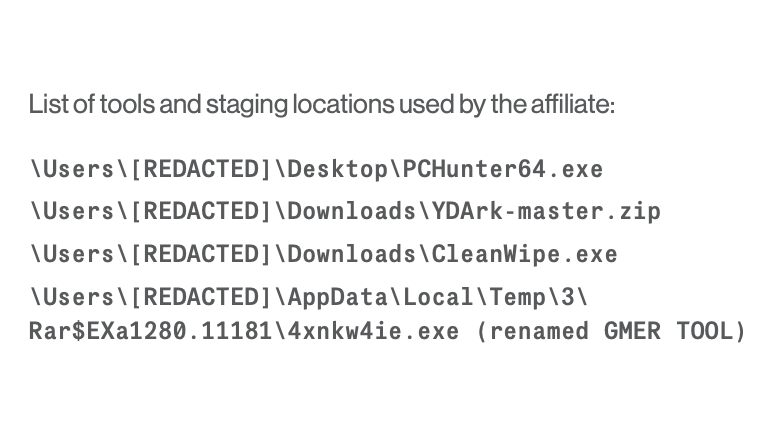
1/ #ThreatHunting: @Avast has blogged how Roshtyak checks the VBAWarnings registry value.
If the value is 1 ("Enable all macros"), then the code will not be executed because it is assumed that this setting is only enabled in a sandbox (or by courageous users). 🧵 #CyberSecurity
If the value is 1 ("Enable all macros"), then the code will not be executed because it is assumed that this setting is only enabled in a sandbox (or by courageous users). 🧵 #CyberSecurity
2/ "Interestingly, this means that users, who for whatever reason have lowered their security this way, are immune to Roshtyak." [1]
3/ However, this "Enable all macros" value can also be explicitly set for Outlook
(Computer\HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook - Level = 1).
If this value is set to 1 in a user context, a nifty persistence within Outlook may have been set up by a TA.
(Computer\HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook - Level = 1).
If this value is set to 1 in a user context, a nifty persistence within Outlook may have been set up by a TA.
4/ @MDSecLabs published a very readable article about an Outlook persistence technique almost two years ago. [2]
I could easily recreate this persistence in my lab, which still works up to this date. On the one hand, we could now hunt in our network if this registry key is set.
I could easily recreate this persistence in my lab, which still works up to this date. On the one hand, we could now hunt in our network if this registry key is set.
5/ Or we could check in which user directories the file VbaProject.OTM is present, which contains the macro code that would be executed when certain criteria are met (see MDSec's blog post [2])
Path on disk:
C:\Users\<user>\AppData\Roaming\Microsoft\Outlook\VbaProject.OTM).
Path on disk:
C:\Users\<user>\AppData\Roaming\Microsoft\Outlook\VbaProject.OTM).
6/ In our customer networks, we found very few VbaProject.OTM files in user directories, wich makes a manual analysis of the VBA code or monitoring for a creation of this file feasible.
• • •
Missing some Tweet in this thread? You can try to
force a refresh