1/ Perhaps a lesser known "feature" of Microsoft Authenticator, but the diagnostic data can be very helpful in investigating a compromised #Azure account where MFA is enabled but the user claims not to have confirmed the MFA Consent Prompt. 🧵
2/ You will find the diagnostic data here:
Authenticator App
▪️ Burger Menu
▪️ Send feedback
▪️ Having trouble?
▪️ View diagnostic data
Click "Copy all" and send the text via mail or other ways to your analysis device.
Authenticator App
▪️ Burger Menu
▪️ Send feedback
▪️ Having trouble?
▪️ View diagnostic data
Click "Copy all" and send the text via mail or other ways to your analysis device.

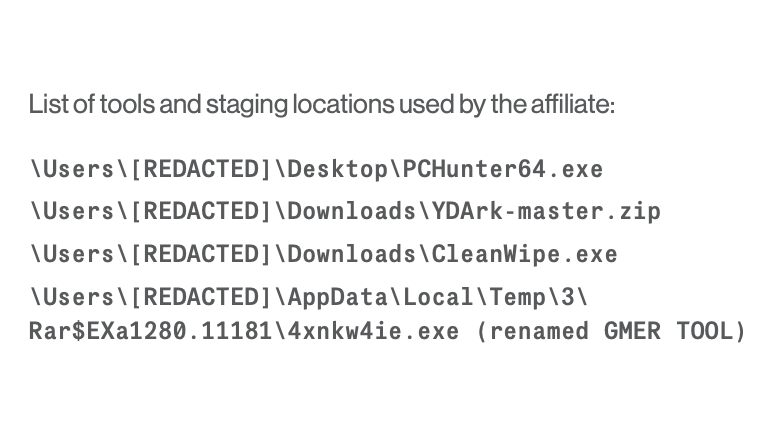
3/ When logging into an MFA protected (the second factor is the Consent Prompt) account, we see the following entries (abbreviated) in the Authenticator diagnostic data:
4/ 2022-10-09 18:24:48.700 VERB MfaSdk 0 TID=1 0 () handleCheckForAuthResponse(request:error:dosPreventer:currentDeviceToken:previousDeviceToken:):
➡️ Pending authentication found for username: 2c4fa44468@<redacted_domain>
➡️ Pending authentication found for username: 2c4fa44468@<redacted_domain>
5/ The random looking number above can be mapped to a user within the diagnostic data.
2022-10-09 18:24:51.286 VERB MfaSdk 0 TID=1 0 () -[AuthenticationSessionNotificationBuilder createStandardNotificationAlert:messageText:[..]]_block_invoke_2:
➡️ Approve button clicked
2022-10-09 18:24:51.286 VERB MfaSdk 0 TID=1 0 () -[AuthenticationSessionNotificationBuilder createStandardNotificationAlert:messageText:[..]]_block_invoke_2:
➡️ Approve button clicked
6/ There you have it.
We see in the logs that an authentication or confirmation has been requested and that the user has confirmed it. ✅
The sign-in logs will show that MFA was completed within Azure.
We see in the logs that an authentication or confirmation has been requested and that the user has confirmed it. ✅
The sign-in logs will show that MFA was completed within Azure.

7/ In the Authentication Details it also says "Mobile app notification".
The timestamps from the Authenticator App to the Sign-In logs are only a few seconds off, so correlation should not be that difficult.
The timestamps from the Authenticator App to the Sign-In logs are only a few seconds off, so correlation should not be that difficult.

8/ The data from the Authenticator App can be used to prove that a user has given his consent to the MFA prompt, and the attacker has logged into the account that way (the credentials must be known to the attacker, of course).
9/ But with this evidence of the user confirming the Consent Prompt, other attack vectors can be ruled out, which of course also affects the course of the investigation.
10/ @rootsecdev wrote an excellent blog post on how to improve MFA for Azure 💪🏅
trustedsec.com/blog/defending…
trustedsec.com/blog/defending…
• • •
Missing some Tweet in this thread? You can try to
force a refresh