#CertiKSkynetAlert 🚨
On October 11, 2022 at 11:19 PM UTC, Mango Market was attacked for a total loss of roughly ~$116M.
The attacker was able to manipulate the price of the MNGO token and exploitatively borrowed more assets than what they were supposed to be able to.
🧵…
On October 11, 2022 at 11:19 PM UTC, Mango Market was attacked for a total loss of roughly ~$116M.
The attacker was able to manipulate the price of the MNGO token and exploitatively borrowed more assets than what they were supposed to be able to.
🧵…
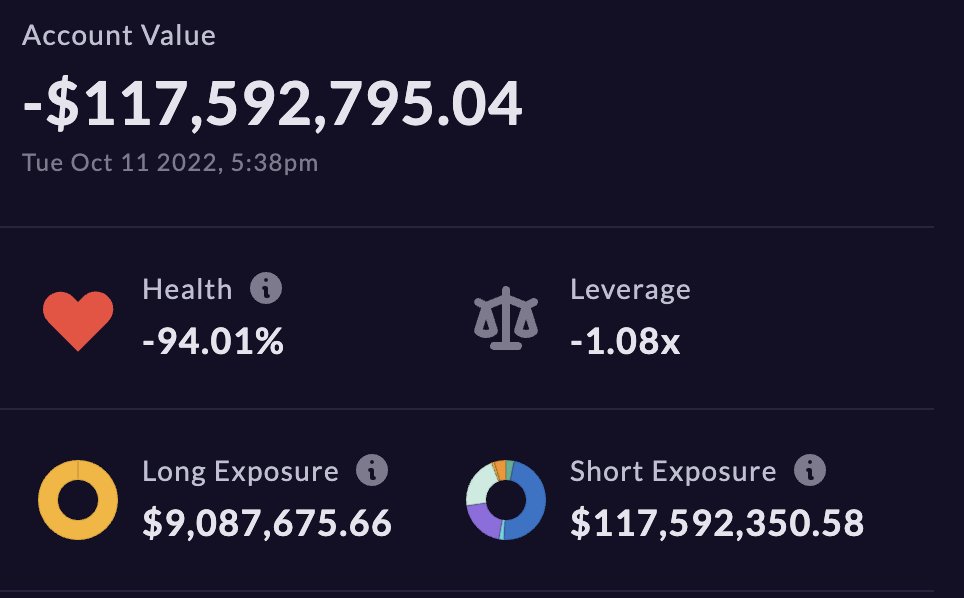
1/ The attacker funded Account A with 4,999,998.95 USDC. Account A then sold 488,302,109 MNGO worth of perpetual swaps on Mango Markets, worth $18,653,140.
Account B bought 482,745,055 of the MNGO swaps.
Account B bought 482,745,055 of the MNGO swaps.

2/ The attacker then began manipulating the price of MNGO on the spot MNGO/USDC market.
From a stable low of ~$0.038 prior to the attack, they pushed it up to a peak of $0.91.
From a stable low of ~$0.038 prior to the attack, they pushed it up to a peak of $0.91.

3/ This allowed both Account A and Account B, which the attacker resorted to, to compound their profits on top of what was already gained, and to borrow other tokens against this profit as collateral.
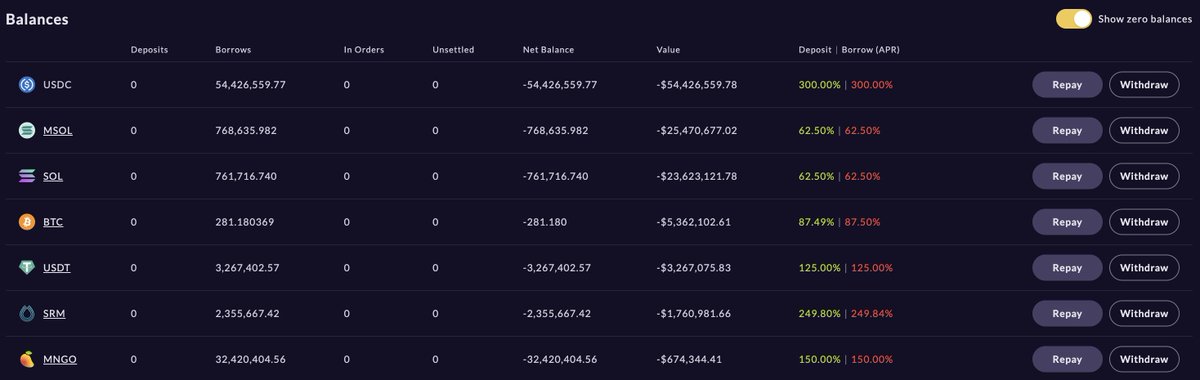
4/ Account A borrowed 0.337 BTC (worth $7.1K), 17,014,501 ($541K at time of writing), 2,650 USDC, 152,843 GMT ($97.7K), 1,809 AVAX ($28.9K), 98,295 RAY ($50.4K), 1,155 MSOL ($38.6K), 608 BNB (1$64.7K), 11,774 FTT ($273.8K), and 226 ETH ($289.5K) all at time of writing. 
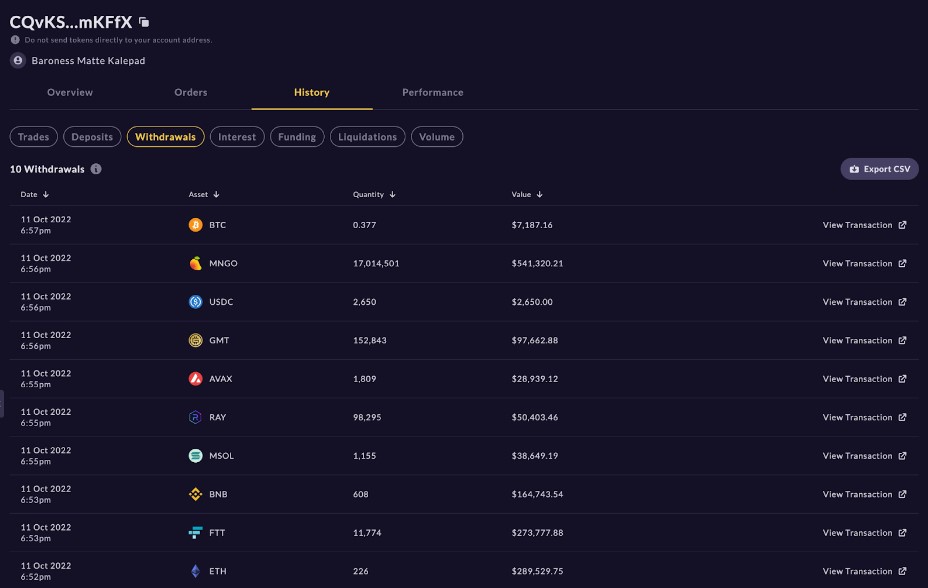
5/ Account B borrowed 54,426,559 USDC, 768,635 mSOL (worth $25.4M), 761,716 SOL (worth $23.6M), 281 BTC (worth $5.3M), 3.3M USDT, 2,355,667 SRM (worth $1.8M), and 32,420,404 MNGO (worth $674K at the time of writing). 
6/ The vulnerability here stemmed from the thin liquidity on the MNGO/USDC market, which was used as the price reference for the MNGO perpetual swap.
With only a few million USDC at their disposal, the attacker was able to pump the price of MNGO by 2,394%.
With only a few million USDC at their disposal, the attacker was able to pump the price of MNGO by 2,394%.
7/ The attacker manipulated the price by purchasing a huge amount of Mango token.
@mangomarkets uses Switchboard as the price oracle for Mango and Switchboard uses FTX and Raydium as the price feed.
The liquidity on Raydium is extremely low and can easily be manipulated.
@mangomarkets uses Switchboard as the price oracle for Mango and Switchboard uses FTX and Raydium as the price feed.
The liquidity on Raydium is extremely low and can easily be manipulated.
• • •
Missing some Tweet in this thread? You can try to
force a refresh