1\ #DFIR: How to investigate insider threats
Sharing the forensic methodology I follow when I'm investigating insiders 😍
This is where an employee sells creds/changes configs/runs malware leading to full DA compromise and then say they didn't do it O_o
inversecos.com/2022/10/how-to…
Sharing the forensic methodology I follow when I'm investigating insiders 😍
This is where an employee sells creds/changes configs/runs malware leading to full DA compromise and then say they didn't do it O_o
inversecos.com/2022/10/how-to…

2\ The questions that I use to guide the analysis and prioritisation of analysis are:
1. How was the device accessed around the suspected behaviour?
2. Where was the user/device when this occurred?
3. Was the insider active on their system?
4. What did the user do?
1. How was the device accessed around the suspected behaviour?
2. Where was the user/device when this occurred?
3. Was the insider active on their system?
4. What did the user do?
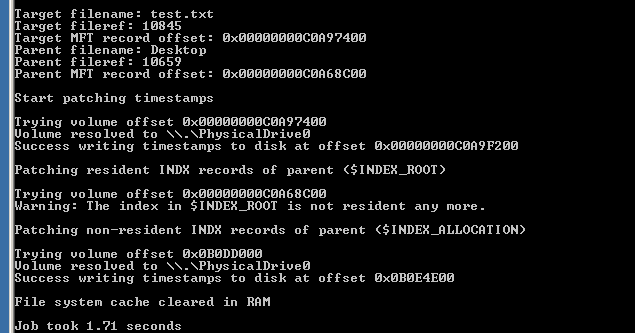
3\ To answer the first question, I look at SRUM, specifically the App Timeline Provider details.
I pull:
> Execution time of the malicious thingz
> Duration of execution
> User SID
Then, I cross correlate that user info with their corresponding ActivitiesCache.db. #DFIRISS3XY
I pull:
> Execution time of the malicious thingz
> Duration of execution
> User SID
Then, I cross correlate that user info with their corresponding ActivitiesCache.db. #DFIRISS3XY

4\ Now we know the user, we need to address how the logon occurred.
I pull:
> Logon events
> System wake/hibernation times
> Network SSID it was connected to (SRUM + Software reg + evtx)
Generally logon is not remote & the SSID tells you the physical location they did this.
I pull:
> Logon events
> System wake/hibernation times
> Network SSID it was connected to (SRUM + Software reg + evtx)
Generally logon is not remote & the SSID tells you the physical location they did this.

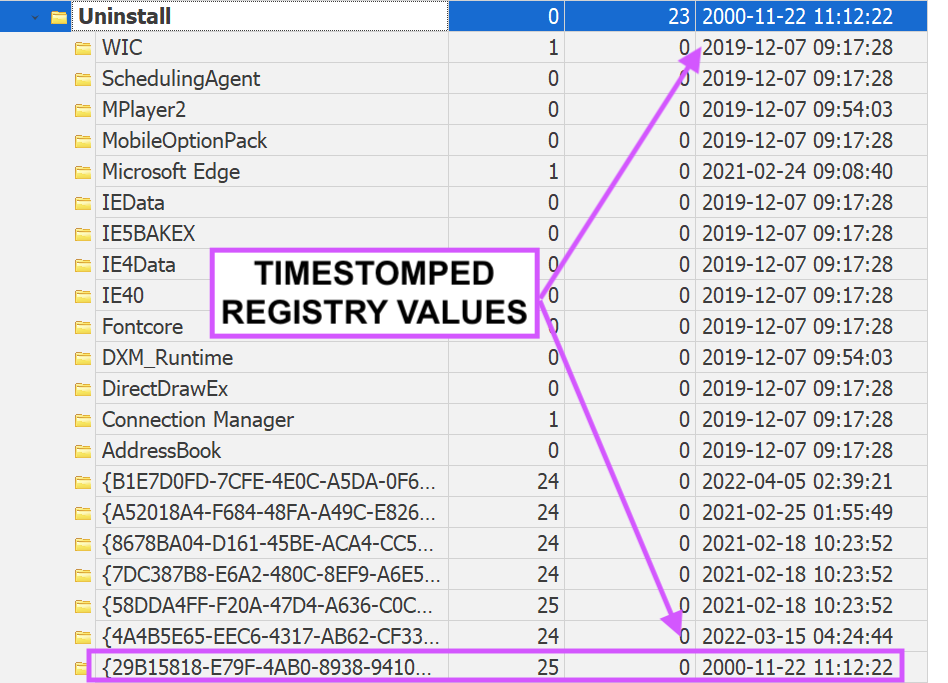
5\ Sometimes the users say they were on the system but not "active" ...*cries in awkward*
My fave artefact for this (amongst several) is AppSwitched under the "Feature Usage" registry key.
This tracks when a user ACTIVELY switches from one app to another in the taskbar.
My fave artefact for this (amongst several) is AppSwitched under the "Feature Usage" registry key.
This tracks when a user ACTIVELY switches from one app to another in the taskbar.

6\ You might ask how common are insider threats? I would say around 10% of cases I worked in the past year were insider.
I am obviously not an industry white paper :P so I'm not the best source for this. Also i notice an automatic assumption that everything is an external TA..
I am obviously not an industry white paper :P so I'm not the best source for this. Also i notice an automatic assumption that everything is an external TA..
7\ Lastly, this blog is NOT about the cases where a user just puts files on a usb or uploads it to the cloud when they quit or something.
We do not work those type of cases.
We do not work those type of cases.
• • •
Missing some Tweet in this thread? You can try to
force a refresh