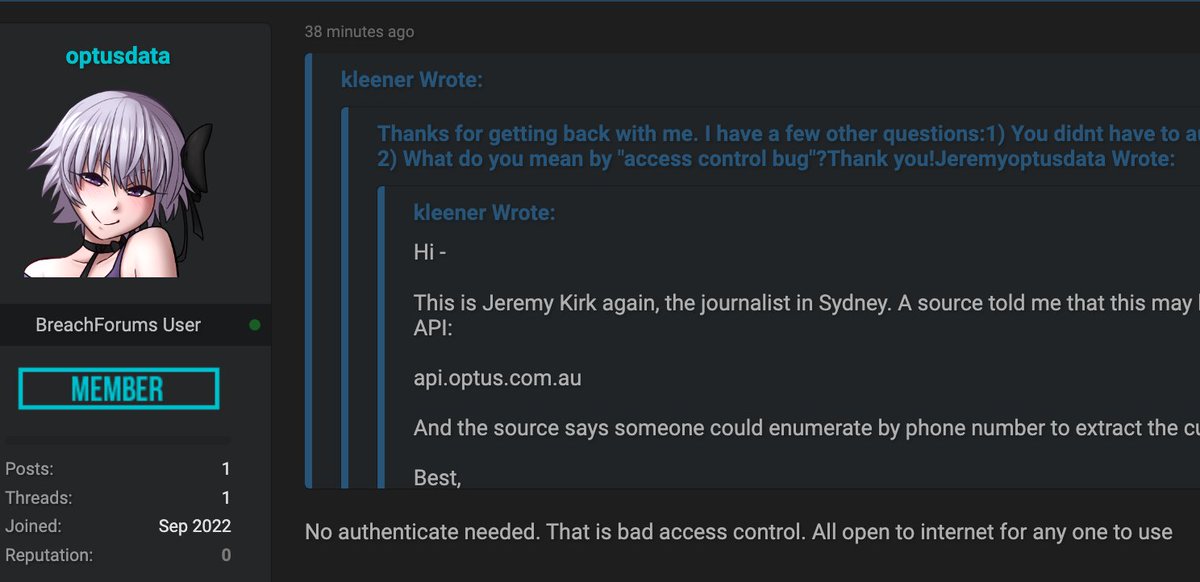
Someone is claiming responsibility for the recent hack of MyDeal, the online marketplace owned by Aussie grocery Woolworths Group. The price for the data is at $600. CAUTION: I haven't verified the data yet or if this is legit. #infosec #auspol
https://twitter.com/Cyberknow20/status/1581838827592699904
To recap, Woolworths said on Friday that 2.2 million people were affected after its CRM system was accessed. For 1.2 million, only email was exposed. For the rest, names, email addresses, phone numbers, delivery addresses, sometimes birth dates. PR here: woolworthsgroup.com.au/au/en/media/la…
This is the first screenshot that the person claims is proof of access to MyDeal's AWS. Sean Senvirtne is the founder and CEO of MyDeal. Anyone have thoughts on what this may or may not show? #infosec 

The person also published this screenshot on Saturday, writing "will leak some of the data soon." Seems to show access to MyDeal's Atlassian. URL is mydeal.atlassian[dot]net. Ironically what's open is the cyber security policy and breach response wiki. #auspol
@woolworths
@woolworths

Woolworth's media team says they're unlikely to have a comment today on this MyDeal development but probably will by tomorrow morning. #auspol
The attacker shared with me a network infrastructure map for Woolworths MyDeal. It's too sensitive to post a screenshot. It's a complex diagram of how MyDeal is put together, from SaaS services, e-commerce systems, payments, dev systems to the CRM system that was hacked.
The MyDeal attacker says they're only asking $600 for the data because it's not that valuable to cyber criminals. This is right because there's just so much data like this already out there (there's no passport/DL numbers, financial info or passwords in the data).
The Woolworths MyDeal attacker also says they sent an email to around a dozen people who work at MyDeal asking for $20K in exchange for a promise to delete the data. It doesn't appear that MyDeal responded. #infosec #auspol #databreaches
Last tweet before I sign off here. The Woolworths MyDeal attacker says they also took source code from MyDeal's Bitbucket. Additionally, they did a bit of trolling in MyDeal's Zendesk customer support system, as exhibited in this screenshot that references @troyhunt. #infosec 

@troyhunt The Woolworths @mydealaustralia attacker released a 500-line data sample a few minutes ago. #auspol #databreach #Australia #infosec 

The Woolworths Group MyDeal data has now been marked as "sold" on the data leak forum. The attacker writes on Telegram that "the MyDeal DB has been sold won't be selling anymore copies." #auspol #infosec
Adding to the thread a link to a story I wrote today that wraps the MyDeal situation into all of the other activity going on in Australia now related data breaches - @vinomofo, @optus and @medibank: bankinfosecurity.com/new-data-leaks…
• • •
Missing some Tweet in this thread? You can try to
force a refresh