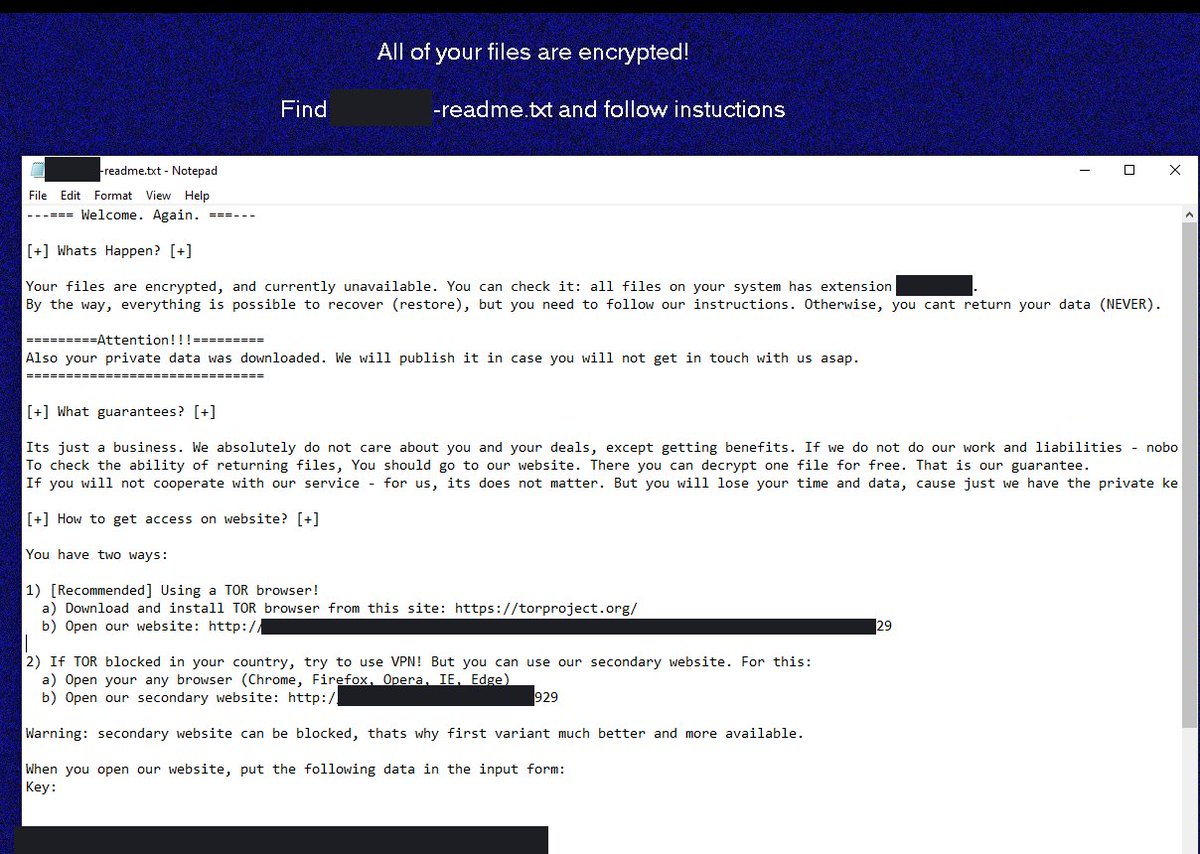
Follina Exploit Leads to Domain Compromise
➡️Initial Access: Word Doc exploiting Follina
➡️Persistence: Scheduled Tasks
➡️Discovery: ADFind, Netscan, etc.
➡️Lat Movement: SMB, Service Creation, RDP
➡️C2: #CobaltStrike, Qbot, NetSupport, Atera/Splashtop
thedfirreport.com/2022/10/31/fol…
➡️Initial Access: Word Doc exploiting Follina
➡️Persistence: Scheduled Tasks
➡️Discovery: ADFind, Netscan, etc.
➡️Lat Movement: SMB, Service Creation, RDP
➡️C2: #CobaltStrike, Qbot, NetSupport, Atera/Splashtop
thedfirreport.com/2022/10/31/fol…
Analysis and reporting completed by @pigerlin, @yatinwad and @_pete_0.
Shout outs to @CISAgov, @GossiTheDog, @msftsecresponse, @malware_traffic and @sans_isc.
Shout outs to @CISAgov, @GossiTheDog, @msftsecresponse, @malware_traffic and @sans_isc.
IOC's for intrusion, dated June 2022
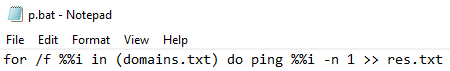
Maldoc:
doc532.docx
03ef0e06d678a07f0413d95f0deb8968190e4f6b
Qbot Dll:
liidfxngjotktx.dll
dab316b8973ecc9a1893061b649443f5358b0e64
Netsupport Client
client32.exe
3112a39aad950045d6422fb2abe98bed05931e6c
Maldoc:
doc532.docx
03ef0e06d678a07f0413d95f0deb8968190e4f6b
Qbot Dll:
liidfxngjotktx.dll
dab316b8973ecc9a1893061b649443f5358b0e64
Netsupport Client
client32.exe
3112a39aad950045d6422fb2abe98bed05931e6c
Qbot C2:
144.202.3[.]39:443
67.209.195[.]198:443
176.67.56[.]94:443
72.252.157[.]93:995
90.120.65[.]153:2078
72.252.157[.]93:990
86.97.9[.]190:443
37.34.253[.]233:443
23.111.114[.]52:65400
CobaltStrike C2
190.123.44[.]126:443
ATERA ID
cadencefitzp.atrickzx@gmail[.]com
144.202.3[.]39:443
67.209.195[.]198:443
176.67.56[.]94:443
72.252.157[.]93:995
90.120.65[.]153:2078
72.252.157[.]93:990
86.97.9[.]190:443
37.34.253[.]233:443
23.111.114[.]52:65400
CobaltStrike C2
190.123.44[.]126:443
ATERA ID
cadencefitzp.atrickzx@gmail[.]com
Detections:
➡️1 custom Qbot Sigma rule
➡️15 Sigma Detections
➡️14 Network Detections
➡️1 custom Qbot Sigma rule
➡️15 Sigma Detections
➡️14 Network Detections
• • •
Missing some Tweet in this thread? You can try to
force a refresh