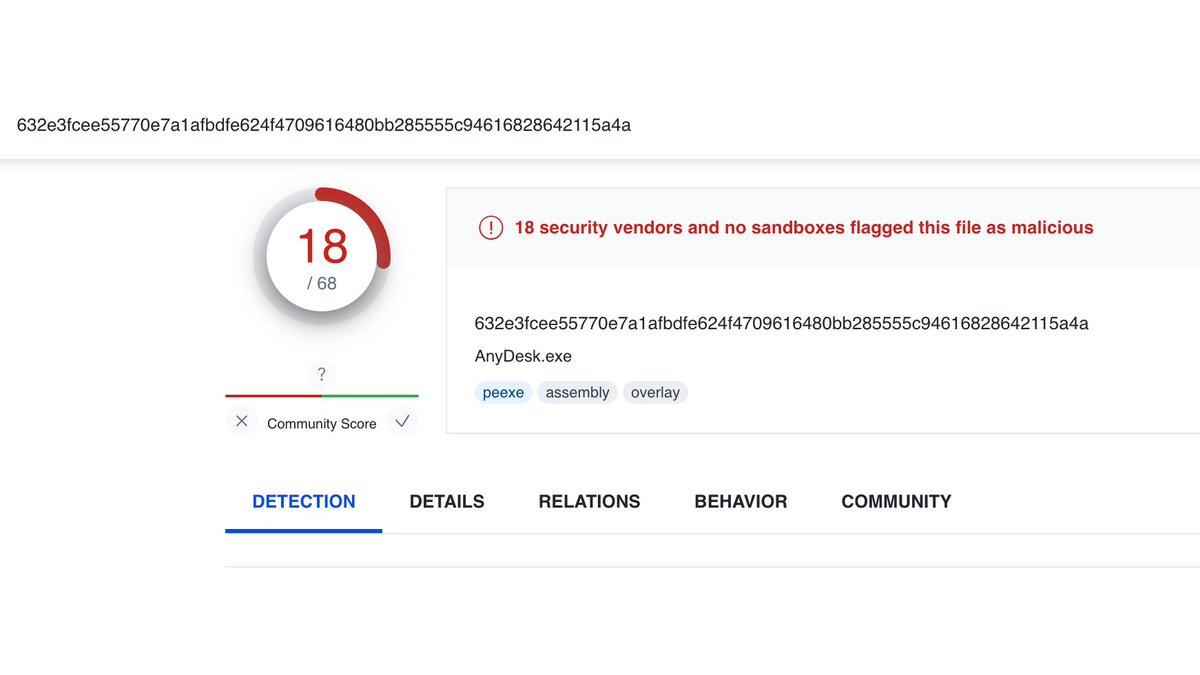
1/ #Azure In a recent case, the TA was able to compromise the user despite MFA (MFA fatigue).
After logging in, the attacker registered another mobile number as "Alternate Mobile Phone Call".
In the audit logs, we see this event within "Authentication Methods":
🧵 #DFIR
After logging in, the attacker registered another mobile number as "Alternate Mobile Phone Call".
In the audit logs, we see this event within "Authentication Methods":
🧵 #DFIR

2/ The audit logs are a goldmine for finding suspicious behavior in an Azure tenant.
If we filter by "Core Directory", "UserManagement" and "Update user" ..
If we filter by "Core Directory", "UserManagement" and "Update user" ..

3/ .. we also see the ModifiedProperties (the modifications done by the attacker).
Notice, the primary Phone Number is a Swiss mobile phone (+41), and the attacker added a number from the United Arab Emirates (+971).
Suspicious? You bet!
Notice, the primary Phone Number is a Swiss mobile phone (+41), and the attacker added a number from the United Arab Emirates (+971).
Suspicious? You bet!

4/ #ThreatHunting
We can export all MFA properties of users to search for users who have added or registered a second number or use a mobile number from a country without a branch office.
I use the code from the link below quite frequently:
morgantechspace.com/2018/06/find-a…
We can export all MFA properties of users to search for users who have added or registered a second number or use a mobile number from a country without a branch office.
I use the code from the link below quite frequently:
morgantechspace.com/2018/06/find-a…
• • •
Missing some Tweet in this thread? You can try to
force a refresh