1/ In a recent case, the TA installed DWservice as a backdoor. [1]
I installed the software on my test machine, which works incredibly well!
The screenshot shows the desktop from my lab machine, which I accessed from within the browser.
🤯
🧵 #CyberSecurity
I installed the software on my test machine, which works incredibly well!
The screenshot shows the desktop from my lab machine, which I accessed from within the browser.
🤯
🧵 #CyberSecurity

2/ The screenshot above depicts the content of the config.json file, which is located in the installation directory of DWservice, and could be interesting for LEA purposes (the key could be linked to an account).
Below is another screenshot with various features of the service.
Below is another screenshot with various features of the service.

3/ In our case, the path to the binary was C:\Programdata\DWAgent\native\dwagsvc.exe, but the path can be changed during installation.
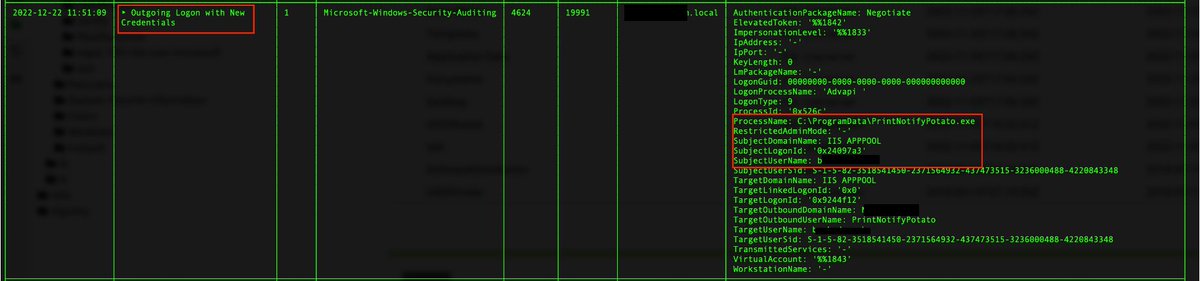
4/ In the EventLogs, the service installation and the start of the service are logged.
7045: A service was installed in the system. Service Name: DWAgent Service
7036: The DWAgent service entered the running state.
7045: A service was installed in the system. Service Name: DWAgent Service
7036: The DWAgent service entered the running state.
5/ @mgreen27's @velocidex Velociraptor Applications Artifact ("Bulk indicator hunt over Windows.Sys.Programs") also searches for installation of DWservice, among other known RMM solutions. 

6/ And: The file dwagent.log in the installation path records the IP address from the source host, which connects to the DWservice agent. 🕵️👮
References:
[1] dwservice.net
[2] github.com/mgreen27/Detec…
References:
[1] dwservice.net
[2] github.com/mgreen27/Detec…

• • •
Missing some Tweet in this thread? You can try to
force a refresh