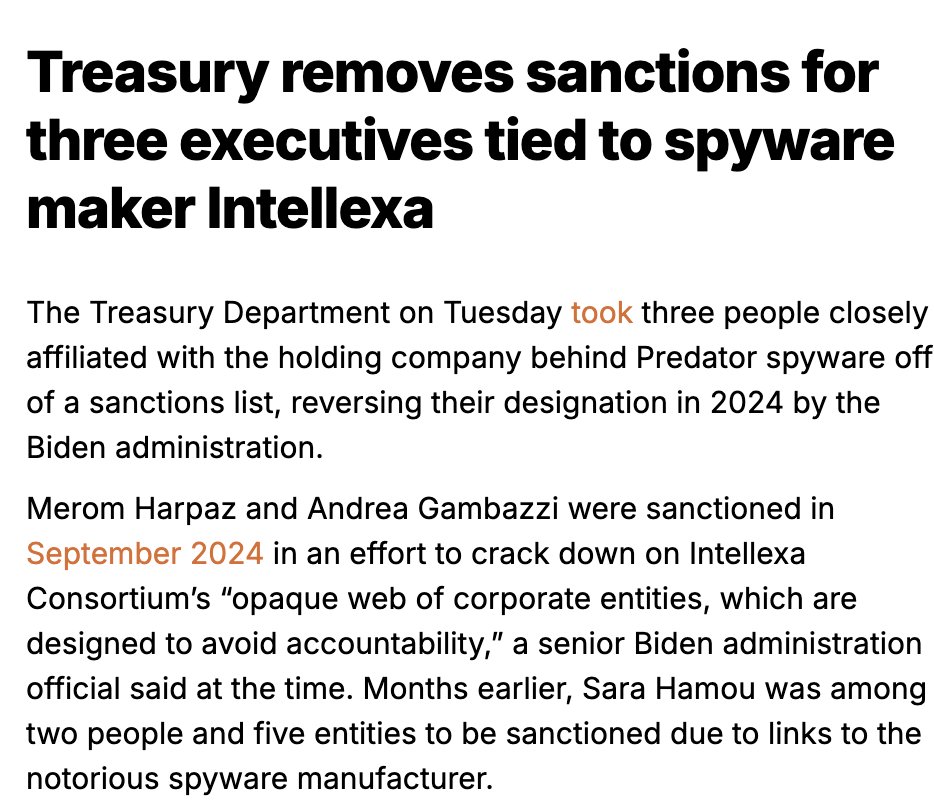
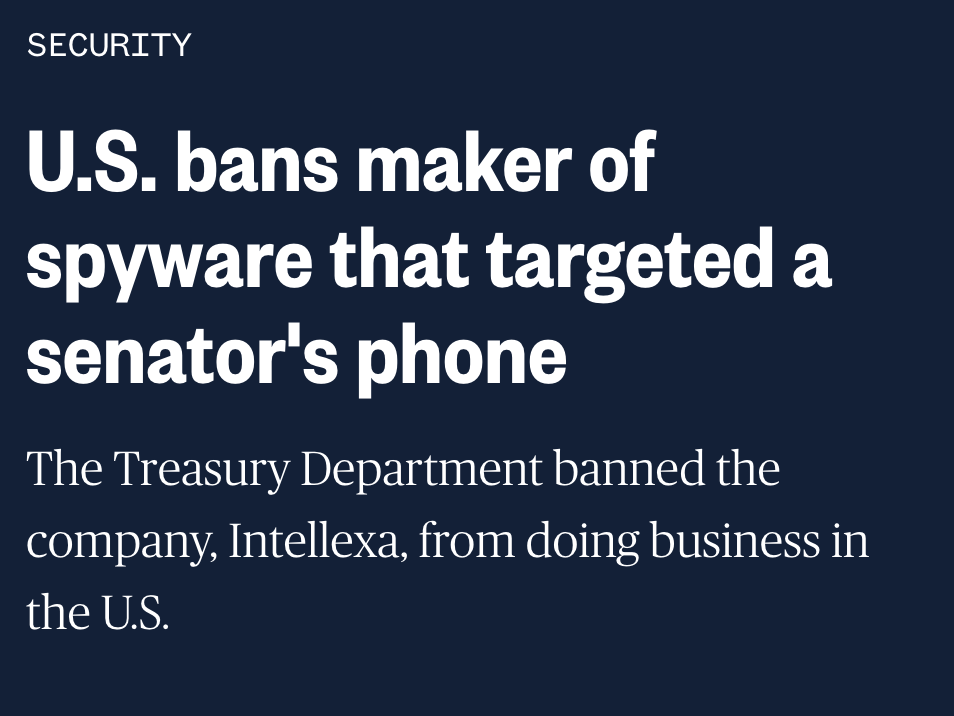
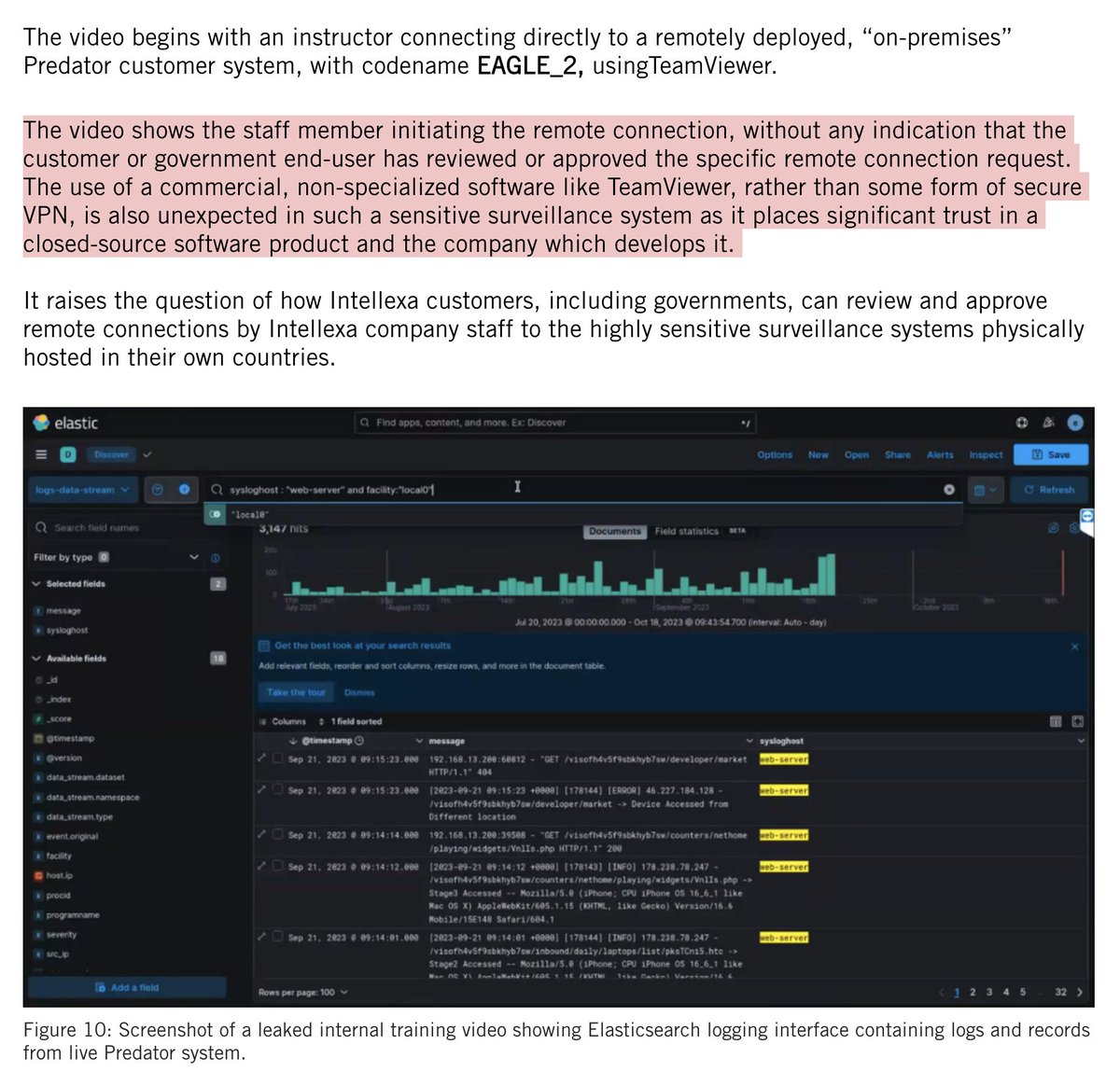
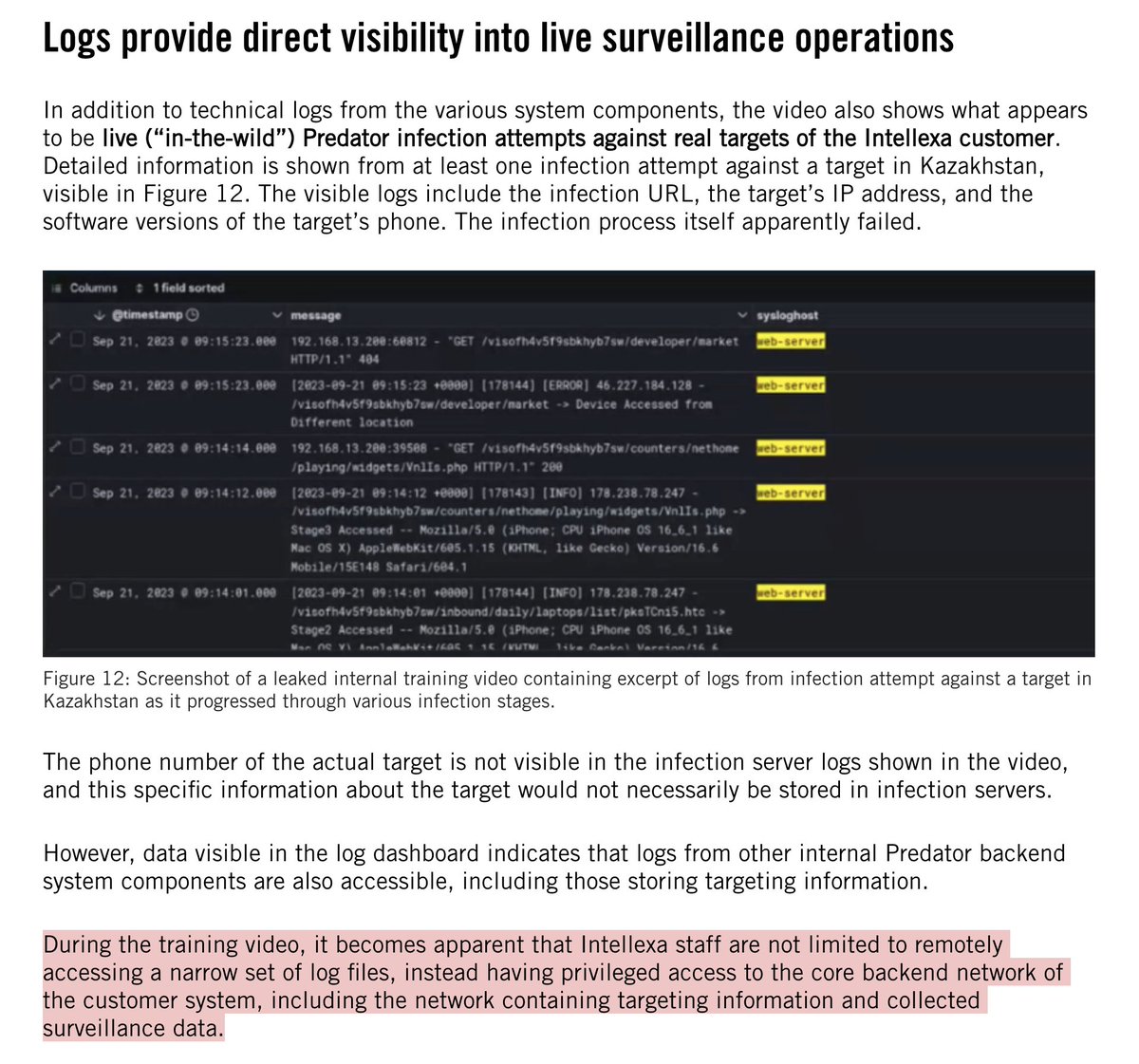
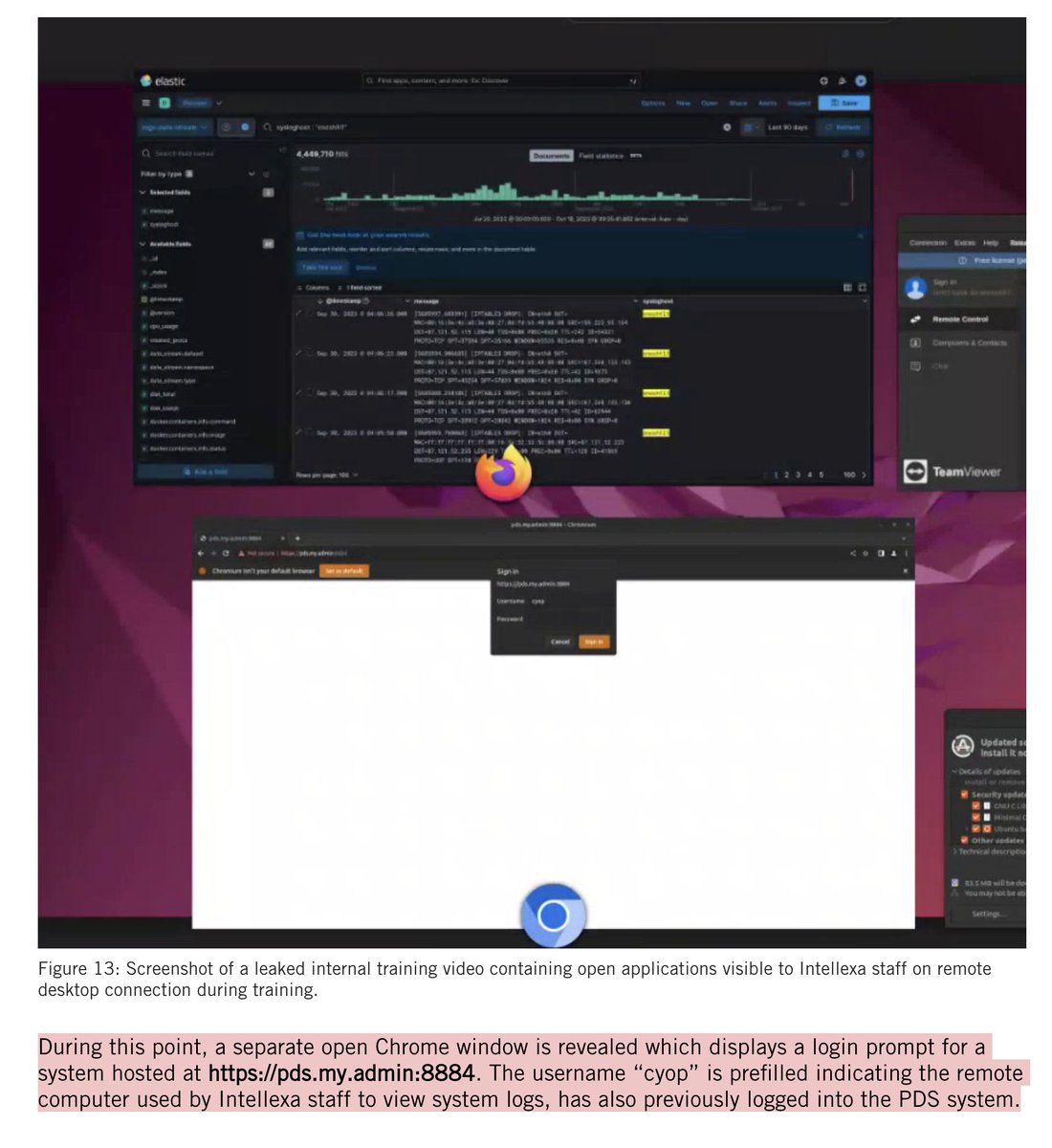
WHOA: Team of Israeli ex-spies boast of manipulating 33 elections w/ #hacking & #bots.
Tricked into demoing #telegram hacking & bot army to undercover investigators.
By @skirchy @manisha_bot @davidtpegg @carolecadwalla & @burke_jason
theguardian.com/world/2023/feb…



Tricked into demoing #telegram hacking & bot army to undercover investigators.
By @skirchy @manisha_bot @davidtpegg @carolecadwalla & @burke_jason
theguardian.com/world/2023/feb…


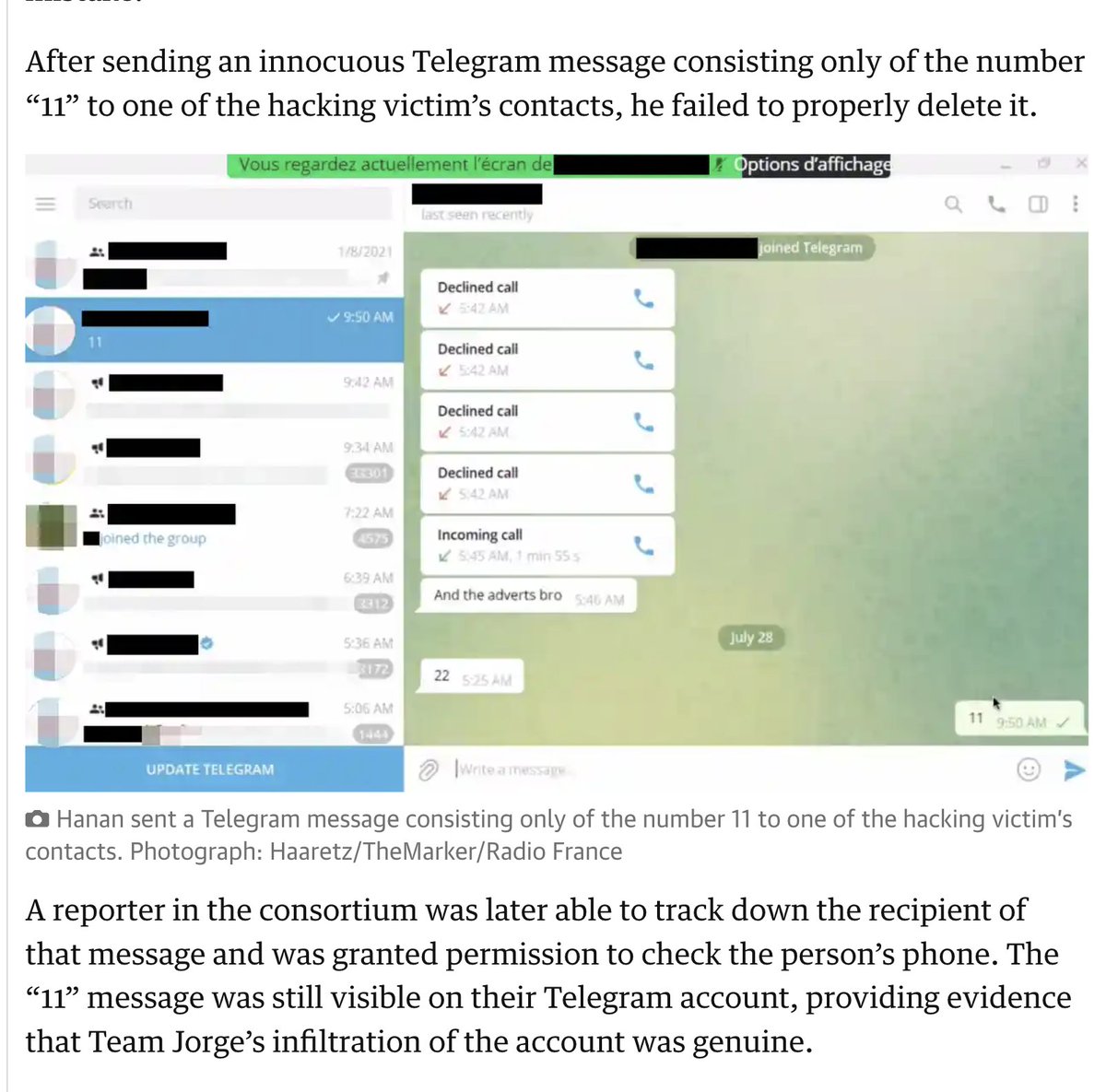

2/ “After you’ve created credibility, what do you do? Then you can manipulate"
Good to see @Meta take action on these accounts.
Honestly though we are at the absolute tip of the iceberg.

Good to see @Meta take action on these accounts.
Honestly though we are at the absolute tip of the iceberg.


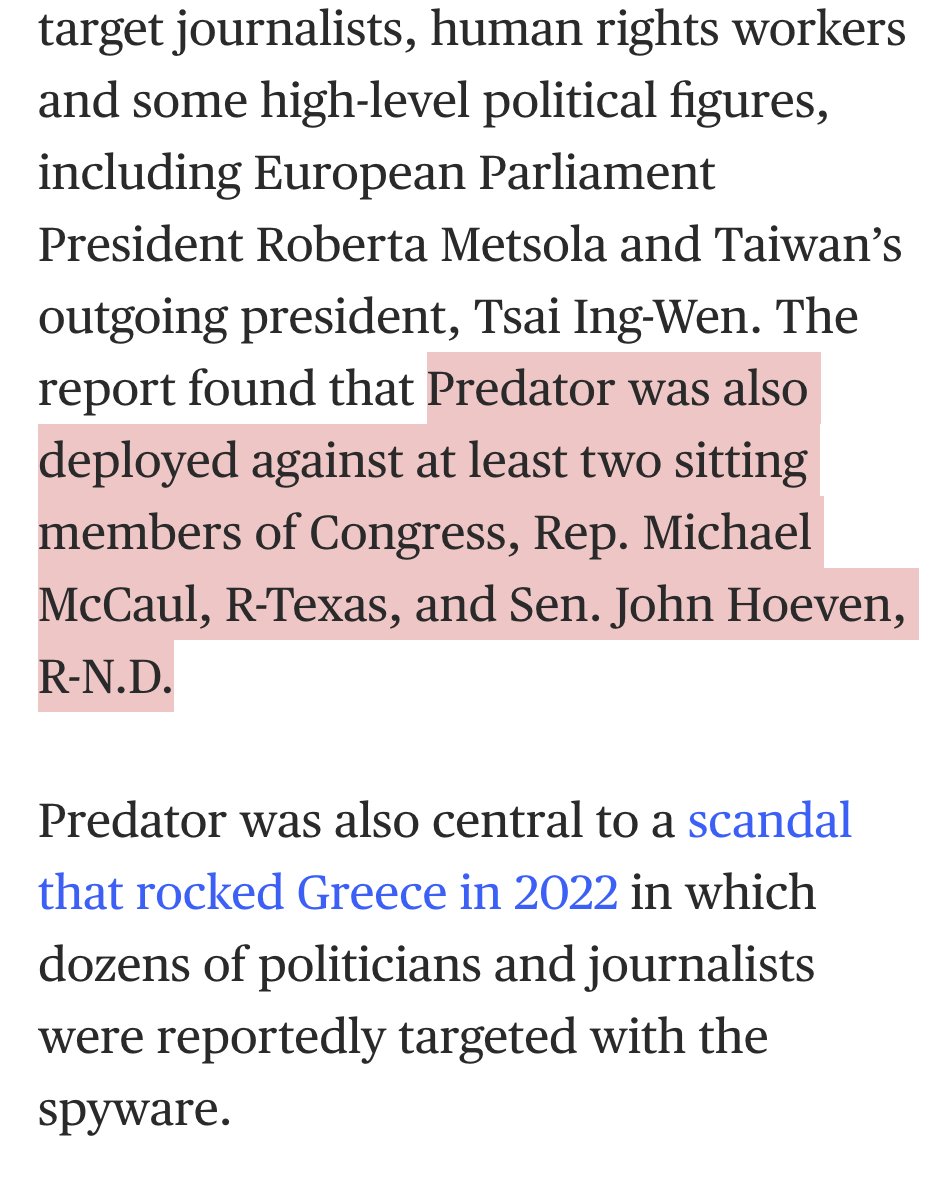
3/ Here he is demoing access to the #Gmail of a purported key political insider in #Kenya just days before the election.
This tech & tactics is kerosene on the flames of democracy.
This tech & tactics is kerosene on the flames of democracy.

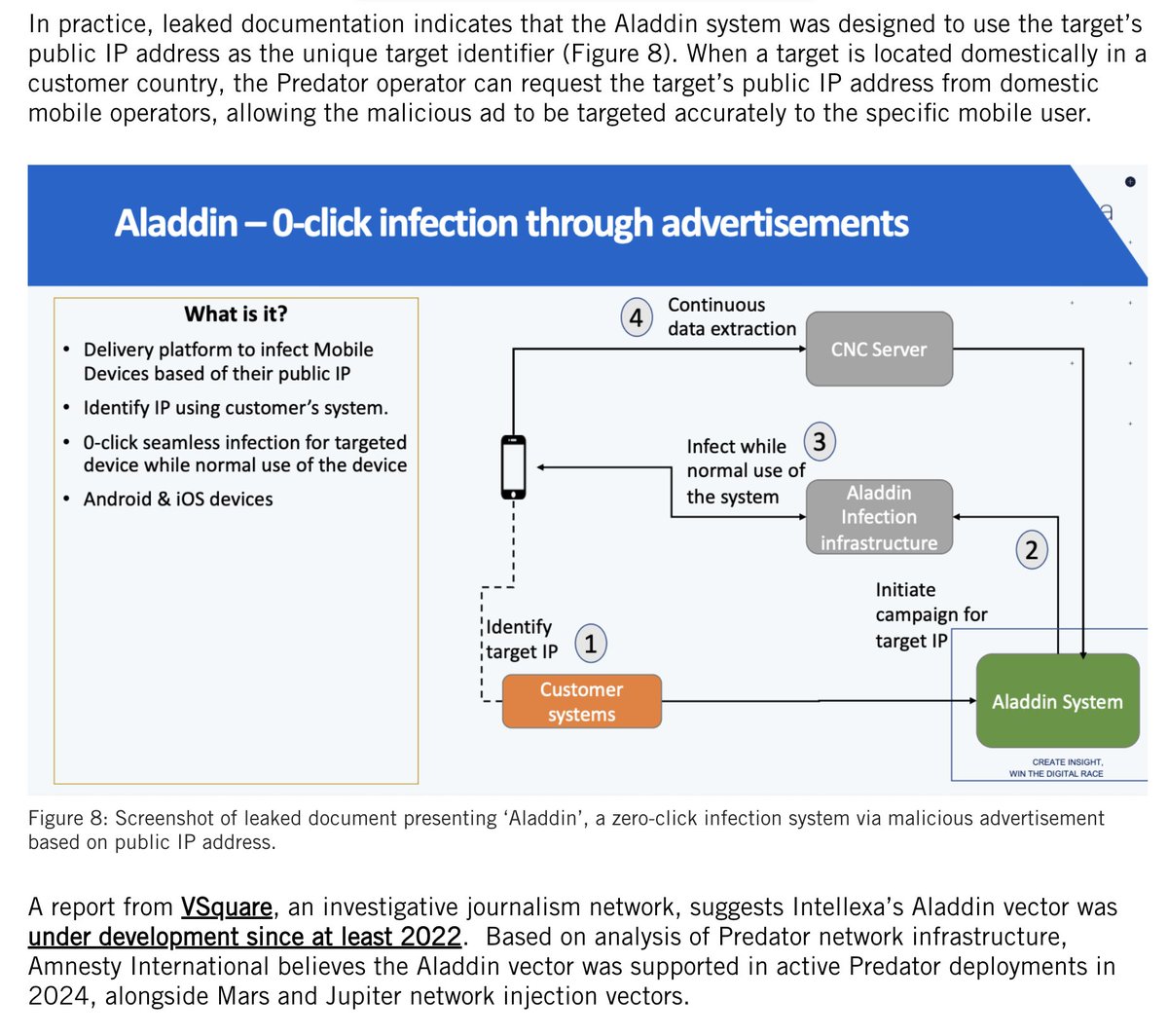
4/ “I know in some countries they believe #Telegram is safe. I will show you how safe it is”
Yikes.
Unclear how he is gaining access to these #Gmail & Telegram accounts, but the talk of #SS7 is a good hint.
And yet another reminder: SMS is not a safe second factor.

Yikes.
Unclear how he is gaining access to these #Gmail & Telegram accounts, but the talk of #SS7 is a good hint.
And yet another reminder: SMS is not a safe second factor.
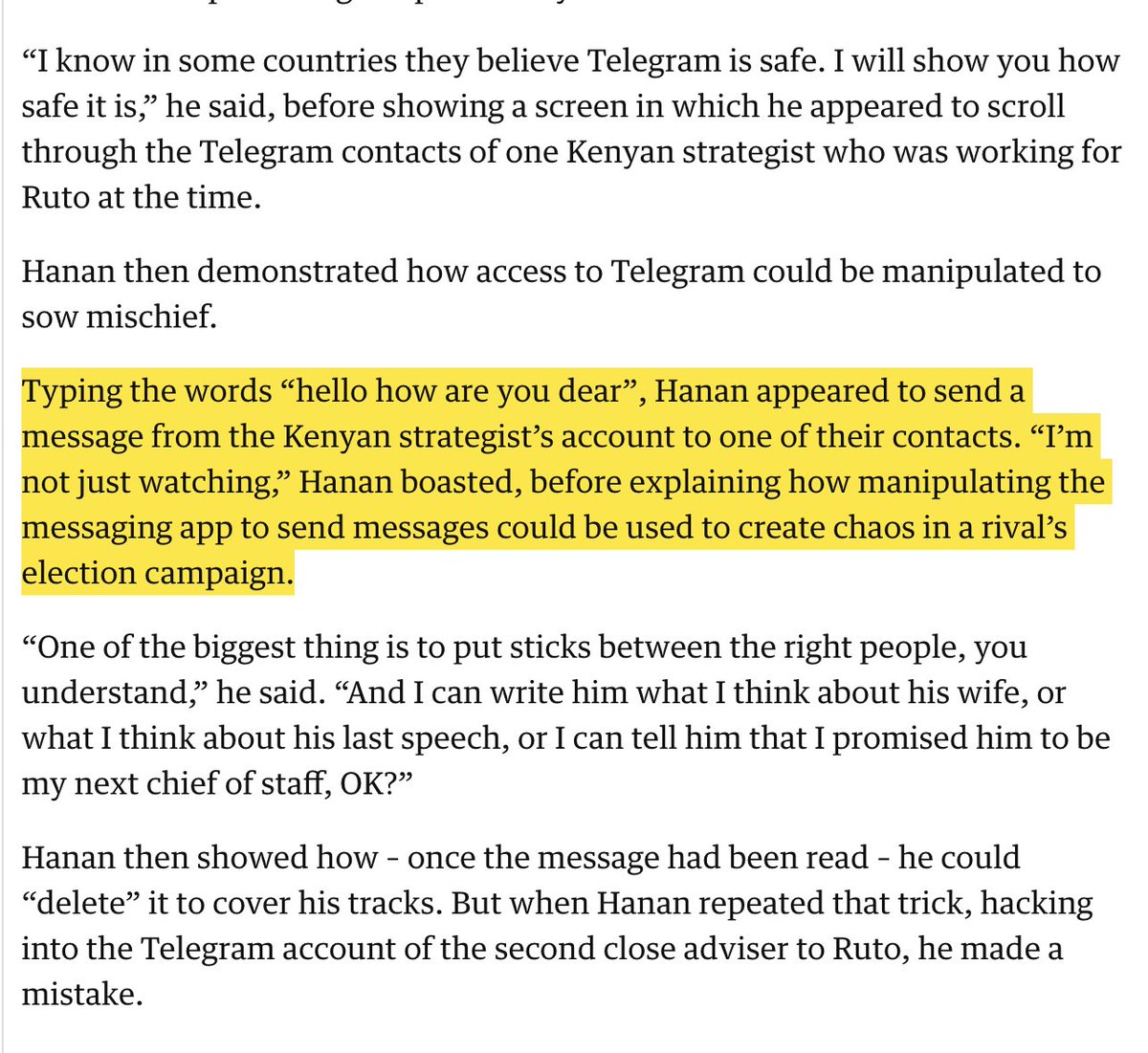

5/ Great to see mercenary election manipulators exposed. Solid journalism.
Trust me, this is a window into a *much bigger industry* active in elections around the world.
So rare to see it caught.
Trust me, this is a window into a *much bigger industry* active in elections around the world.
So rare to see it caught.
6/ The fact that so much political activity happens on a handful of platforms makes the tooling for political manipulation really interoperable.
Also radically lowers barriers to entry.
Making mercenary election manipulation scaleable & easy to export.
Also radically lowers barriers to entry.
Making mercenary election manipulation scaleable & easy to export.
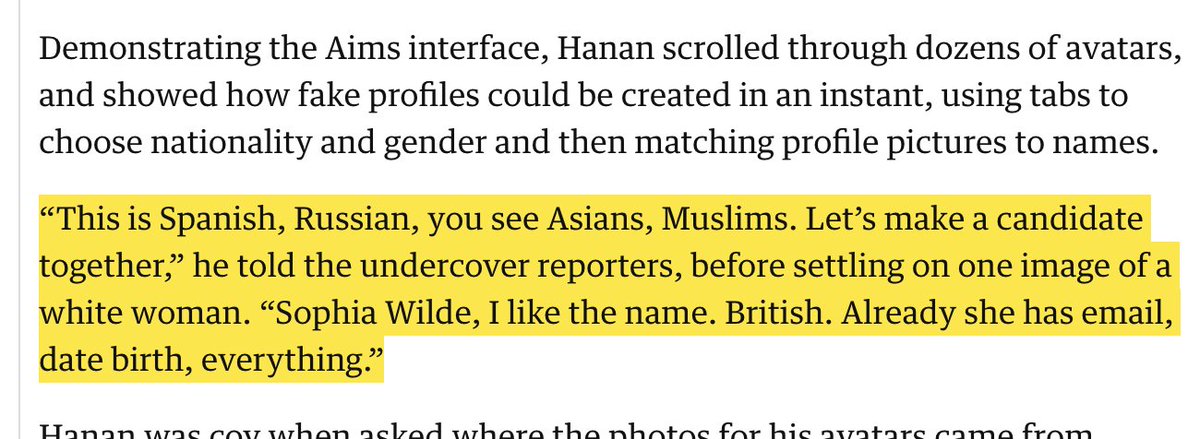
7/ Of course, we don't know whether these guys have successfully changed the outcome of any election.
The guy here is also pretty clearly boasting & trying to sell.
But the mere fact of mercenary election manipulators running around is damaging, even when they don't win.
The guy here is also pretty clearly boasting & trying to sell.
But the mere fact of mercenary election manipulators running around is damaging, even when they don't win.
8/ Even if mercenary election manipulators don't successfully throw an election (e.g. successfully shift mass sentiment), bots, hacking & turbocharged dirty tricks can distort political culture.
Opposing parties have to adjust.
And the net result is harm to democracy.
Opposing parties have to adjust.
And the net result is harm to democracy.
9/ UPDATE: @haaretzcom reports the mercenary political manipulators targeted 🇺🇸US politicians.
Like @GavinNewsom in #California
Topic: #diablocanyon nuclear plant
Were taxpayer funds routed to #TeamJorge for that op?
STORY haaretz.com/israel-news/se…



Like @GavinNewsom in #California
Topic: #diablocanyon nuclear plant
Were taxpayer funds routed to #TeamJorge for that op?
STORY haaretz.com/israel-news/se…




10/ Powerful coda to this remarkable story
https://twitter.com/avischarf/status/1625741253412364288
11/ Really remarkable undercover work went into this story.
Huge credit to @omerbenj @GurMegiddo & @FredMetzo for pulling off such a feat.
These are paranoid people confessing to illegal things, it cannot have been easy.
Huge credit to @omerbenj @GurMegiddo & @FredMetzo for pulling off such a feat.
These are paranoid people confessing to illegal things, it cannot have been easy.
https://twitter.com/omerbenj/status/1625771056488144897
• • •
Missing some Tweet in this thread? You can try to
force a refresh