Azure App Service Web Apps are yet another #Azure service that supports managed identity assignments.
Here's how attackers can use #BARK to abuse those assignments:
Here's how attackers can use #BARK to abuse those assignments:

There are at least 3 ways to achieve code execution on an Azure App Service Web App ("Azure Web App" from here on) instance:
1. The Kudu shell execution API endpoints
2. Poison deployment to include a web shell in the app
3. Find a cmd execution vulnerability in the deployed app
1. The Kudu shell execution API endpoints
2. Poison deployment to include a web shell in the app
3. Find a cmd execution vulnerability in the deployed app
We'll focus on #1 - abusing the built-in Kudu shell execution endpoints.
This is the feature the Azure GUI uses as its "Debug Console" and is documented here: github.com/projectkudu/ku…
@kfosaaen discussed this in his August 2020 blog post here: netspi.com/blog/technical…
This is the feature the Azure GUI uses as its "Debug Console" and is documented here: github.com/projectkudu/ku…
@kfosaaen discussed this in his August 2020 blog post here: netspi.com/blog/technical…
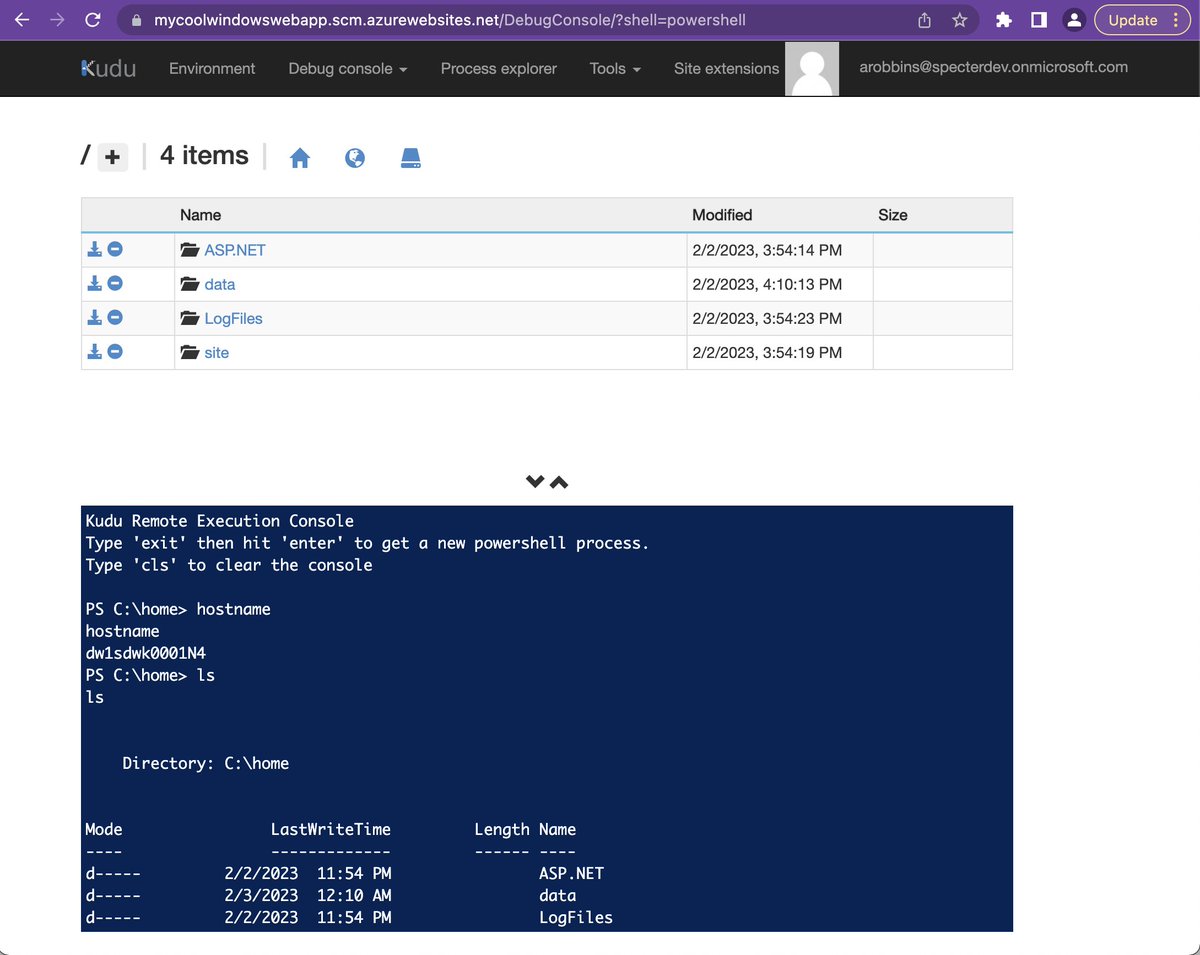
We can access this endpoint with either deployment credentials or an AzureRM-scoped JWT for a principal with Owner, Contributor, or Website Contributor role on the Web App.
You can use either with BARK's new cmdlet, Invoke-AzureRMWebAppShellCommand
You can use either with BARK's new cmdlet, Invoke-AzureRMWebAppShellCommand
Say you found clear-text application-scoped credentials for the Web App. Just base64-encode the username/password and provide that, the Kudu URI, and the command to Invoke-AzureRMWebAppShellCommand: 

If the Web App has a Managed Identity assignment, we can use Invoke-AzureRMWebAppShellCommand to extract a JWT for the Managed Identity Service Principal: 

As an attacker, we can now act as the service principal and gain whatever new privileges that service principal may have that we didn't have before.
Why should you care?
This is why:
Why should you care?
This is why:
https://twitter.com/_wald0/status/1621673654592630785
Want to know more? Check out my blog post from yesterday: medium.com/p/c3adefccff95
• • •
Missing some Tweet in this thread? You can try to
force a refresh