#ESETResearch analyze first in-the-wild UEFI bootkit bypassing UEFI Secure Boot even on fully updated Windows 11 systems. Its functionality indicates it is the #BlackLotus UEFI bootkit, for sale on hacking forums since at least Oct 6, 2022. @smolar_m welivesecurity.com/2023/03/01/bla… 1/11
BlackLotus brings legit but vulnerable binaries to the victim’s system (#BYOVD) to exploit #CVE-2022-21894 and bypass UEFI Secure Boot on up-to-date Windows systems. In some samples, these binaries are downloaded directly from the MS Symbol Store. cve.mitre.org/cgi-bin/cvenam… 2/11 

Although the vulnerability was fixed in Microsoft’s January 2022 update, its exploitation is still possible by bringing vulnerable drivers to the system, as the affected binaries have still not been added to the UEFI revocation list. msrc.microsoft.com/update-guide/e… 3/11
After exploitation, the bootkit’s persistence is set up by: 1. Enrolling attacker’s own self-signed public key certificate (MOK key) to the MokList NVRAM variable. 2. By using legitimate Microsoft-signed shim to load the bootkit - a UEFI app signed by that enrolled key. 4/11 



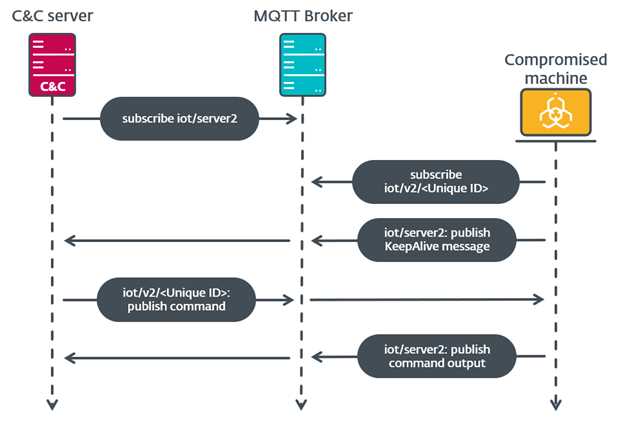
Once installed, the bootkit’s main goal is to deploy a kernel driver (which, among other things, protects the bootkit against removal), and an HTTP downloader responsible for communication with the C&C and capable of loading additional user-mode or kernel-mode payloads. 5/11 

The following files – deployed to the \EFI\Microsoft\Boot folder on EFI System partition by the BlackLotus installer – are protected against removal by the BlackLotus kernel driver: winload.efi, grubx64.efi and bootmgfw.efi. 6/11 

Additionally, BlackLotus can disable built-in Windows security protections such as Hypervisor-protected Code Integrity (HVCI), BitLocker, Windows Defender, and bypass User Account Control (UAC). 7/11 



Interestingly, the code decrypts but never uses various strings – including a message for the well-known security researcher @hasherezade, or just some random quotes – e.g, from the @UnderTale RPG game. 8/11 





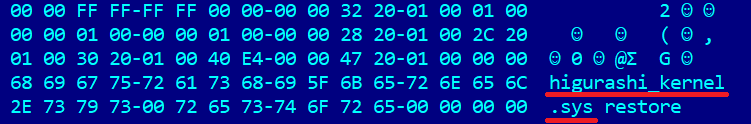
Although we believe this is the BlackLotus bootkit, we found no reference to that name in the samples we analyzed. Instead, some of the bootkit’s components’ names and self-signed certificate refer to the Higurashi When They Cry anime series. en.wikipedia.org/wiki/Higurashi… 9/11 




For more technical details about the BlackLotus UEFI bootkit, CVE-2022-21894 exploitation, and BlackLotus mitigation tips, read our blogpost: BlackLotus UEFI bootkit: Myth confirmed. welivesecurity.com/2023/03/01/bla… 10/11
IoCs available on our Github: github.com/eset/malware-i… 11/11
• • •
Missing some Tweet in this thread? You can try to
force a refresh