
1/ I presented 10 #ActiveDirectory hardening measures a few weeks ago, and I will tweet my recommendations in the next ten days.
The list is neither prioritised nor complete, but it might give companies and administrators good input on improving (AD) security.
🧵 #CyberSecurity
The list is neither prioritised nor complete, but it might give companies and administrators good input on improving (AD) security.
🧵 #CyberSecurity
2/ Number #1 of the Active Directory hardening measures:
#ADCS (Active Directory Certificate Services)
#ADCS (Active Directory Certificate Services)

3/ The whitepaper Certified Pre-Owned: Abusing Active Directory Certificate Services by Will Schroeder and Lee Christensen showcased new possibilities and attack vectors to gain domain administrative rights as an attacker. [1] 

4/ Attackers (and we as Defenders!) can use the Certify tool published by @SpecterOps to find vulnerable certificates.
Below are parts of a vulnerable certificate (from [2]).
Below are parts of a vulnerable certificate (from [2]).

5/ In the screenshot above, we see ENROLLEE_SUPPLIES_SUBJECT, which means the user requesting a new certificate based on this template can request a certificate for any user, including domain admins! 🤯
6/ Client Authentication at PkiExtendedKeyUsage means that the newly created certificate, based on this template, can also be used for authentication against computers in AD.
7/ Based on "Enrollment Rights: NT Authority\Authenticated Users," any authenticated user can create a new certificate based on this template.
8/ Further details and more profound descriptions can be found in [2]. 📖
9/ "Once the vulnerable certificate template has been identified, we can request a new certificate on behalf of a domain administrator using Certify." [2] 

10/ "Once we have the certificate in cert.pfx, we can request a Kerberos TGT for the user for which we minted the new certificate." [2] 
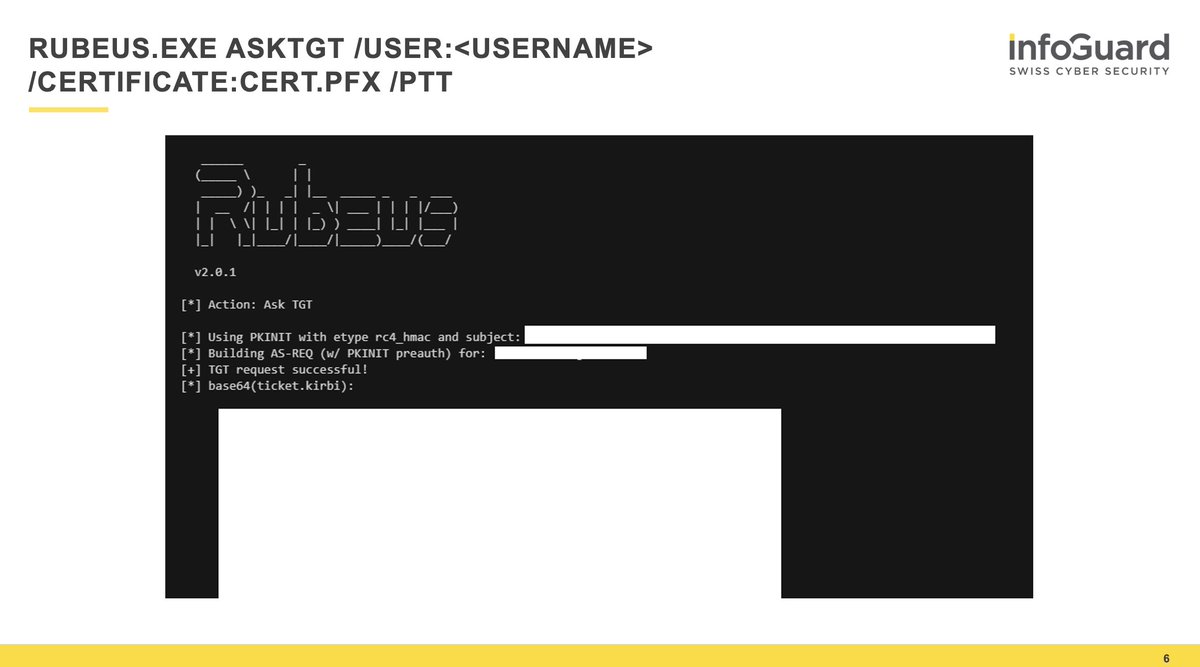
11/ In a nutshell - it's practically game over at this point.
More attacks against vulnerable certificates exist than outlined here (check the original whitepaper from SpecterOps), and there is constant research in this area.
More attacks against vulnerable certificates exist than outlined here (check the original whitepaper from SpecterOps), and there is constant research in this area.

12/ In our AD assessments, we find regularly vulnerable certificates.
In discussions with customers, it becomes clear that this topic is still too little known among administrators and IT security personnel.
A circumstance that needs to be changed.
In discussions with customers, it becomes clear that this topic is still too little known among administrators and IT security personnel.
A circumstance that needs to be changed.
13/ As always, we cannot protect our networks 100%, but we should raise the bar as high as possible, eliminating vulnerable certificates and misconfigurations in our AD Certificate Services.
• • •
Missing some Tweet in this thread? You can try to
force a refresh















