1/ Number #6 of the #ActiveDirectory hardening measures:
Privileges and Permissions
🧵 #CyberSecurity
Privileges and Permissions
🧵 #CyberSecurity

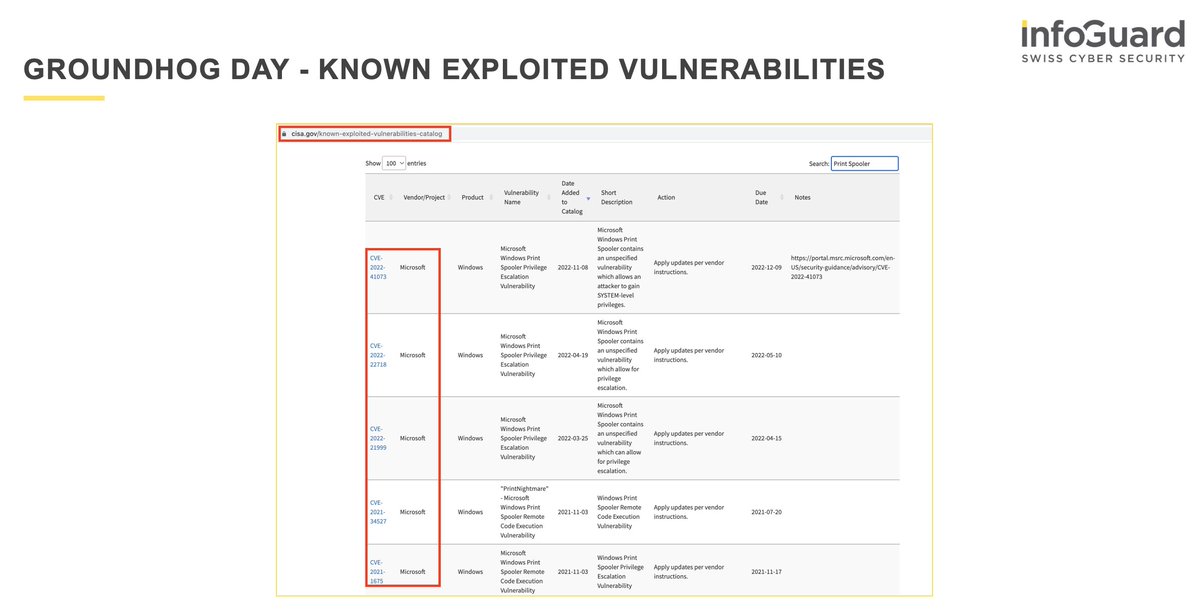
2/ #PingCastle lists, among many other things, the privileges assigned to domain users via GPOs.
The screenshot shows that the Default Notebook Policy grants Domain Users the SeLoadDriverPrivilege privilege.
Why is this bad?
The screenshot shows that the Default Notebook Policy grants Domain Users the SeLoadDriverPrivilege privilege.
Why is this bad?

3/ As @0xdf put it:
"If I can load a driver, I can load a vulnerable driver, and then exploit it." [1]
I know that some EDR's raise an alert when a vulnerable driver is loaded or dropped to disk, as such a driver could be exploited for a LPE.
"If I can load a driver, I can load a vulnerable driver, and then exploit it." [1]
I know that some EDR's raise an alert when a vulnerable driver is loaded or dropped to disk, as such a driver could be exploited for a LPE.
4/ Excerpt from the new @Volexity blog:
"A userland application cannot modify kernel memory, so the malware authors include a vulnerable driver, RTCore64.sys, to read and write into this protected memory space." [4]
"A userland application cannot modify kernel memory, so the malware authors include a vulnerable driver, RTCore64.sys, to read and write into this protected memory space." [4]
5/ "This technique of using an older, vulnerable driver to load malicious code was famously used by Turla for the purposes of loading a malicious rootkit. A public GitHub repository, KDU, owned by hFiref0x,
6/ documents a list of drivers that can be abused for this “Bring Your Own Vulnerable Driver” (BYOVD) technique." [4]
7/ "Access Control Lists (ACL) misconfiguration is one of the most common issues DART finds in Active Directory environments.
Active Directory ACLs are exceptionally granular, complex, and easy to configure incorrectly." [2]
Active Directory ACLs are exceptionally granular, complex, and easy to configure incorrectly." [2]

8/ "GenericAll – this privilege is the same as Full Control access.
If a user was compromised and that user had GenericAll over a highly privileged group, then the threat actor could add additional members to that group." [2]
If a user was compromised and that user had GenericAll over a highly privileged group, then the threat actor could add additional members to that group." [2]
9/ "WriteDacl – this privilege allows manipulation of the ACL on an object.
With this privilege a threat actor can change the ACL on an object such as a group. If a user was compromised and that user had WriteDacl over a highly privileged group,
With this privilege a threat actor can change the ACL on an object such as a group. If a user was compromised and that user had WriteDacl over a highly privileged group,
10/ the threat actor could add a new ACL to that group. That new ACL could then give them access to add additional members to the group, such as themselves." [2]
11/ We, as defenders, can proactively check for such misconfigurations, for example, with PowerView. [3]
🔍
🔍

13/ References:
[1] 0xdf.gitlab.io/2020/10/31/htb…
[2] techcommunity.microsoft.com/t5/microsoft-s…
[3] ired.team/offensive-secu…
[4] volexity.com/blog/2023/03/0…
[1] 0xdf.gitlab.io/2020/10/31/htb…
[2] techcommunity.microsoft.com/t5/microsoft-s…
[3] ired.team/offensive-secu…
[4] volexity.com/blog/2023/03/0…
• • •
Missing some Tweet in this thread? You can try to
force a refresh