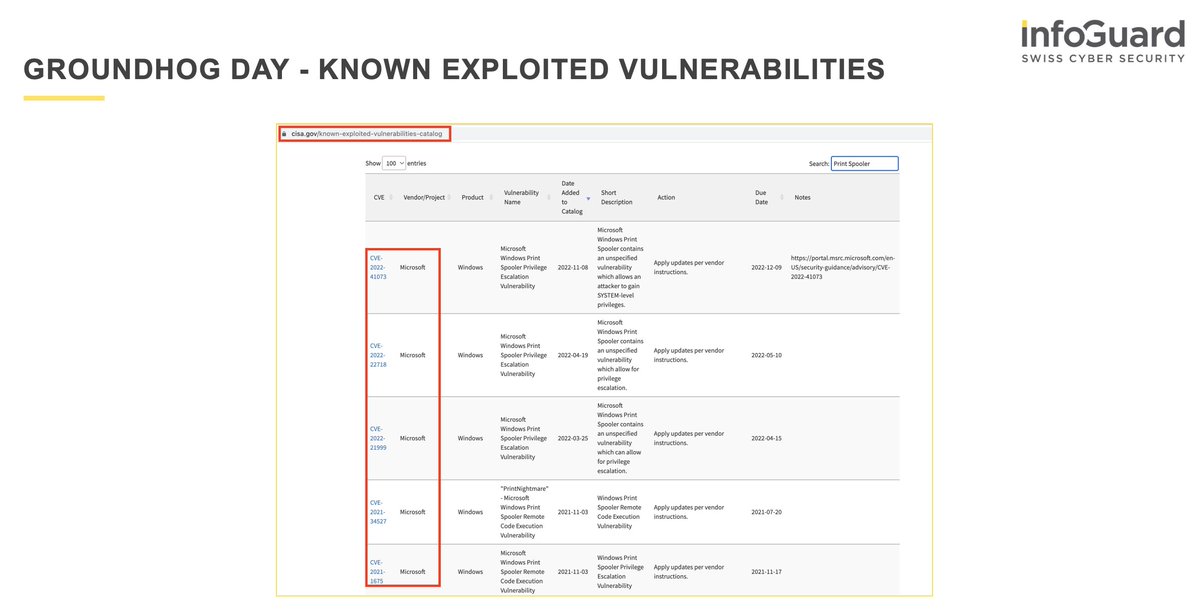
2/ There exists a ton of different techniques of how attackers can relaying credentials to another host in order to raise their privileges or get a shell on the target server. 

3/ @TrustedSec has written an excellent blog post about the different relaying techniques, how they work and which prerequisites have to be in place that the attack is successful. [1]
4/ "In order to assess the effectiveness of relaying attacks, we will need to learn more about our network environment. In order to succeed with ‘classic’ relaying attacks, some prerequisites must be met: 

6/ There must be broadcast traffic in the environment. Classic examples of this are DNS replacement protocols like Link Local Multicast Name Resolution (LLMNR) and NetBIOS Name Resolution (NBT-NS)." [1]
7/ As you might have read the blog and realised that attackers (again!) have different techniques at hand, how can we protect our network against these techniques?
One solution is to enable SMB signing, as this will prevent relaying because all SMB traffic must be signed.
One solution is to enable SMB signing, as this will prevent relaying because all SMB traffic must be signed.

8/ We can not only enable SMB signing, but also LDAP signing.
And of course, disable Windows Proxy Auto Detection (WPAD) and LLMNR/NBNS (#PingCastle check).
And of course, disable Windows Proxy Auto Detection (WPAD) and LLMNR/NBNS (#PingCastle check).

• • •
Missing some Tweet in this thread? You can try to
force a refresh