1/ Number #10 of the #ActiveDirectory hardening measures:
Easy Wins (for Attackers)
🧵 #CyberSecurity
Easy Wins (for Attackers)
🧵 #CyberSecurity

This is the last thread in this AD hardening measure series, but there would still be so much to discuss 😅
Here are more points you should focus on to defend your networks even better.
Here are more points you should focus on to defend your networks even better.

"Administrative accounts should never be enabled for delegation.
You can prevent these privileged accounts from being targeted by enabling the ‘Account is sensitive and cannot be delegated’ flag on them. You can optionally add these accounts to the ‘Protected Users’ group.
You can prevent these privileged accounts from being targeted by enabling the ‘Account is sensitive and cannot be delegated’ flag on them. You can optionally add these accounts to the ‘Protected Users’ group.
This group provides protections over and above just preventing delegation and makes them even more secure; however, it may cause operational issues, so it is worth testing in your environment." [1]
#PingCastle check below ⤵️
#PingCastle check below ⤵️

"It is not uncommon for DART to engage with customers where accounts have weak or easy to guess credentials, including those of privileged users such as Domain Admins.
Simple password spray attacks can lead to the compromise of such accounts." [1]
#PingCastle check below ⤵️
Simple password spray attacks can lead to the compromise of such accounts." [1]
#PingCastle check below ⤵️

"If you are licensed for Azure Active Directory P1 or higher, you can also deploy Azure Active Directory Password Protection, which can disallow your users from using easy to guess passwords even in on-premises Active Directory."
https://twitter.com/malmoeb/status/1517156950068260864
"An account can be set without a password if it has the flag "PASSWD_NOTREQD" set as "True" in the "useraccountcontrol" attribute. This represents a high security risk as the account is not protected at all without a password".
#PingCastle finding ⤵️
#PingCastle finding ⤵️

"Groups such as Account and Server Operators have wide ranging privilege over your Active Directory. For example, by default Server Operators can log on to Domain Controllers, restart services, backup and restore files, and more."
#PingCastle finding ⤵️
#PingCastle finding ⤵️
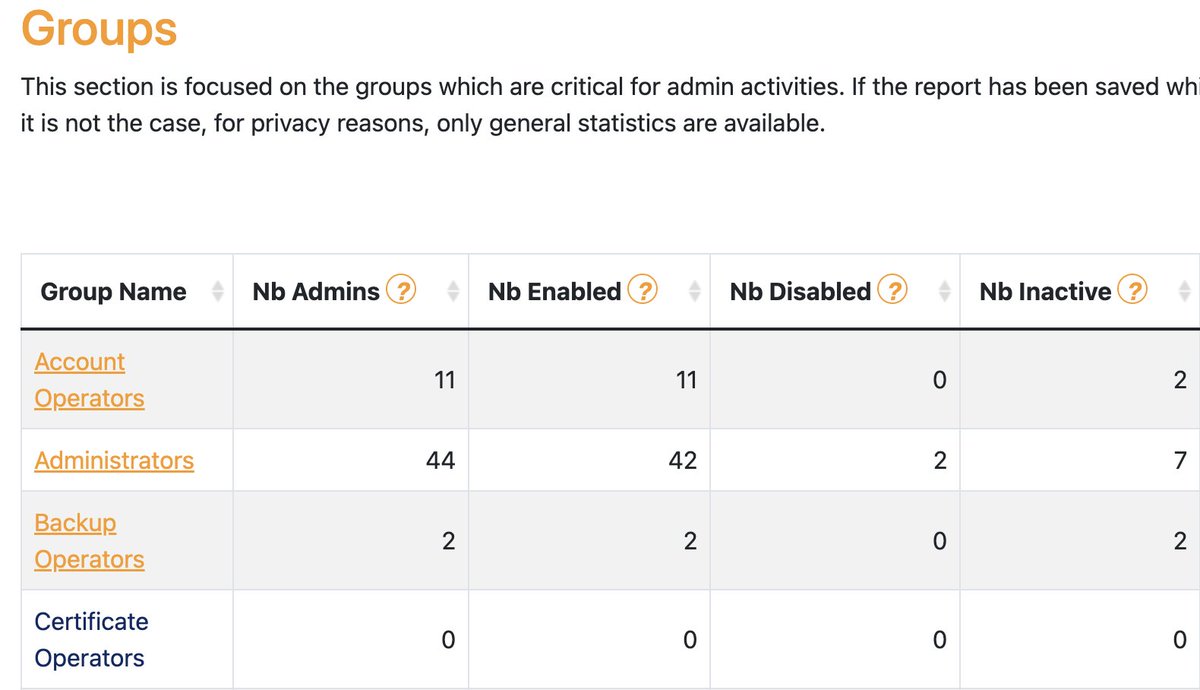
"It is recommended that, where possible, privileged built-in groups not contain any users. Instead, the appropriate privilege should be granted specifically to users that require it." [1]
Thanks for following me through this 10-day journey into hardening AD.
I want to use this thread to thank all the incredible people in our industry who have conducted the research and created the tools I presented in this series 💙
I really stand on the shoulders of giants 🙏
I want to use this thread to thank all the incredible people in our industry who have conducted the research and created the tools I presented in this series 💙
I really stand on the shoulders of giants 🙏

• • •
Missing some Tweet in this thread? You can try to
force a refresh