1/ The Rug Pull Report
Exit scams, more popularly known as rug pulls, are the most common type of #Web3 scam. A rug pull involves fraudsters robbing a crypto project by liquidating their holdings without warning and leaving investors holding worthless tokens. 🧵👇🏼
Exit scams, more popularly known as rug pulls, are the most common type of #Web3 scam. A rug pull involves fraudsters robbing a crypto project by liquidating their holdings without warning and leaving investors holding worthless tokens. 🧵👇🏼

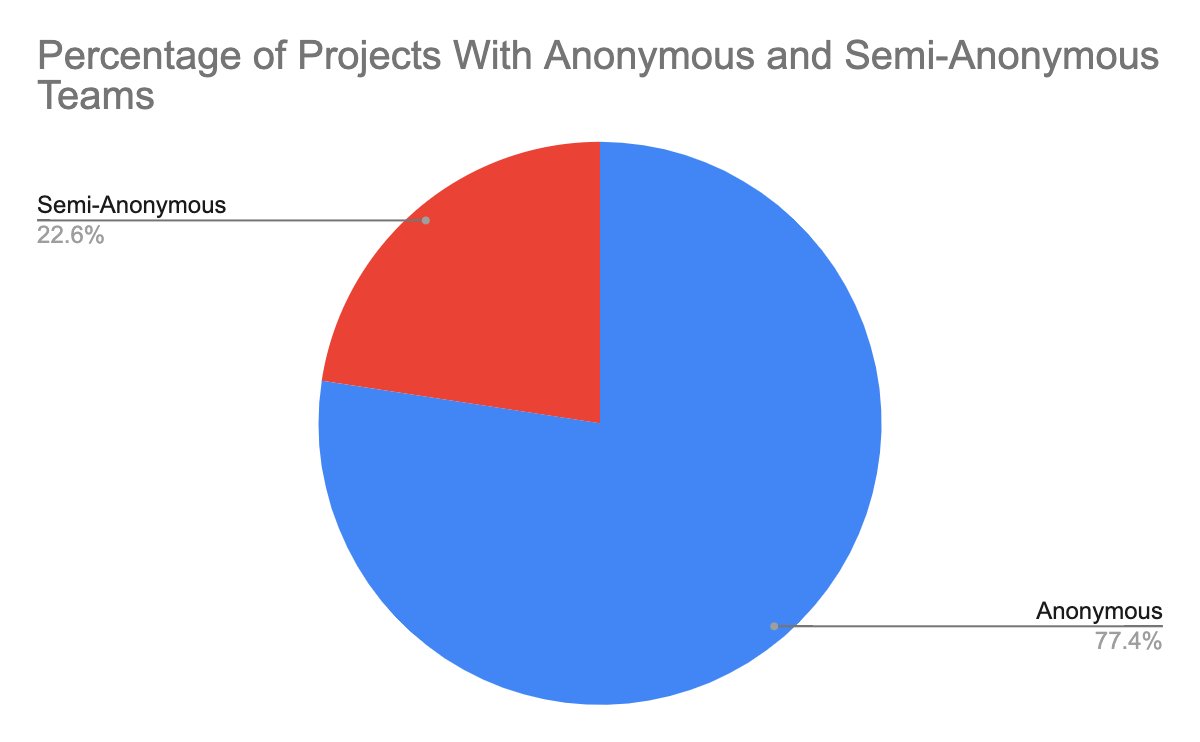
2/ 3️⃣1️⃣6️⃣rug pulls stole $207 million of value from #Web3 investors in 2022. 💰👎🏼The prevalence of this type of #scam is an ongoing blight on the image of the industry. 👇🏼
3/ In this report, we analyzed the common characteristics of rug pulls, from the domain registrars scammers prefer to the average length of projects designed to exit #scam. 👇🏼
4/ Teams accounted for nearly two-thirds of all rug pulls analyzed. Founders working alone represented 15% of exit scams, and rogue developers 10%. 👇🏼 

5/ We found that the average project that rug pulled existed for 9️⃣2️⃣ days from inception to the #scam. The median lifespan, or most common, was 5️⃣7️⃣ days from start to finish. 👇🏼
6/ Scammers employ tactics that exploit the emotional and physiological triggers in order to maximize investment into their project. 👇🏼 
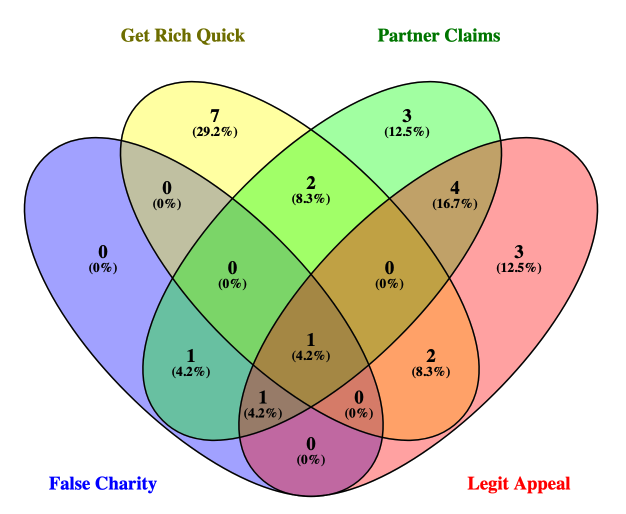
7/ Of the 3️⃣1️⃣ projects analyzed, only seven had roadmaps and only four published whitepapers. When they are available, these documents are often of poor quality, with grammatical errors, missing information, and even explicitly fraudulent messaging. 👇🏼
• • •
Missing some Tweet in this thread? You can try to
force a refresh