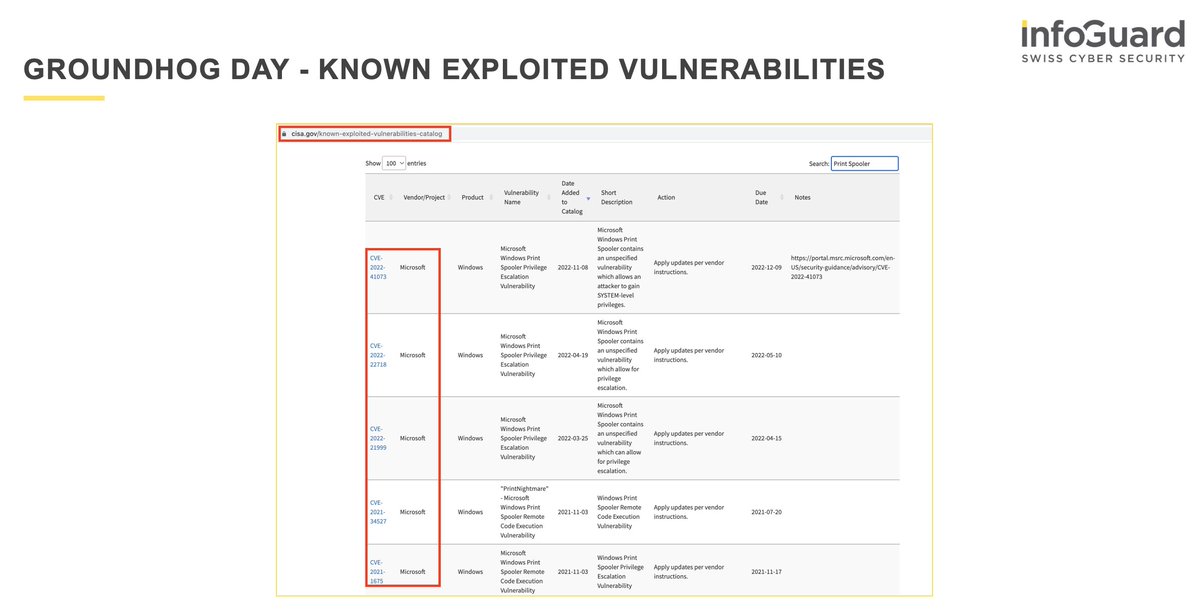
1/ Do you monitor newly created services within your environment, and would you notice when a (vulnerable) driver is loaded?
The screenshot below (#Velociraptor 🤩) is from a recent #XMRig CoinMiner investigation ⤵️
🧵 #CyberSecurity
The screenshot below (#Velociraptor 🤩) is from a recent #XMRig CoinMiner investigation ⤵️
🧵 #CyberSecurity
https://twitter.com/BushidoToken/status/1522525471182893056

2/ We talked about vulnerable drivers before:
https://twitter.com/malmoeb/status/1551449425842786306
4/ And Florian covers vulnerable drivers with #Sigma rules here:
https://twitter.com/cyb3rops/status/1552188055372578817
• • •
Missing some Tweet in this thread? You can try to
force a refresh