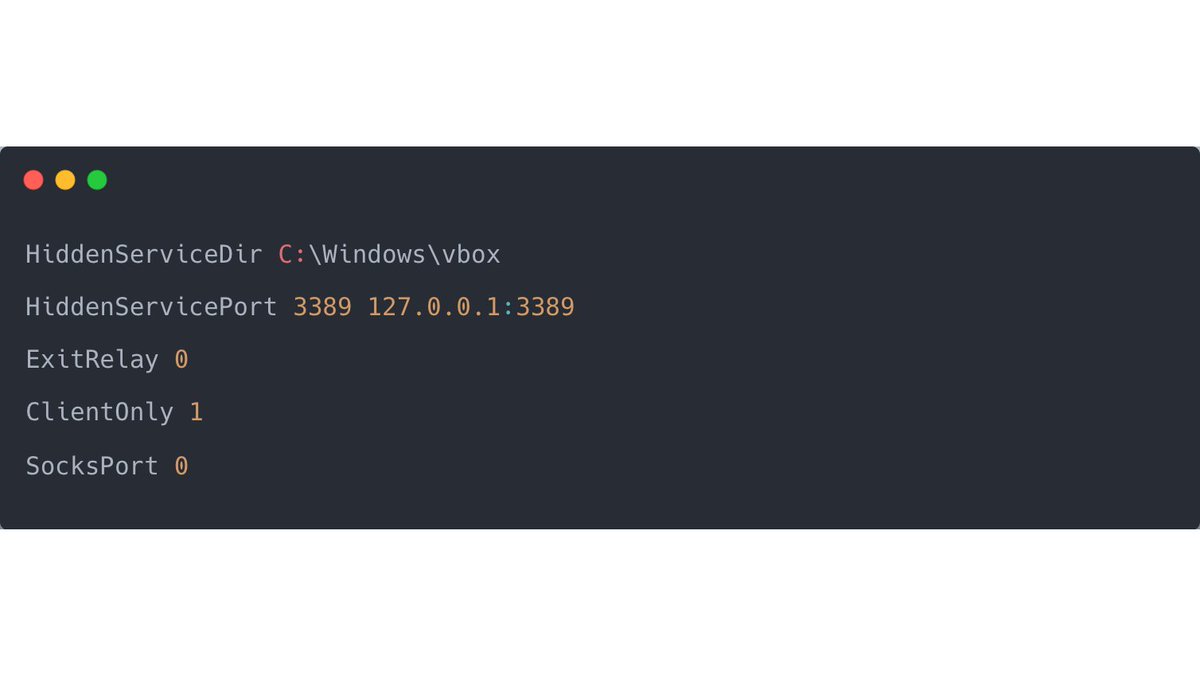
1/ Real-World #PingCastle Finding #13: Allow log on locally
➡️ Domain Users are eligible to log into DC's 🤯🙈
"When you grant an account the Allow logon locally right, you are allowing that account to log on locally to all domain controllers in the domain." [1]
#CyberSecurity
➡️ Domain Users are eligible to log into DC's 🤯🙈
"When you grant an account the Allow logon locally right, you are allowing that account to log on locally to all domain controllers in the domain." [1]
#CyberSecurity

2/ Why is this a bad idea?
"If you do not restrict this user right to legitimate users who must log on to the console of the computer, unauthorized users could download and run malicious software to elevate their privileges." [1]
"If you do not restrict this user right to legitimate users who must log on to the console of the computer, unauthorized users could download and run malicious software to elevate their privileges." [1]
3/ I encountered this finding several times in our AD assessments, so you better check your settings in your domain right now (better safe than sorry 🔒).
Good luck 🍀
Good luck 🍀
• • •
Missing some Tweet in this thread? You can try to
force a refresh