1/ The content below is from a file named install.bat and stems from a recent investigation where a TA launched this batch file. 👀
What's going on?
Well, VboxUpdate.exe is, in fact, tor.exe, and a new service is created, launching tor with a config file.
🧵 #CyberSecurity
What's going on?
Well, VboxUpdate.exe is, in fact, tor.exe, and a new service is created, launching tor with a config file.
🧵 #CyberSecurity

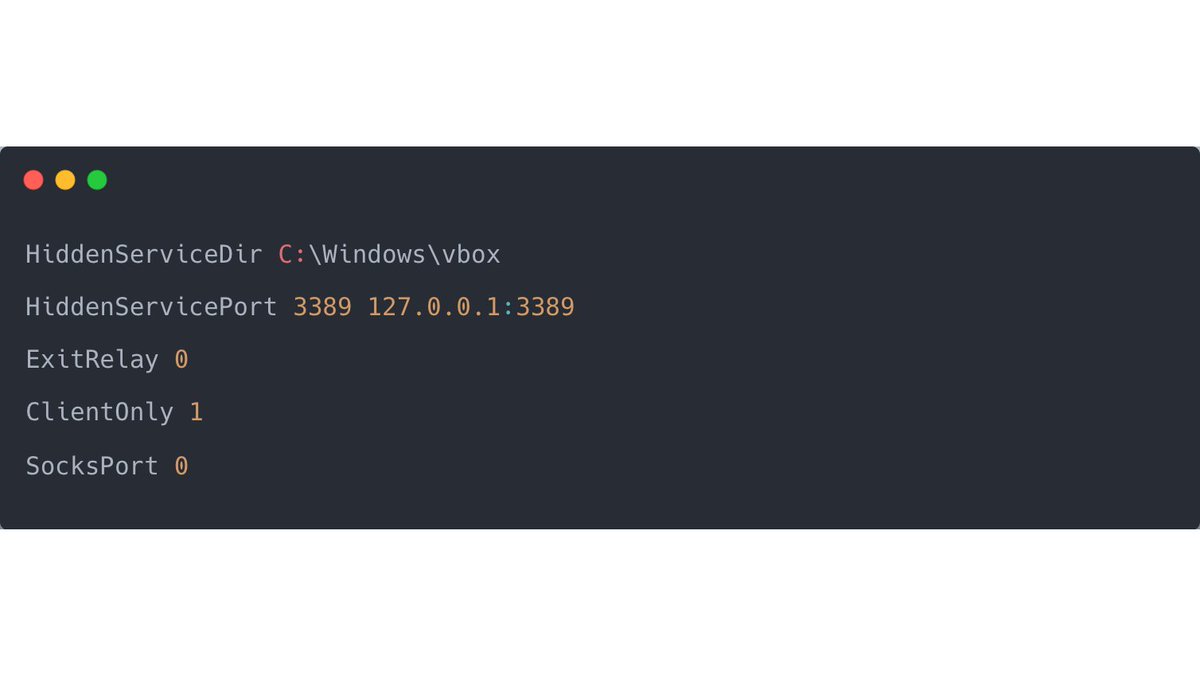
2/ Below is an excerpt from the content of config.txt; the configuration file passed as an argument to the tor service.
If you think this looks a lot like RDP Tunneling, you are absolutely right. 🥇
If you think this looks a lot like RDP Tunneling, you are absolutely right. 🥇
3/ Head over to the allthingsdfir blog to read a more profound write-up about the techniques used here and how they work together.
allthingsdfir.com/rdp-over-tor/
allthingsdfir.com/rdp-over-tor/
4/ What is nice from a #DFIR perspective is that inside the config.txt, there is a log file specified:
> C:\Windows\vbox\debug.log
> C:\Windows\vbox\debug.log
5/ Which logs the amount of data sent back and forth (or not, in our case). This could prove or disprove that a TA used that backdoor to enter or re-enter the network:
[notice] Heartbeat: Tor's uptime is 3 days 0:00 hours, with 0 circuits open I've sent 0 kB and received 0 kB
[notice] Heartbeat: Tor's uptime is 3 days 0:00 hours, with 0 circuits open I've sent 0 kB and received 0 kB
• • •
Missing some Tweet in this thread? You can try to
force a refresh