Last week I spoke at @journalismfest on how open-source intelligence is used to combat propaganda and uncover new information during Russia's war on Ukraine. Thank you for having me.
I promised to share a list of links to tools and sources. Here it is (I hope it helps) 👇
I promised to share a list of links to tools and sources. Here it is (I hope it helps) 👇

I often share digital investigation skills, cases and sources at events to help remotely answer core questions such as:
WHERE & WHEN did it happen?
WHAT happened?
WHO is responsible?
And HOW can it be visualised?
So let's start with the case studies.
WHERE & WHEN did it happen?
WHAT happened?
WHO is responsible?
And HOW can it be visualised?
So let's start with the case studies.
1: EyesonRussia.org - our community effort to document, verify and map Russia's invasion of Ukraine and share this info with the world.
Collaboration is key for this, from @Cen4infoRes @bellingcat @C4ADS incl volunteer groups @GeoConfirmed, GeoMouse and more.
Collaboration is key for this, from @Cen4infoRes @bellingcat @C4ADS incl volunteer groups @GeoConfirmed, GeoMouse and more.
2. Disinformation & Denial: Russia’s attempts to discredit open source evidence of Bucha.
The Russian Govt and its proxies tried to discredit important satellite imagery using public tools, but they were wrong. info-res.org/post/disinform…
The Russian Govt and its proxies tried to discredit important satellite imagery using public tools, but they were wrong. info-res.org/post/disinform…
3. Finding the Russian general who oversaw atrocities in Syria led cluster bomb attacks on civilians in Ukraine.
Our collab with @CNN identifying the general who oversaw cluster bomb attacks in Kharkiv. Big H/T to @GianlucaMezzo & @katie_polglase edition.cnn.com/2022/05/12/wor…
Our collab with @CNN identifying the general who oversaw cluster bomb attacks in Kharkiv. Big H/T to @GianlucaMezzo & @katie_polglase edition.cnn.com/2022/05/12/wor…
4. Killer Coordinates: How a Russian missile hit Kyiv with the help of online sleuths.
This piece was an OSINT community effort involving @amra_dorjbayar @ArchitMeta @AlbertoOlivie13 @brechtcastel @akhmxt @Techjournalisto & @GeoConfirmed info-res.org/post/killer-co…
This piece was an OSINT community effort involving @amra_dorjbayar @ArchitMeta @AlbertoOlivie13 @brechtcastel @akhmxt @Techjournalisto & @GeoConfirmed info-res.org/post/killer-co…
What are some data and tools that are helpful to use?
Here's a non-exhaustive list of a few OSINT tools, sources of data and specialists 👇
Here's a non-exhaustive list of a few OSINT tools, sources of data and specialists 👇
1. @ACLEDINFO - disaggregated data collection, analysis, and crisis mapping project. acleddata.com
Great for mapping media reports of specific instances, trends, statistics and a general geographical awareness. Especially useful when combined with other datasets.
Great for mapping media reports of specific instances, trends, statistics and a general geographical awareness. Especially useful when combined with other datasets.
2. The @bellingcat autoarchiver - automatically archives social media posts, videos, and images from a Google Sheets document. github.com/bellingcat/aut…
This has enabled us to easily archive thousands of grim videos and photos that could be used by researchers in the future.
This has enabled us to easily archive thousands of grim videos and photos that could be used by researchers in the future.
3. Telegram export channel history - automatically export an entire channel in Telegram, choose date, file types. Available in the Telegram desktop.
Very helpful if you don't want to flick through traumatic imagery. You can also convert the chat file into a spreadsheet.

Very helpful if you don't want to flick through traumatic imagery. You can also convert the chat file into a spreadsheet.


4. @oryxspioenkop tracker of military vehicles during Russia's invasion of Ukraine.
Great to see #OSINT work like this getting recognition, even from @DefenceHQ. oryxspioenkop.com/2022/02/attack…
Great to see #OSINT work like this getting recognition, even from @DefenceHQ. oryxspioenkop.com/2022/02/attack…
5. @flightradar24 - shows real-time aircraft flight tracking information on a map. flightradar24.com
Hit up @Gerjon_ for help on flights.
Hit up @Gerjon_ for help on flights.

6. @MarineTraffic - maritime analytics provider, providing real-time info on the current location and movements of ships. marinetraffic.com
Hit up @YorukIsik for anything that floats.
Hit up @YorukIsik for anything that floats.

7. Overpass Turbo - web based data mining tool for OpenStreetMap. overpass-turbo.eu
(Image below is a map of power plants/stations made with Overpass Turbo)
(Image below is a map of power plants/stations made with Overpass Turbo)

8. Map of Russian fortifications - the map shows Russia’s field fortifications in (and around) Ukraine as viewed via satellite imagery. (by @bradyafr)
google.com/maps/d/u/0/vie…
read.bradyafrick.com/p/russian-fiel…
google.com/maps/d/u/0/vie…
read.bradyafrick.com/p/russian-fiel…
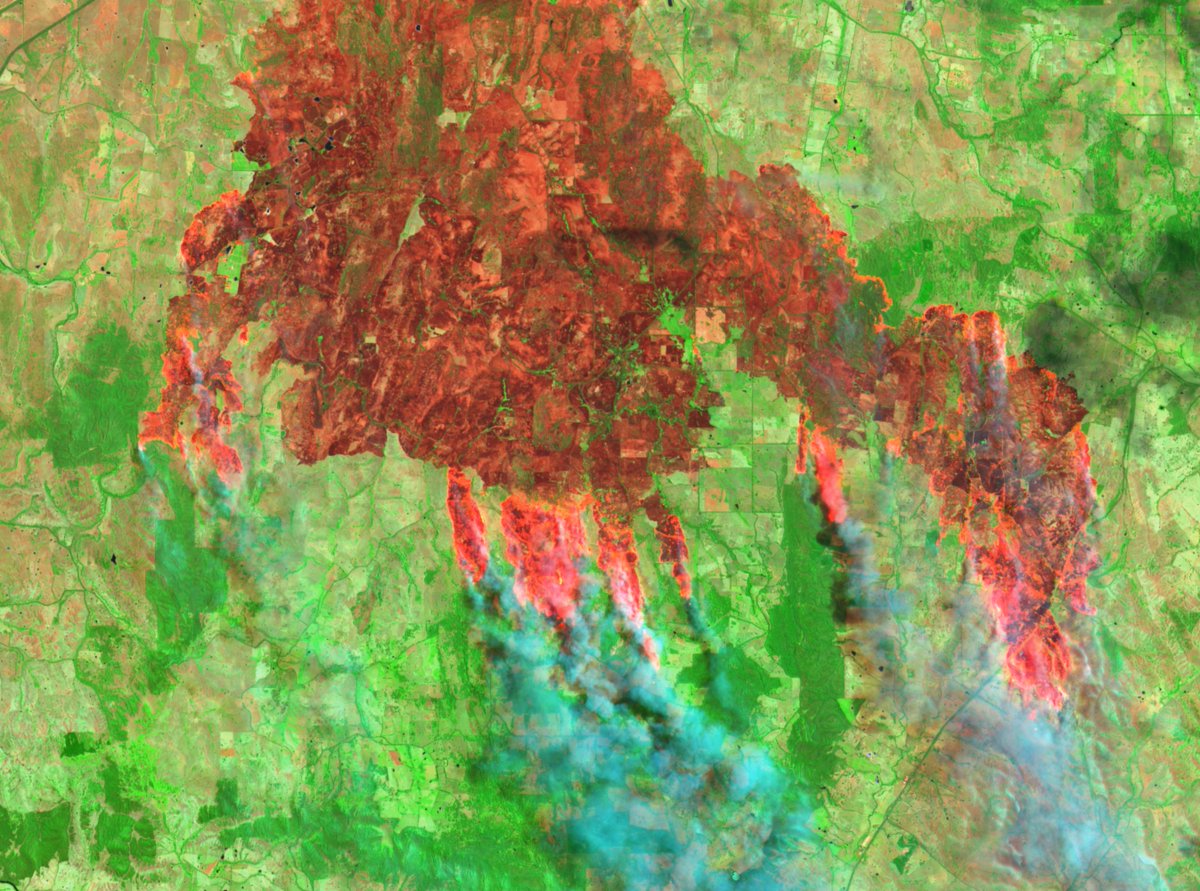
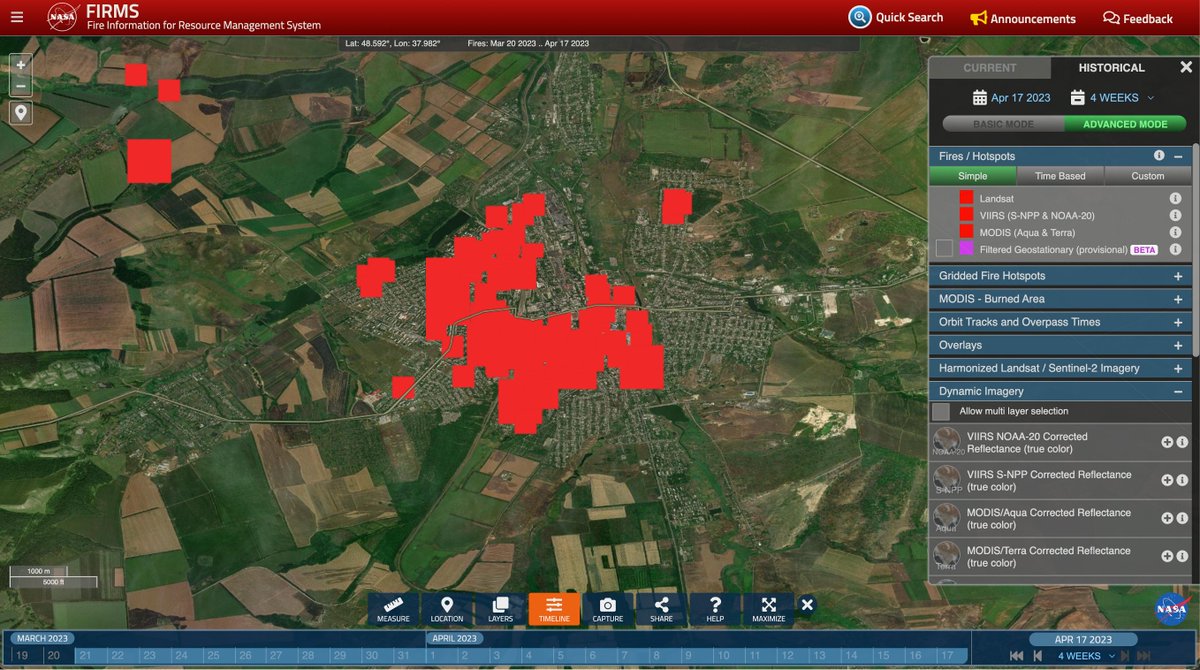
9. NASA FIRMS - near real-time active fire data. This tool has been core to work across Ukraine, Myanmar, Sudan, Ethiopia and many others.
firms.modaps.eosdis.nasa.gov/map
firms.modaps.eosdis.nasa.gov/map
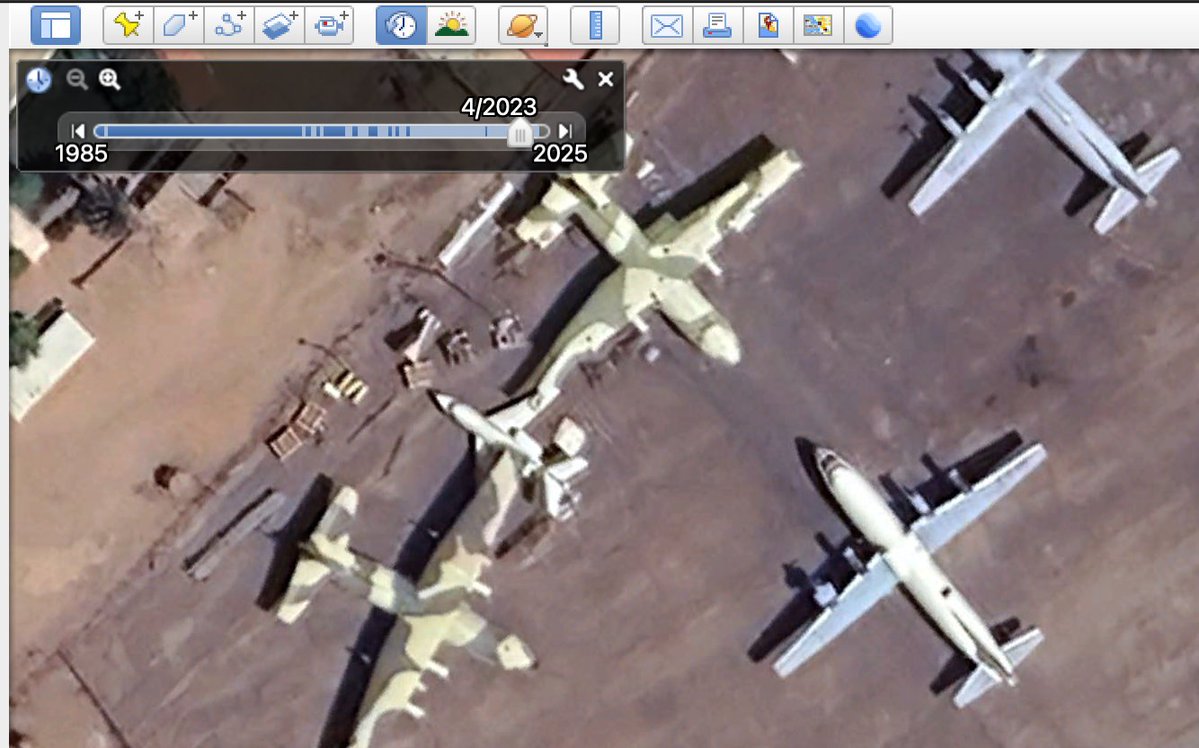
10. @googleearth (desktop) - program using 3D representation of Earth based primarily on satellite imagery. google.com/intl/en_uk/ear…
Here's a video on five useful cool features: . Example below is a geolocation from Mariupol using Google Earth

Here's a video on five useful cool features: . Example below is a geolocation from Mariupol using Google Earth


11. @sentinel_hub - a platform to browse, query and analyse satellite data. apps.sentinel-hub.com/sentinel-playg…
Example below is smoke rising from Mariupol, with banding to bring out active fires.
Example below is smoke rising from Mariupol, with banding to bring out active fires.

12. Pinpoint by Google - research tool to help journalists and academics explore and analyse large collections of documents. journaliststudio.google.com/pinpoint/about
Very useful to dump a heap of PDFs in there, it then scrapes them for words, and lists names, organisations and more.
Very useful to dump a heap of PDFs in there, it then scrapes them for words, and lists names, organisations and more.
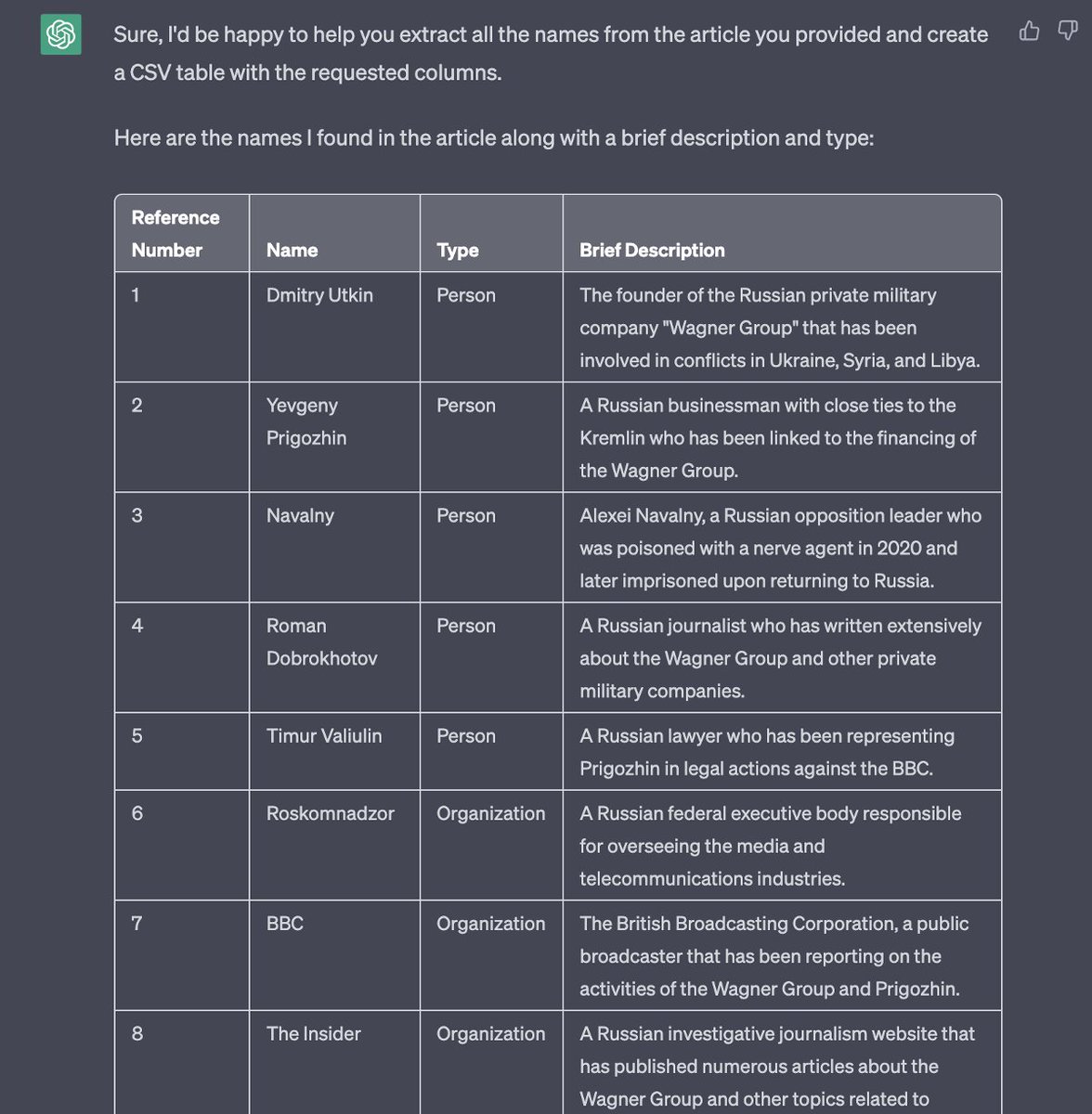
13. @OpenAI ChatGPT - chatbot trained to follow instructions and provide a detailed response. chat.openai.com
Great prompt from @TomTomjarvis (text in alt) to extract names and entities from a report into a csv.
Don't use this as a fact-finder, but as an assistant.

Great prompt from @TomTomjarvis (text in alt) to extract names and entities from a report into a csv.
Don't use this as a fact-finder, but as an assistant.
You can watch the full session of the presentation from Perugia, Italy at the @journalismfest #ijf23 here: journalismfestival.com/programme/2023….
You can also find tutorials on digital investigative skills on my YouTube: youtube.com/@Bendobrown
You can also find tutorials on digital investigative skills on my YouTube: youtube.com/@Bendobrown
For satellite and remote sensing nerds, @wammezz and @oballinger did a great of a session at @journalismfest showcasing remote sensing in environmental cases. journalismfestival.com/programme/2023…
The session includes a helpful remote sensing OSINT guide: bellingcat.github.io/RS4OSINT/
The session includes a helpful remote sensing OSINT guide: bellingcat.github.io/RS4OSINT/

Two other great sessions involving remote sensing at @journalismfest were from @AI_Micah on satellite imagery for crisis reporting (journalismfestival.com/programme/2023…), & environmental geospatial forensic work with Kuek Ser Kuang Keng @nandawenzel @gufalei (journalismfestival.com/programme/2023…) 

• • •
Missing some Tweet in this thread? You can try to
force a refresh