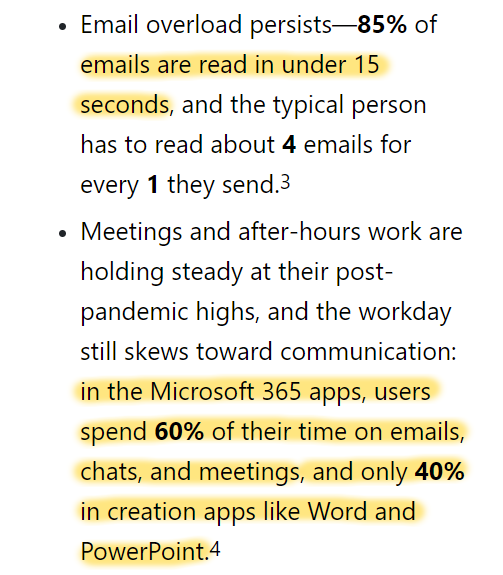
NEW: "Surveillance and Algorithmic Control in the Call Center", a case study on contact center software and automated management.
It explores technologies that are used to monitor, rate, rank and micromanage workers in call centers and similar workplaces:
crackedlabs.org/en/data-work/p…

It explores technologies that are used to monitor, rate, rank and micromanage workers in call centers and similar workplaces:
crackedlabs.org/en/data-work/p…


This case study is part of a larger project led by Cracked Labs, which examines and maps how companies use personal data on (and against) workers in Europe, together with @algorithmwatch, @JeremiasPrassl, @UNI_Europa and others, funded by @Arbeiterkammer:
crackedlabs.org/en/data-work
crackedlabs.org/en/data-work
The work environment pioneered in the call center, which involves extensive monitoring and performance control, has spread into many areas, from helpdesk services to debt collection to remote nursing, from outsourced back-office work to content moderation to 'AI' data labeling.
The case study makes two contributions:
- It summarizes research on how call centers actually use monitoring and algorithmic control, with a focus on Europe
- It examines software that is available on the market, based on an analysis of technical documentation and other sources
- It summarizes research on how call centers actually use monitoring and algorithmic control, with a focus on Europe
- It examines software that is available on the market, based on an analysis of technical documentation and other sources
The investigation focuses on contact center systems provided by the leading vendor Genesys, whose software is used to manage and monitor 720,000 workers, according to the company. It also documents data practices from other firms like NICE, Verint, Amazon, Cogito and Callminer. 

I went through several thousand pages of software documentation. The findings show that today’s contact center systems offer a wide range of mechanisms to structure, direct, monitor and control work down to the second.
1) Performance metrics, targets and rankings are ubiquitous.
1) Performance metrics, targets and rankings are ubiquitous.

Dashboards, reports and alerts help to identify “outliers” and appoint coaching sessions.
This is how the Genesys system can show real-time performance metrics like the 'average handling time' directly to workers, putting them in relation to defined targets (green, yellow, red).
This is how the Genesys system can show real-time performance metrics like the 'average handling time' directly to workers, putting them in relation to defined targets (green, yellow, red).

Other performance control mechanisms that exploit peer pressure to intensify work include 'wallboards', which show metrics to the whole team in the office.
Here's an example wallboard from a Slovakian firm that displays individual-level metrics and can be 'plugged' into Genesys.
Here's an example wallboard from a Slovakian firm that displays individual-level metrics and can be 'plugged' into Genesys.

Genesys also offers a system that obligates workers to collect “points” throughout the day by hitting targets and behaving as desired, and to compete with others, turning the call center into a Black Mirror episode.
Genesys on its website: “competition is a natural motivator”
Genesys on its website: “competition is a natural motivator”

NICE, another leading contact center software vendor, which originally sold surveillance tech to the military sector, offers a system to 'automate incentive compensation', i.e. performance-based pay.
Workers see how hitting/missing performance targets will affect their salary.
Workers see how hitting/missing performance targets will affect their salary.

2) The concept of the “queue” creates a virtual assembly line with the constant need for immediate action.
Genesys provides many mechanisms to automatically prioritize and assign interactions (calls, emails, chats etc) and other tasks (e.g. loan application handling) to workers.
Genesys provides many mechanisms to automatically prioritize and assign interactions (calls, emails, chats etc) and other tasks (e.g. loan application handling) to workers.
Automated call and task allocation can be used to maximize efficiency and minimize the workers' idle time.
Managers can define key performance indicators that determine how quickly calls and other tasks are assigned to workers based on their skill profiles and past behavior.
Managers can define key performance indicators that determine how quickly calls and other tasks are assigned to workers based on their skill profiles and past behavior.
Notifications and timers can act as virtual whips.
e.g. Genesys provides call centers with a timer shown to workers that counts down the available seconds for 'after-call work'. If they don't finish on time, the system may set their 'status' to 'not ready' and raise an alert.
e.g. Genesys provides call centers with a timer shown to workers that counts down the available seconds for 'after-call work'. If they don't finish on time, the system may set their 'status' to 'not ready' and raise an alert.
Workers may have to get in line with rigid scripts and other workflow automation mechanisms that tell them what to say, what to look up and what to enter into forms in different stages of a call.
Or they have to step in when IVR systems, voicebots and chatbots demand it.
Or they have to step in when IVR systems, voicebots and chatbots demand it.
3) Genesys allows call centers to fully monitor and record calls, other communication contents and screen activities - in the name of training, quality assurance, customer satisfaction and compliance.
Managing “quality” and customer satisfaction may turn into behavioral control.
Managing “quality” and customer satisfaction may turn into behavioral control.

Genesys' software can automatically analyze and assess, second by second, what call center workers say, which phrases they use and whether they are associated with a "positive" or "negative" sentiment.
Added together resulting in a sentiment score for each call or conversation.
Added together resulting in a sentiment score for each call or conversation.

Supervisors or quality managers may assess call center agents and their work on an ongoing basis.
They single out calls and other 'interactions' and evaluate them, which may include listening to calls or rely on sentiment scores, and can then result in 'agent quality' scores.
They single out calls and other 'interactions' and evaluate them, which may include listening to calls or rely on sentiment scores, and can then result in 'agent quality' scores.

As detailed in section 2.3 in the case study, Genesys presents a wild mix of promises and purposes with respect to communication monitoring and analysis #purposelimitation
Genesys also emphasizes that supervisors can listen to a workers’s calls without the worker being aware.
Genesys also emphasizes that supervisors can listen to a workers’s calls without the worker being aware.

Genesys also provides software that combines training with skills assessment and performance control.
The 'Performance DNA' module helps call centers to rate and score workers for their 'friendliness', 'tone of voice' and 'call metrics' based on online tests and monitoring data.
The 'Performance DNA' module helps call centers to rate and score workers for their 'friendliness', 'tone of voice' and 'call metrics' based on online tests and monitoring data.

Other vendors provide even more intrusive stuff.
Cogito, a system that can be plugged into Genesys software, claims to measure 'emotional state' in a call, communicates the detected emotions to workers in real-time and instructs them on how to change their speaking style.
Cogito, a system that can be plugged into Genesys software, claims to measure 'emotional state' in a call, communicates the detected emotions to workers in real-time and instructs them on how to change their speaking style.

Cogito claims that its scores are 'objective' measures 🙄
And it states that, as it would not be easy to “make an emotional connection with customers ... on demand”, it aims to help call center agents improve empathy in an automated way by “implementing empathy at scale” 🙄
And it states that, as it would not be easy to “make an emotional connection with customers ... on demand”, it aims to help call center agents improve empathy in an automated way by “implementing empathy at scale” 🙄
Callminer, another speech analytics firm, also promises to extract information about emotions and behaviors from calls, and to calculate “objective” scores that assess, for example, “effort”, “emotion” and “customer satisfaction”. It also instructs agents to e.g. "show empathy". 

Callminer can be plugged into Genesys.
Its early investors include the CIA's venture capital firm In-Q-Tel, which stated that it has "tapped Callminer's expertise" to "serve in the United States national security interest".
Call center monitoring technology is often dual-use.
Its early investors include the CIA's venture capital firm In-Q-Tel, which stated that it has "tapped Callminer's expertise" to "serve in the United States national security interest".
Call center monitoring technology is often dual-use.

This is also true for Verint, which provides contact center tech including speech analytics, performance monitoring and scheduling. Also, Verint has supplied phone surveillance tech to the NSA, as reported in 2013.
(in 2021, Verint spun off its defense business into a new firm)
(in 2021, Verint spun off its defense business into a new firm)

Yet other vendors sell invasive surveillance technologies targeted specifically at those who work from home.
Trendzact uses webcams for worker monitoring and automatically flags behavioral anomalies (left). The UK company Asterlogic records keyboard and mouse activity (right).
Trendzact uses webcams for worker monitoring and automatically flags behavioral anomalies (left). The UK company Asterlogic records keyboard and mouse activity (right).

Both systems can be plugged into Genesys, i.e. installed via the company's "app store".
In a Sept 2020 blog, Genesys promoted Trendzact's workspace monitoring system as a "nontraditional employee monitoring tool" for tracking both “productivity and compliance of at-home agents”.
In a Sept 2020 blog, Genesys promoted Trendzact's workspace monitoring system as a "nontraditional employee monitoring tool" for tracking both “productivity and compliance of at-home agents”.

4) In addition to software that micromanages calls and other tasks down to the level of the phrases mentioned in conversations, Genesys offers functionality for 'workforce planning' and automated shift scheduling - to get the maximum out of a minimum number of flexible workers.
Genesys can automatically schedule shifts, breaks and assignments to particular work activities throughout the day (e.g. responding to calls, working on task queues).
While the system can be configured to create "regular, fixed" schedules, it appears to focus on flexible shifts.
While the system can be configured to create "regular, fixed" schedules, it appears to focus on flexible shifts.
The system can automatically distribute breaks and meals across the working day based on predefined constraints. If the algorithm cannot schedule certain breaks or meals, it may skip them, “relax" the constraints or generate a warning.
Call centers can turn off these warnings.
Call centers can turn off these warnings.

Automated "intraday reschedules" may change start and end times for shifts, meals, breaks and work activities.
Genesys states it may not be "practical to re-optimize the current hour" because changes to meals and breaks “might be difficult to communicate to the affected agents”.
Genesys states it may not be "practical to re-optimize the current hour" because changes to meals and breaks “might be difficult to communicate to the affected agents”.

Generally, schedules are generated in a way that “closely matches requirements with as few paid hours as possible", according to Genesys, which also suggests that “unneeded agents can be sent home if you are overstaffed, or extra agents can be called in if you are understaffed”. 

Scheduling is based on "forecasting" mechanisms.
Genesys can predict future workload in relation to desired KPI objectives and based on historical data on work activities. These forecasts can directly affect performance targets, work intensity and schedule stability for agents.
Genesys can predict future workload in relation to desired KPI objectives and based on historical data on work activities. These forecasts can directly affect performance targets, work intensity and schedule stability for agents.
If e.g. the forecasted interaction volume is too high, the call center could either hire additional agents, reduce the 'handle time' target to speed up the virtual assembly line or increase the 'agent occupancy' metric to minimize any remaining 'idle' time between calls or tasks. 

Genesys emphasizes that "overstaffing" could cost "hundreds of thousands to millions" and promises to help call centers to "develop highly efficient just-in-time hiring" so they "know precisely when, where and how many agents to hire—and when to offer unpaid leave or overtime". 

Genesys’ scheduling system can reward higher-rated workers with the ability to choose more desirable shifts or vacation days.
Its shift trading system can, to the extent agents feel a mutual responsibility to take shifts, be considered a mechanism that exploits peer control.

Its shift trading system can, to the extent agents feel a mutual responsibility to take shifts, be considered a mechanism that exploits peer control.


Genesys and the other examined vendors were selected as illustrative examples of wider practices.
While the 'customer success stories' on the Genesys site suggest that many of these functionalities are in use in Europe, the details of how employers deploy them remains unclear.
While the 'customer success stories' on the Genesys site suggest that many of these functionalities are in use in Europe, the details of how employers deploy them remains unclear.
The findings demonstrate that the design of these systems can shape how they are used by employers and thus how they affect the daily lives of workers.
Default settings and recommendations laid out in the software documentation can also have an impact on how employers use them.
Default settings and recommendations laid out in the software documentation can also have an impact on how employers use them.
While a legal assessment of the examined data practices is beyond the scope of this case study, data protection issues are briefly discussed in section 5.6.
The study's findings will be incorporated in the main report of the ongoing project, which will draw further conclusions.
The study's findings will be incorporated in the main report of the ongoing project, which will draw further conclusions.
Section 8 in my case study summarizes surveys and field reports on the actual use of monitoring and algorithmic control in call centers, with a focus on Europe. It also addresses how workers are affected + the complementary role of low wages, short-term contracts and outsourcing. 



• • •
Missing some Tweet in this thread? You can try to
force a refresh