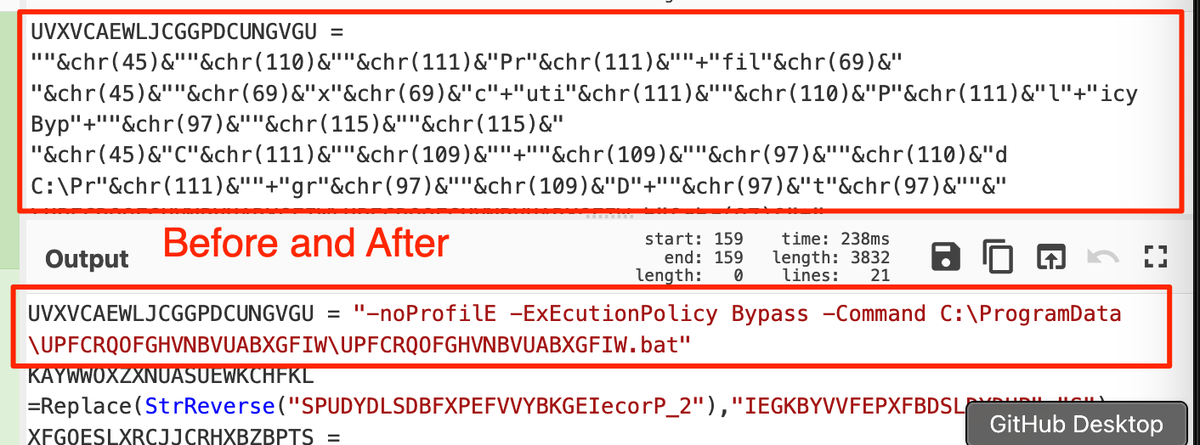
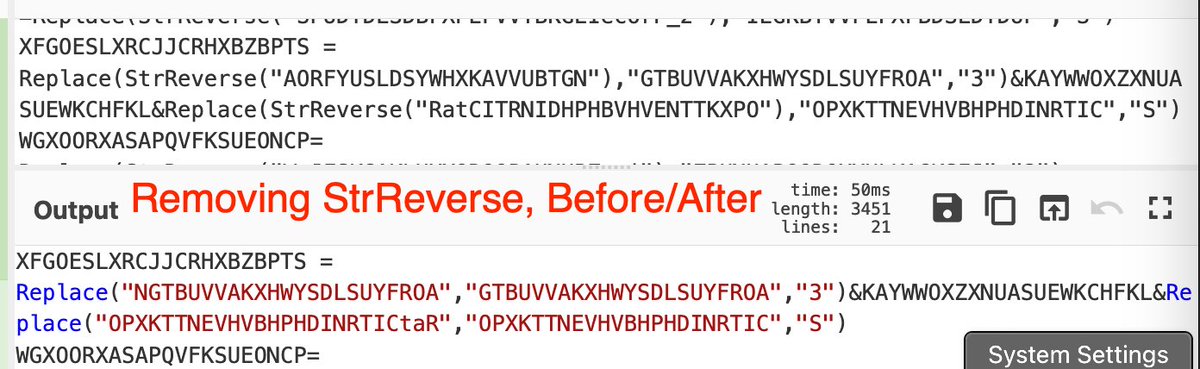
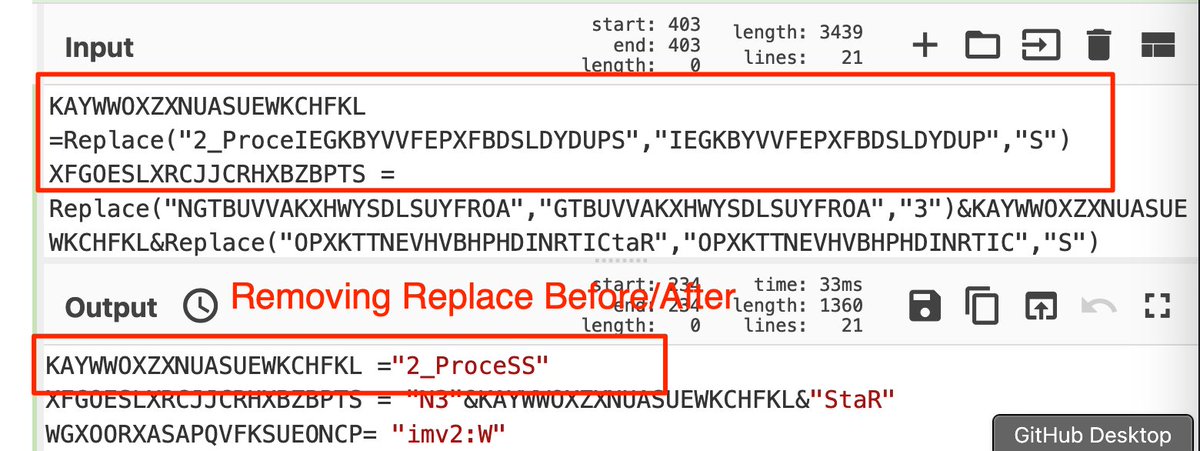
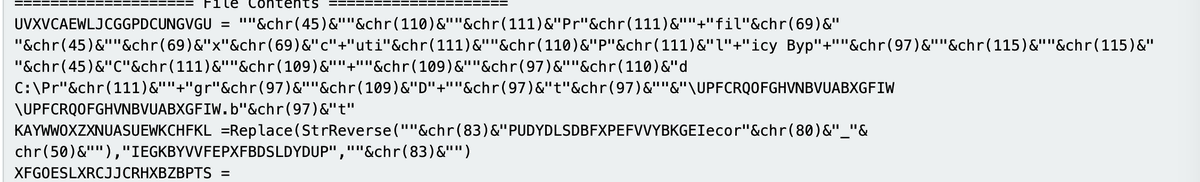
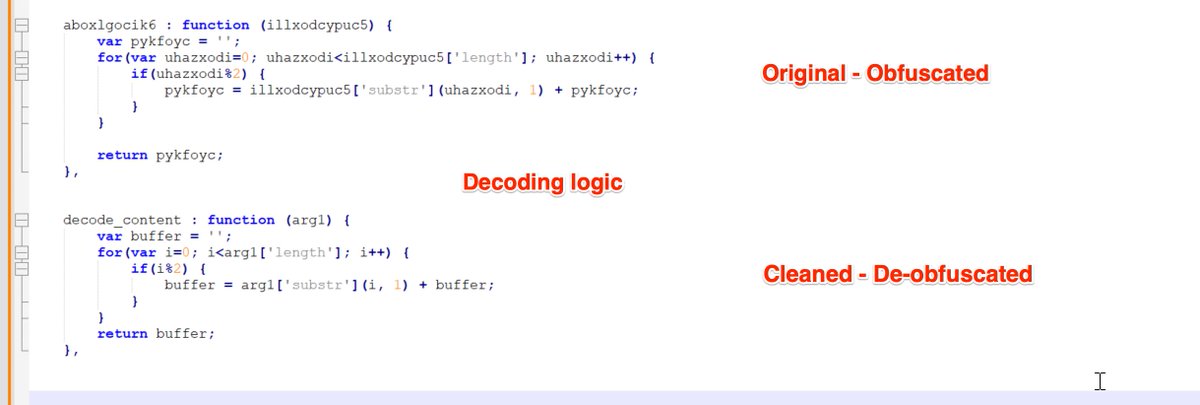
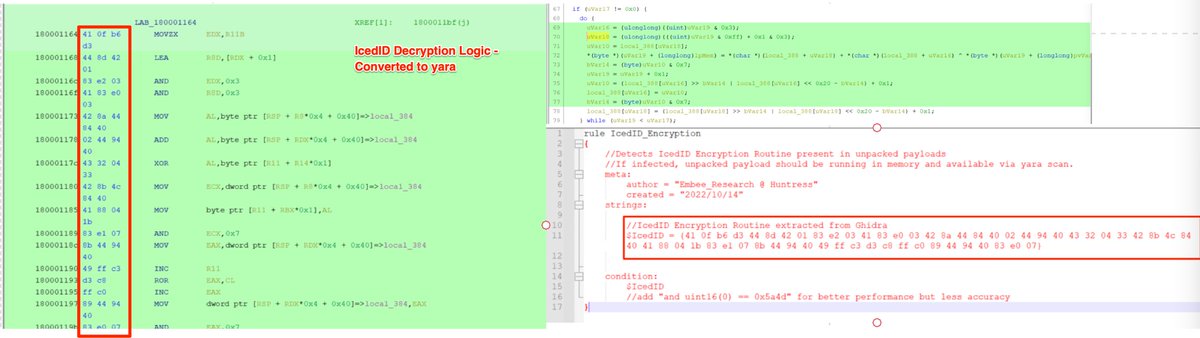
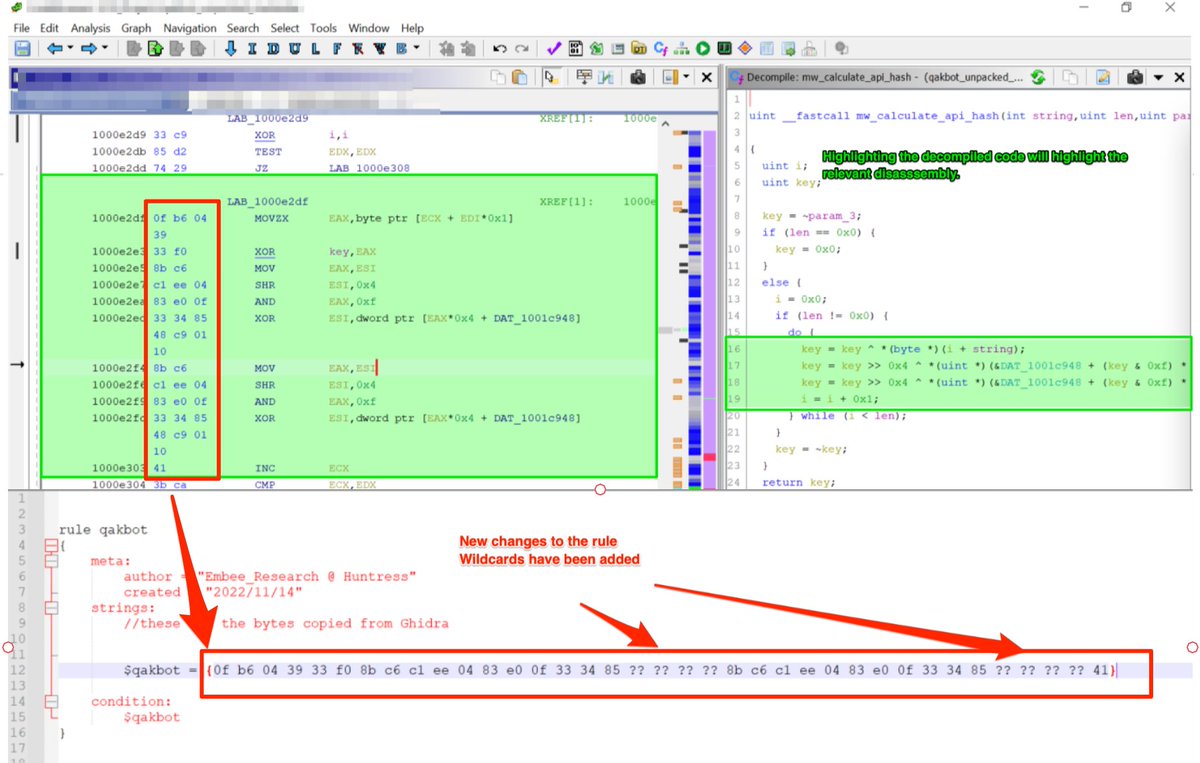
🚨Malware Tips 🚨 - Resolving API Hashes Using Conditional Breakpoints.
By adding breakpoints and log conditions to a function that resolves api hashes, it's possible to quickly resolve api hashes in bulk.
Thread
[1/11] 👇
#Malware #AgentTesla #Ghidra #Debugging


By adding breakpoints and log conditions to a function that resolves api hashes, it's possible to quickly resolve api hashes in bulk.
Thread
[1/11] 👇
#Malware #AgentTesla #Ghidra #Debugging


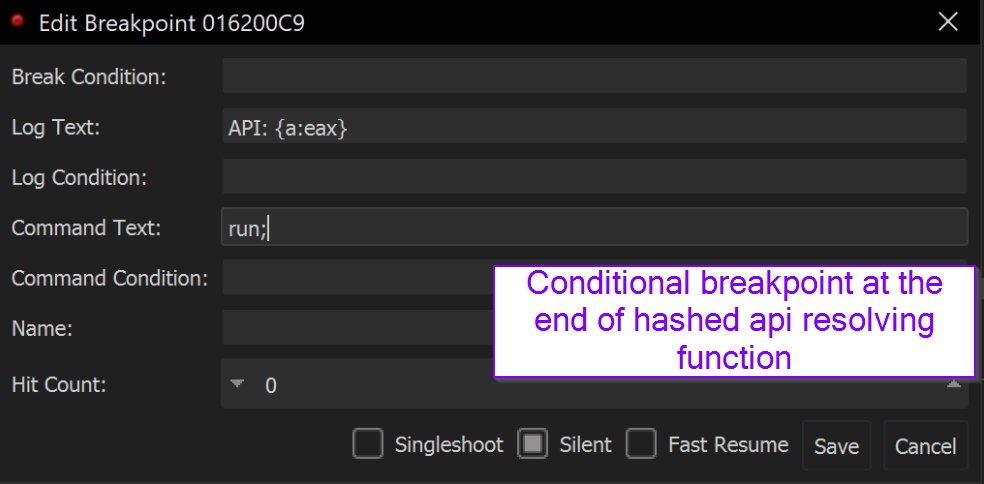
[1.1/11]
Link to original sample: bazaar.abuse.ch/sample/7512be2…
Link to Full Blog: embee-research.ghost.io/agenttesla-ful…
Link to original sample: bazaar.abuse.ch/sample/7512be2…
Link to Full Blog: embee-research.ghost.io/agenttesla-ful…
[2/11] You first need to locate a function that resolves api hashes.
An example can be seen here - A giveaway is the same function is repeatedly called with hash-like values. An extra telltale sign is that each return value is cast as code (code *).
An example can be seen here - A giveaway is the same function is repeatedly called with hash-like values. An extra telltale sign is that each return value is cast as code (code *).

[3/11] Once you've identified the function responsible. Two breakpoints need to be created.
1. At the start of the function where the hash value is easily accessible and typically on the stack
2. At the end of the function, where the resolved api is returned in eax.
1. At the start of the function where the hash value is easily accessible and typically on the stack
2. At the end of the function, where the resolved api is returned in eax.
[4/11] The first breakpoint needs to be set at the start of the api resolving function. In my sample of AgentTesla - this was at <base> + 0x73.
At this same point - the hash value was present in the second argument (located at [esp+8])

At this same point - the hash value was present in the second argument (located at [esp+8])


[5/11] Using this information, you can create a breakpoint on the api resolving function (<base> + 0x73)
This breakpoint will log the hash value at [esp+8].
After logging the hash value, the malware will continue to execute (run;)

This breakpoint will log the hash value at [esp+8].
After logging the hash value, the malware will continue to execute (run;)


[6/11] To make this interesting - a second breakpoint should be set at the end of the api resolving function.
In my case - this was at <base> + 0xc9.
At the end of the function - the resolved api is stored within EAX.
In my case - this was at <base> + 0xc9.
At the end of the function - the resolved api is stored within EAX.

[7/11] With this knowledge - a second conditional breakpoint can be created at the end of the function (<base> + 0xc9).
This time - address info (containing the api name) will be printed to the log each time the function completes.

This time - address info (containing the api name) will be printed to the log each time the function completes.


[8/11] Combining the two conditional breakpoints - all hashes and their decoded values will be written to the log window as the malware executes. 

[10/11] Alternatively - An extra command of "bp eax" can be added to the command text. This will automatically create breakpoints on any api resolved via hashing.
This can be used to continue analysis via a debugger, and automatically break on suspicious functions.
This can be used to continue analysis via a debugger, and automatically break on suspicious functions.

[11/11] This analysis originated from recent blog I published. Here I cover a wide range of skills and tools required to completely unpack and analyse an AgentTesla loader.
embee-research.ghost.io/agenttesla-ful…
embee-research.ghost.io/agenttesla-ful…
• • •
Missing some Tweet in this thread? You can try to
force a refresh

 Read on Twitter
Read on Twitter